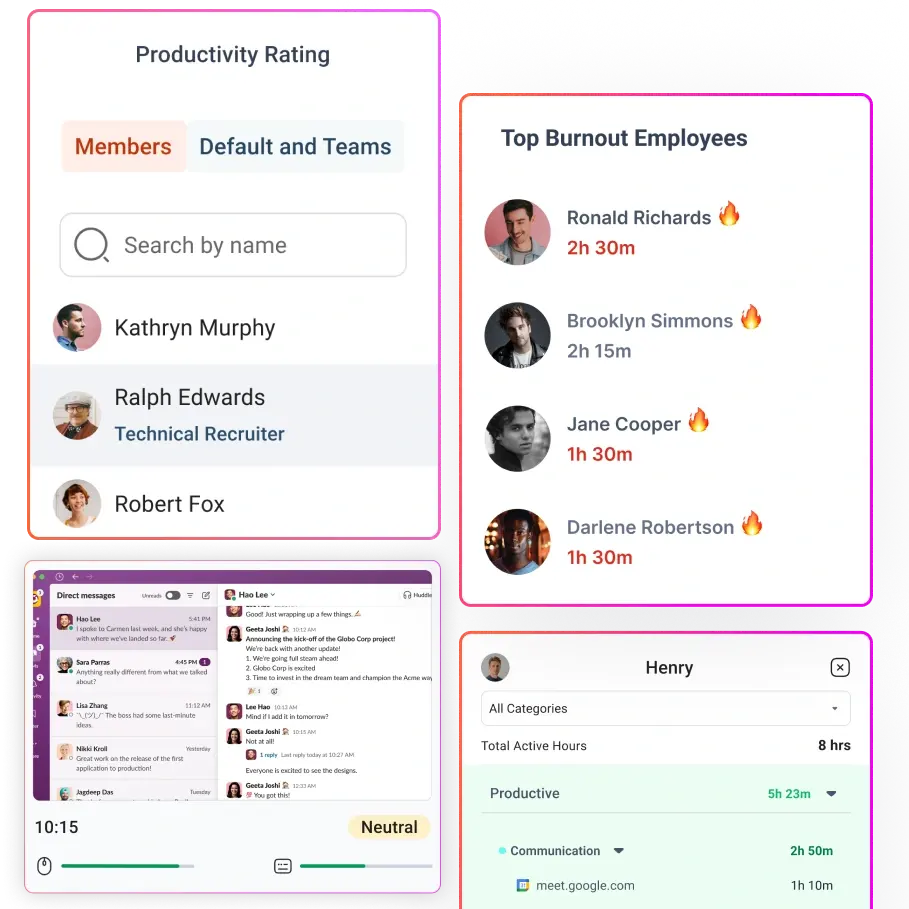
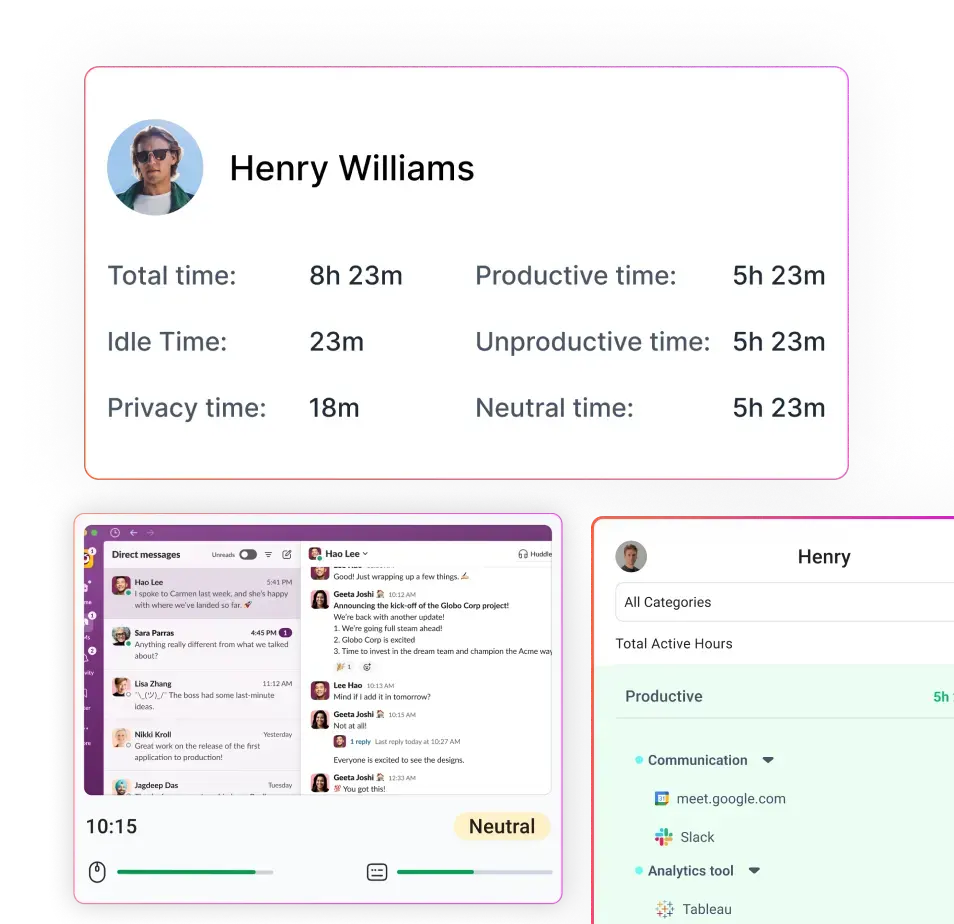
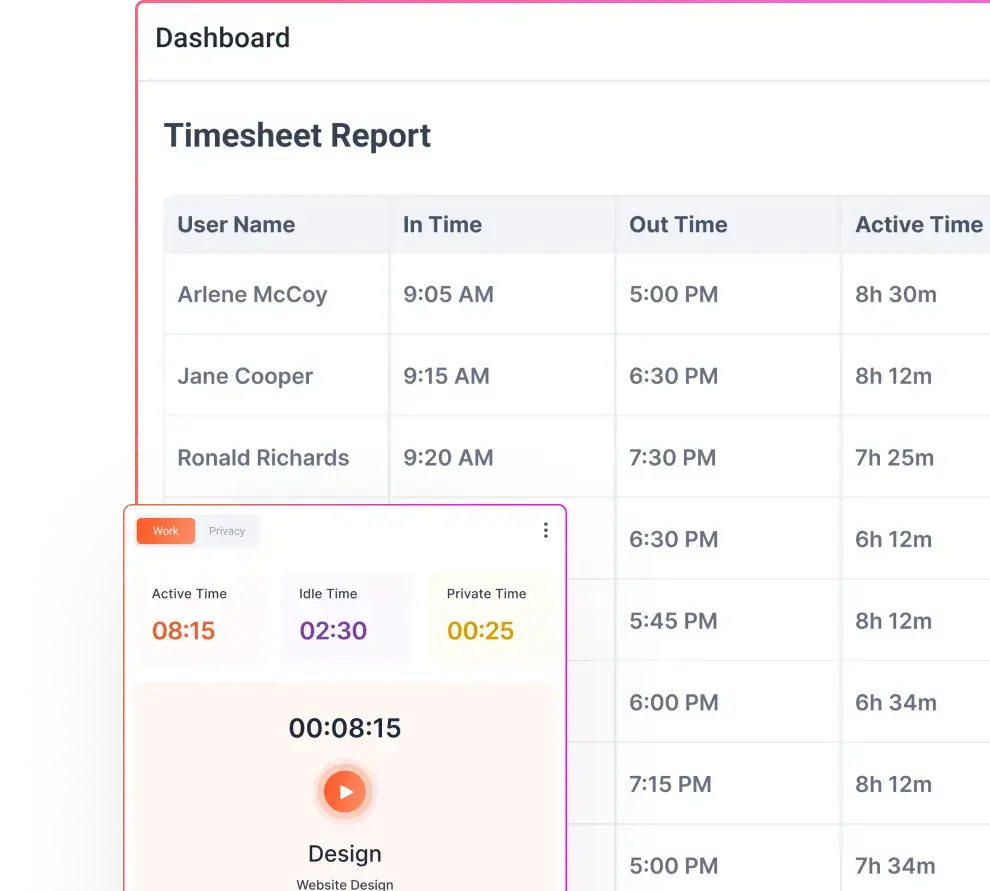
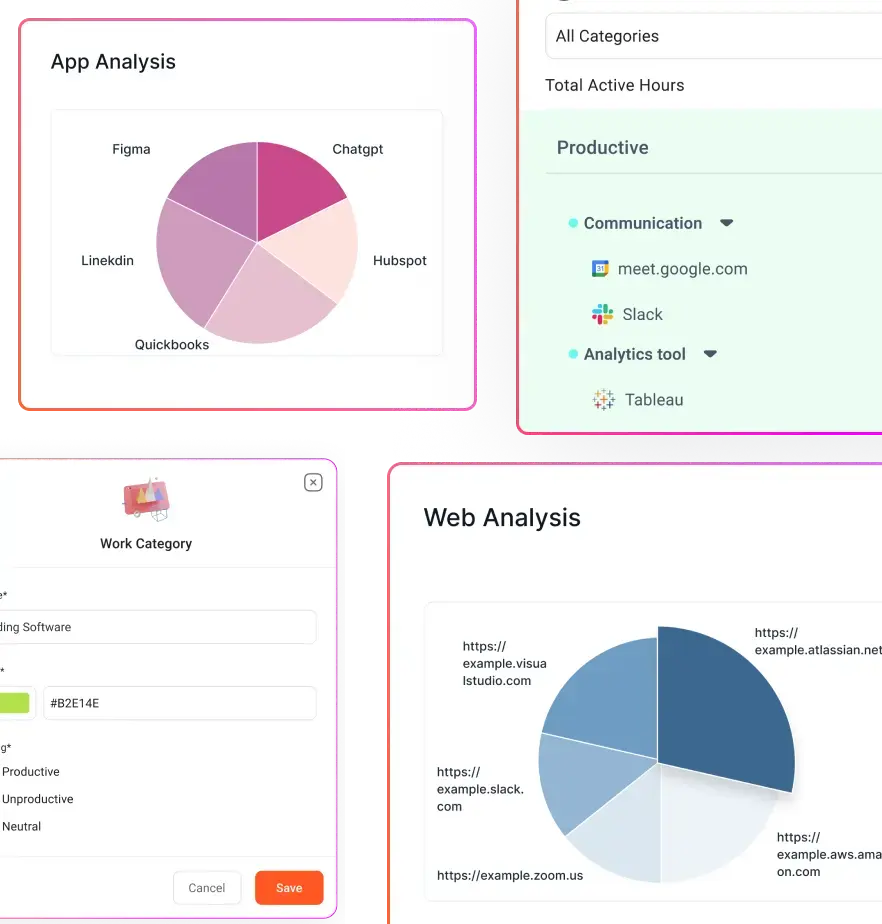
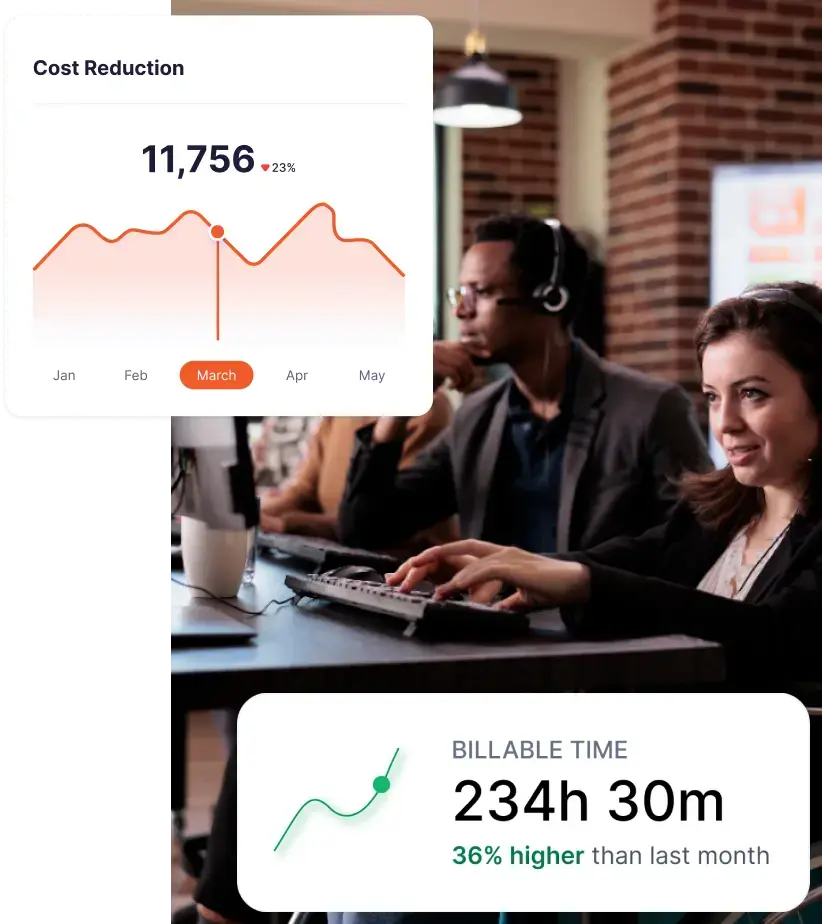
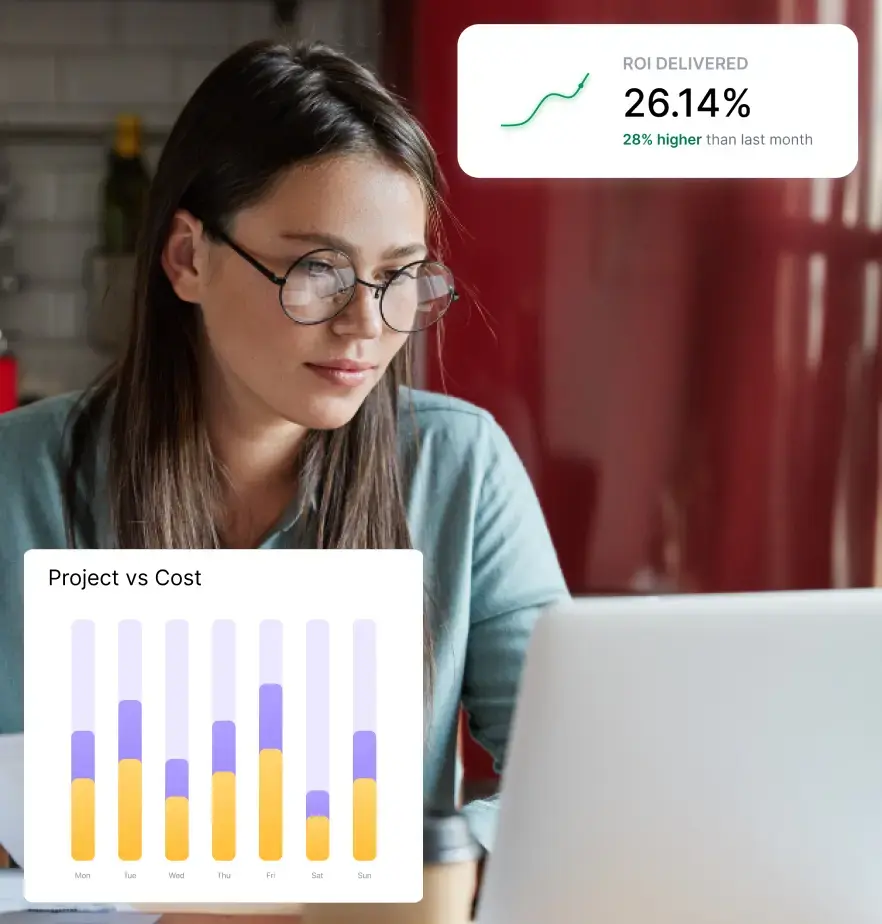
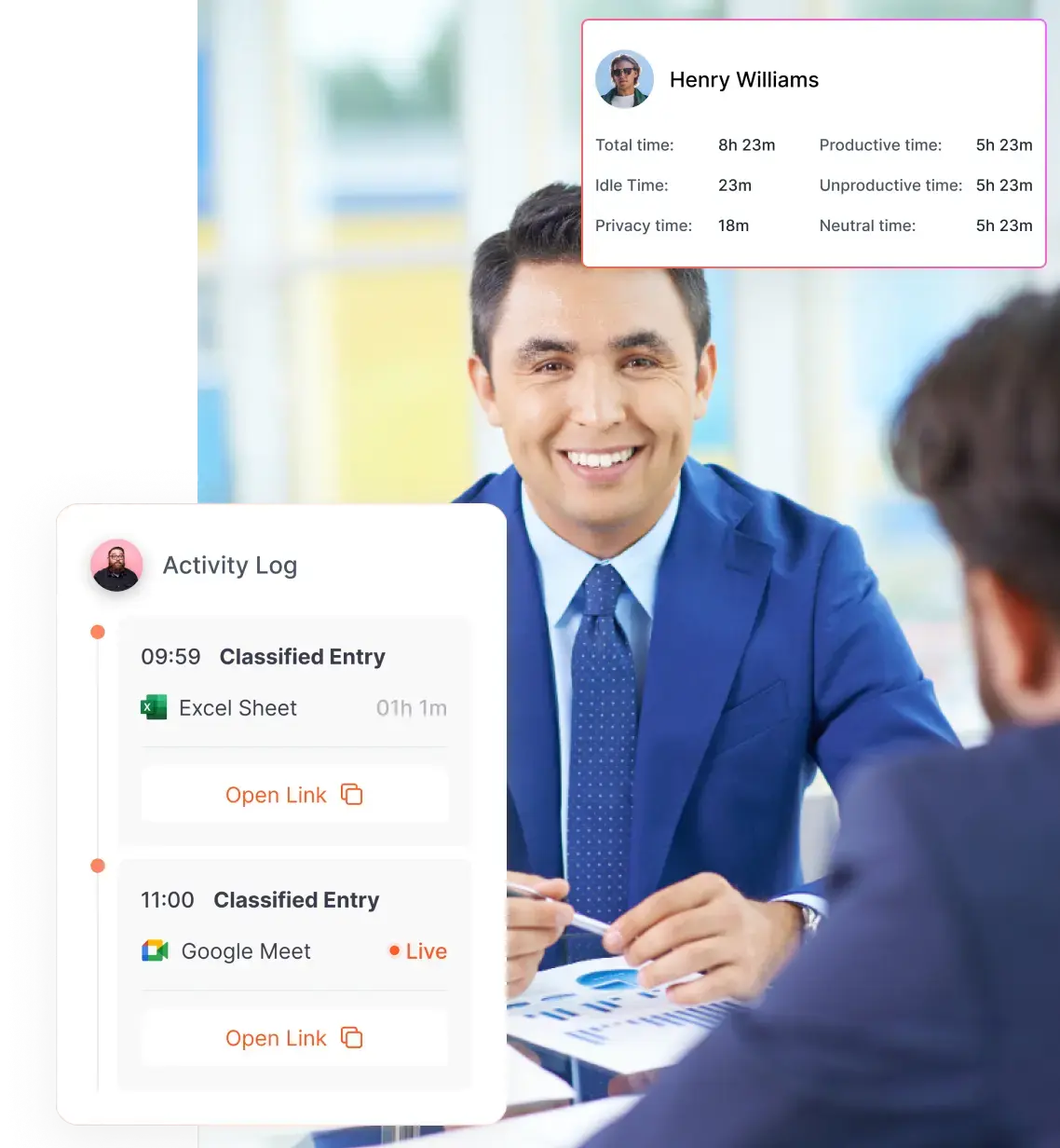
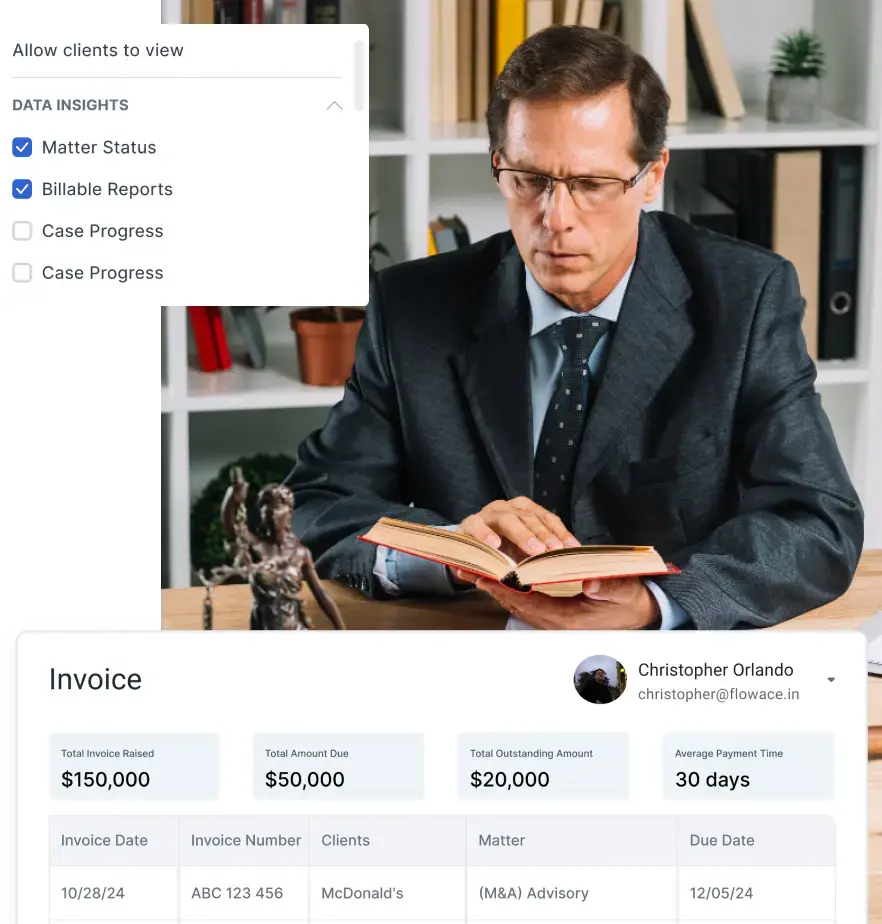
We’re all trying to run our businesses as smoothly as possible. The trick is finding ways to boost productivity, keep data safe, and make everything run like a well-oiled machine. That’s where User Activity Monitoring (UAM) comes in, but it’s not as intimidating as it sounds.
In simple terms, UAM helps you track what your team is doing on company systems, apps, and websites. Think of it like a helpful tool that lets you see how things are going behind the scenes, without being invasive. It helps you figure out where time is going, whether there are any security risks you should worry about, and whether your team’s workflows could use a little tweaking.
If you’ve been curious about how this whole thing works or if it’s something your business should look into, you’re in the right place. In this blog, we’re going to break it down for you: how UAM can help, why it matters, and how to get started. Let’s dive in!
What is User Activity Monitoring?
User Activity Monitoring (UAM) is essentially like having a CCTV for digital workspaces, except instead of watching people walk around, it tracks what users are doing on computers, networks, and applications. It’s a way for businesses to keep an eye on how employees interact with company systems, ensuring security, compliance, and productivity. Think of it as a behind-the-scenes tool that helps prevent data breaches, insider threats, and even accidental mishaps that could put sensitive information at risk.
The best implementations focus on transparency, meaning employees know monitoring is in place and why. For instance, companies use it to detect unusual activity, like an employee accessing confidential files they normally wouldn’t or someone sending large amounts of company data to a personal email. These red flags can help prevent major security incidents before they happen.
How Does User Activity Monitoring Work?
Whether it’s preventing data leaks, blocking harmful websites, or improving productivity, UAM offers a well-rounded approach to keeping businesses safe and efficient. Let’s break down some of the key ways it works.
Real-Time Activity Monitoring
Real-time activity monitoring is like having a live security camera feed of everything happening in a company’s digital space. It continuously tracks user behavior as it happens, offering instant visibility into actions such as software usage, website visits, file transfers, and login attempts. This is crucial for organizations that handle sensitive information, as it allows IT teams to detect unusual or unauthorized activity the moment it occurs.
For example, if an employee suddenly starts downloading large amounts of confidential data outside of normal working hours, real-time monitoring can flag this as a potential security risk. Similarly, suppose someone logs in from an unfamiliar location, such as an employee who typically works in New York suddenly accessing company files from another country without prior notice. In that case, UAM can immediately alert security teams to investigate. This proactive approach helps organizations respond to potential threats before they escalate into full-blown security breaches.
User Activity Reports
While real-time monitoring catches issues in the moment, user activity reports provide a broader view of how employees interact with company systems over time. These reports compile detailed logs of digital activities, offering insights into trends, work habits, and potential risks. They help organizations assess employee engagement, security compliance, and even operational efficiency.
For instance, an HR team might use these reports to identify top-performing employees based on their work patterns, such as the amount of time spent on productive applications versus distractions. IT departments, on the other hand, might use the data to detect insider threats, such as employees accessing sensitive files they shouldn’t or copying data to external devices.
Malicious Website Blocking
The internet is full of risks, and one accidental click on the wrong website can expose an entire organization to cyber threats like phishing attacks, malware, and ransomware. UAM helps prevent this by automatically blocking access to known harmful websites. It acts as a digital gatekeeper, ensuring that employees don’t unintentionally compromise security by visiting unsafe or inappropriate sites.
For example, if an employee unknowingly tries to access a phishing site designed to steal login credentials, the system will immediately block the attempt and alert IT administrators. Similarly, companies can restrict access to non-work-related sites that may lead to productivity losses, such as gaming or social media platforms.
Productivity Tracking
Beyond security, UAM plays a valuable role in measuring workplace productivity. By tracking how employees use their time on company systems, organizations can identify inefficiencies and optimize workflows. Productivity tracking features analyze software usage, website visits, and idle times to determine whether employees are staying focused on their tasks or getting distracted by non-essential activities.
For instance, a company may notice that employees are spending excessive time on administrative tasks rather than core job functions, indicating a need for process automation. It can also highlight cases where employees are overloaded with work, helping managers balance workloads more effectively. The goal of productivity tracking isn’t to micromanage employees but to provide data-driven insights that improve efficiency and job satisfaction.
Activity-based Alarms
Activity-based alarms act as an early warning system, alerting security teams whenever certain actions deviate from predefined rules. These alarms can be triggered for a variety of reasons, such as unauthorized access attempts, data transfers to external storage or unusual login patterns. This ensures that potential security threats are detected and addressed in real time.
For example, if an employee suddenly starts copying large amounts of company data onto a personal USB drive, the system will send an immediate alert to IT administrators. Similarly, if an account experiences multiple failed login attempts from different locations, it could indicate a hacking attempt, prompting the system to lock the account and notify security teams.
Top 4 User Activity Monitoring Tools
1. Flowace
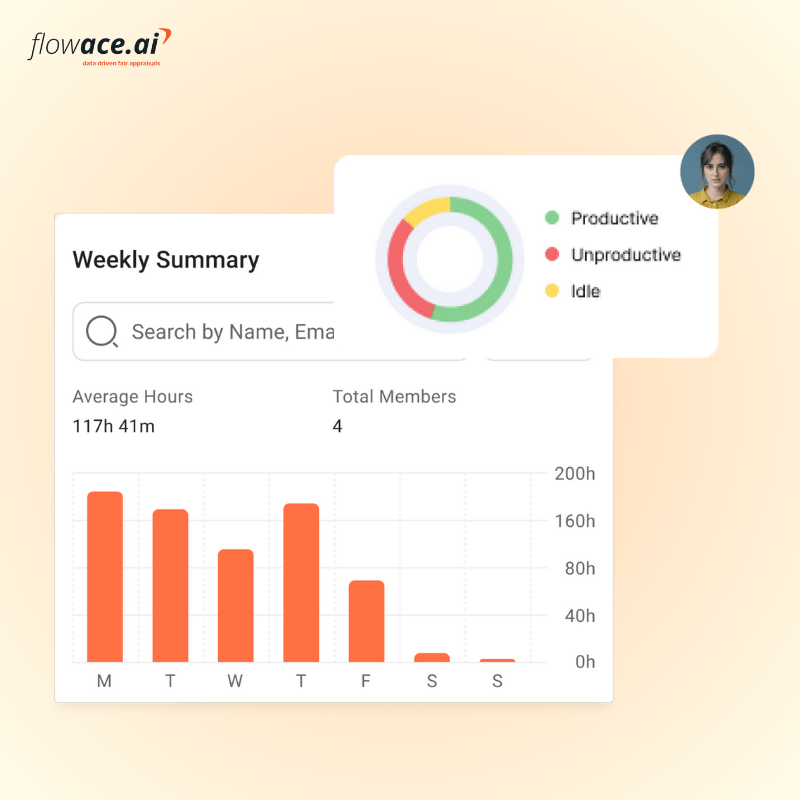
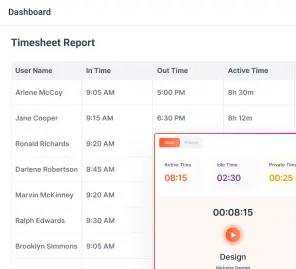
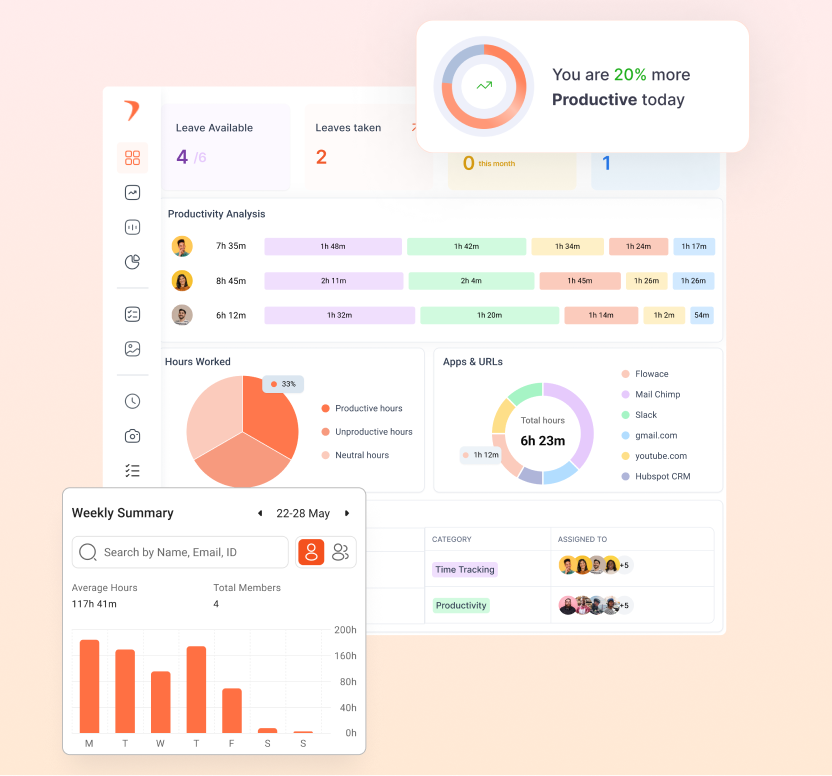
Flowace eliminates the need for manual timesheets by automatically tracking time spent on tasks, applications, and websites. This helps employees focus on their work while still ensuring accurate time logs. Managers can get real-time insights into what employees are working on without micromanaging. Flowace tracks keyboard and mouse activity, app usage, and website visits, helping organizations identify time wasters and boost efficiency.
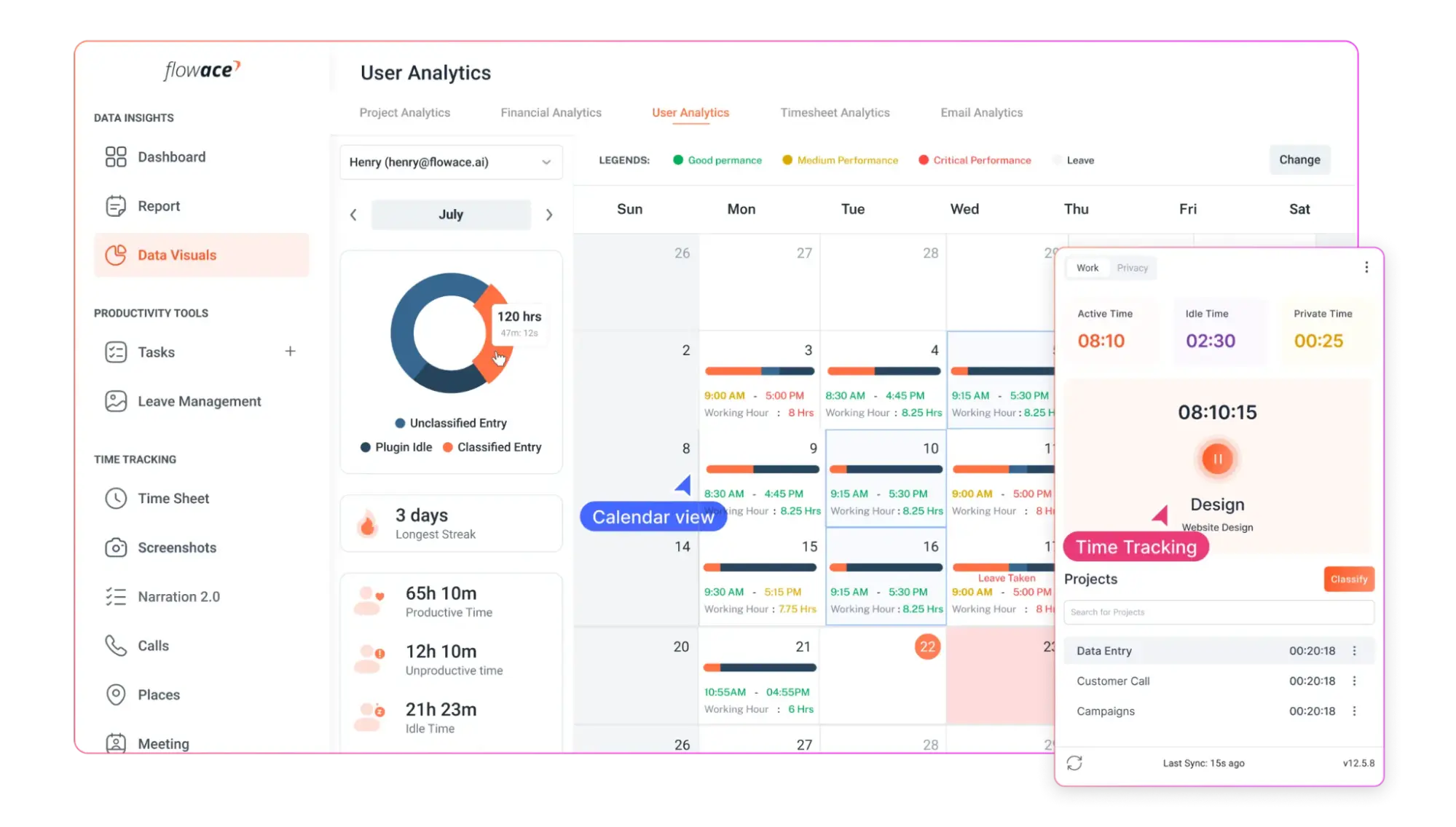
Flowace provides detailed reports on work patterns, helping businesses understand which tasks take the most time, when employees are most productive, and where inefficiencies lie. These insights help in making data-driven decisions to improve performance.
Flowace allows teams to assign tasks to employees and track the time spent on each task or project. This ensures accurate client billing and helps managers allocate resources effectively. For businesses that require more transparency, Flowace can capture periodic screenshots and log user activity, ensuring compliance and preventing unauthorized activities.
2. Teramind
Teramind is one of the most advanced UAM tools for businesses that need tight security controls and insider threat detection. It goes beyond basic activity monitoring and provides deep insights into user behavior to prevent data breaches and detect suspicious activity before it escalates. Tracks user activities across apps, websites, emails, and file transfers as they happen. Captures what employees type to detect unauthorized sharing of confidential data.
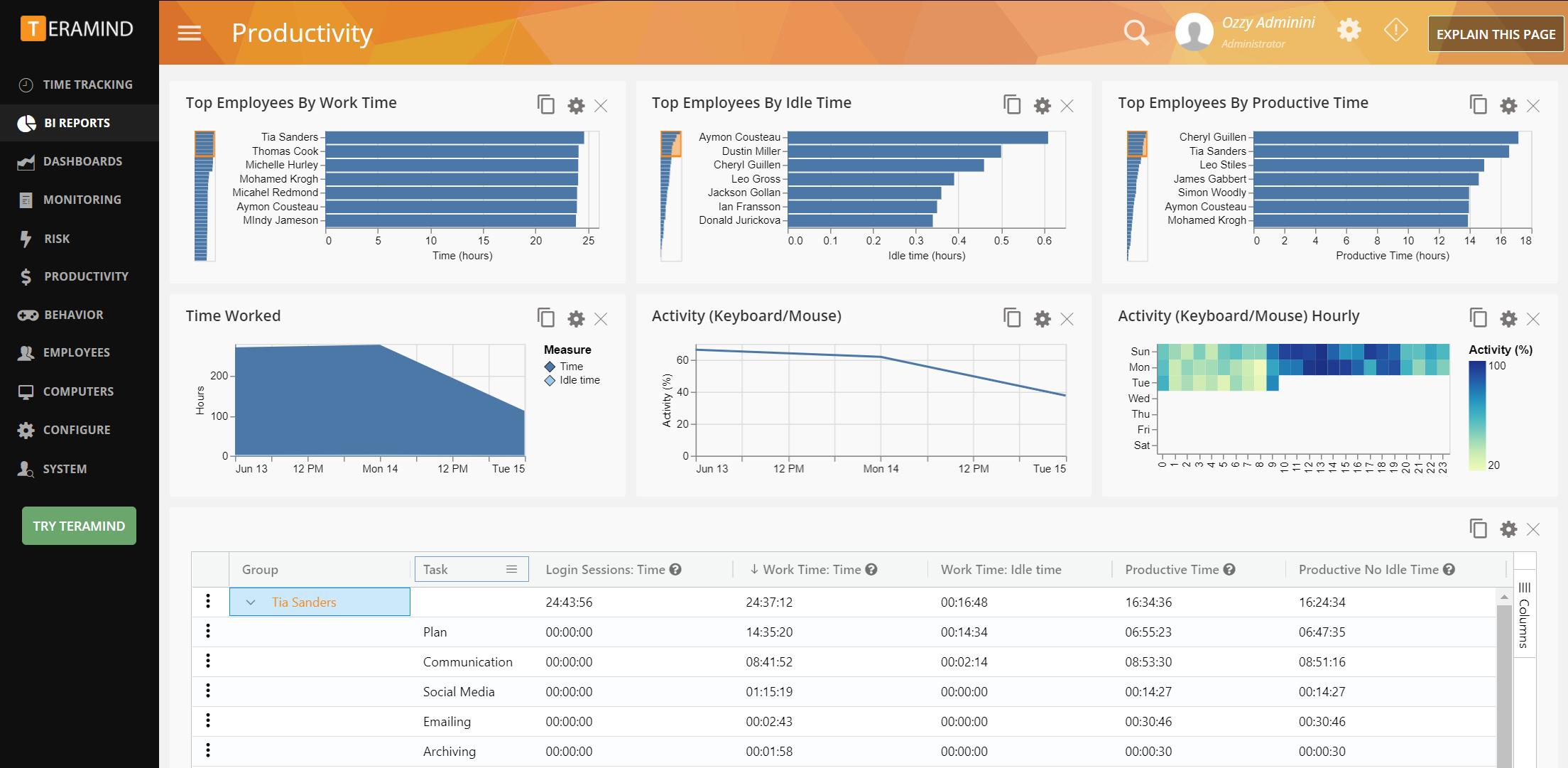
Credit Teramind
Uses machine learning to identify unusual user behavior patterns, such as excessive downloads or attempts to access restricted files. Allows businesses to create rules that block certain actions automatically, such as copying files to external drives.
3. Veriato
Veriato specializes in advanced user behavior analytics, using AI and machine learning to detect patterns that may indicate security risks or compliance violations. It’s particularly beneficial for industries where compliance regulations are strict, such as finance, legal, and healthcare.
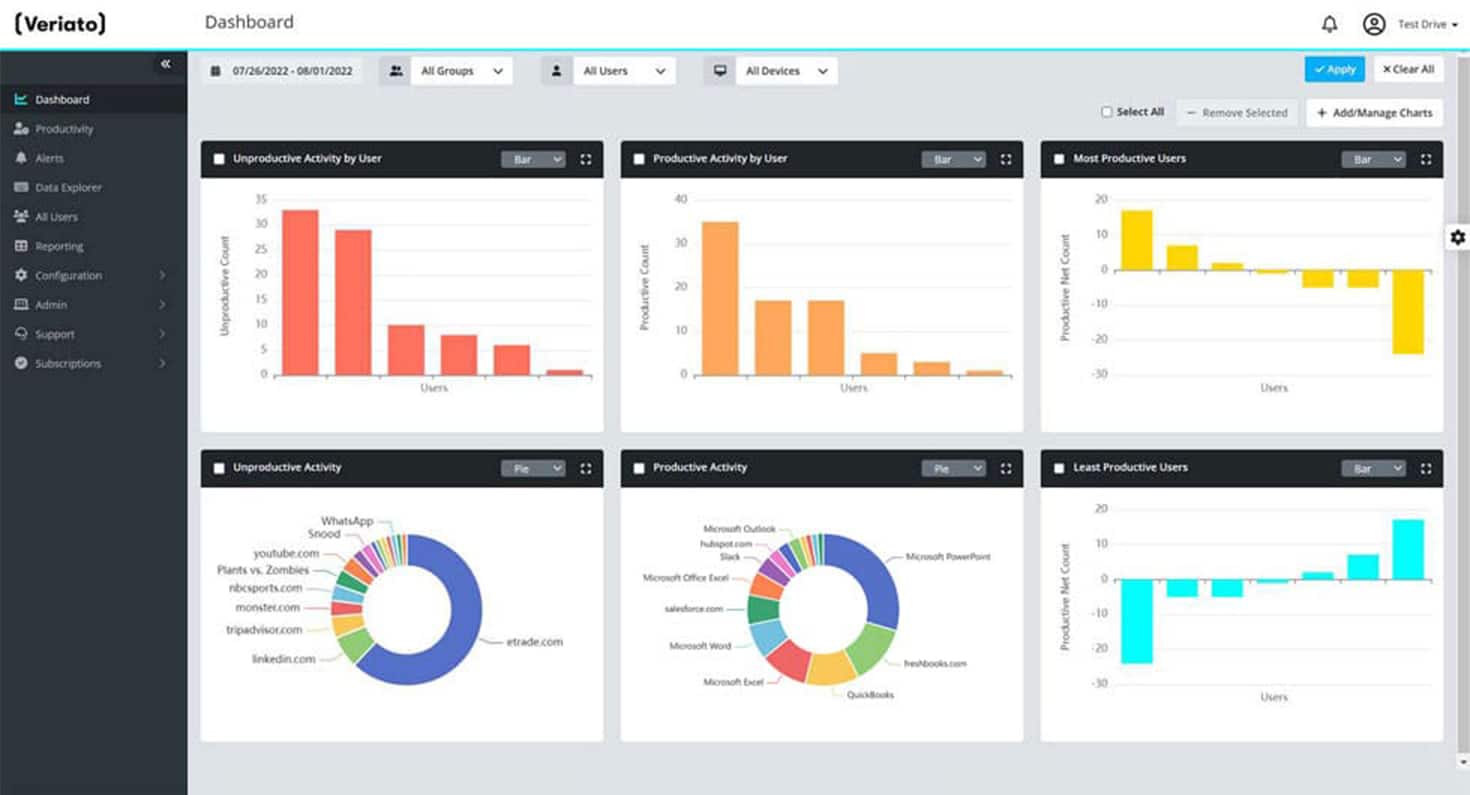
Credit Veriato
It continuously analyzes employee actions to detect anomalies that could signal insider threats. Provides in-depth insights into user activity, helping organizations investigate potential security incidents. Captures user actions in real-time, allowing forensic teams to review suspicious behavior.
Triggers alerts if an employee types, sends, or searches for sensitive information, like client data or company secrets. Scans the dark web to see if leaked company credentials are being sold or used.
4. ActivTrak
Unlike tools that focus primarily on security, ActivTrak is designed to track Employee Productivity and work habits. It helps managers understand how employees use their time, identify distractions, and optimize workflows without invading privacy. Monitors which apps and websites employees use during work hours, classifying them as productive or unproductive.
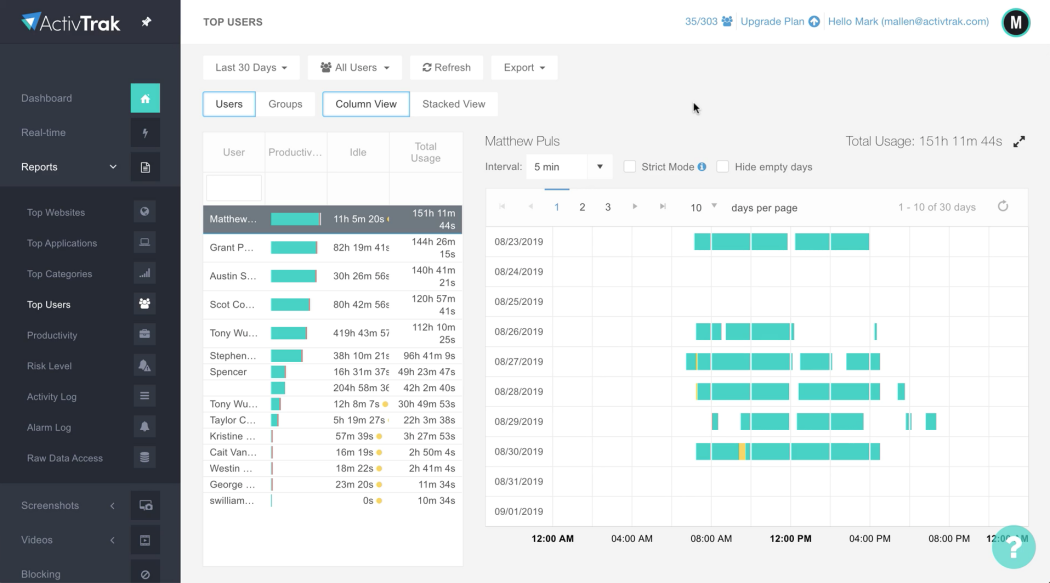
Credit ActivTrack
Provides visual reports on work patterns, helping managers understand team efficiency. The tool also tracks how long employees are actively working versus being idle. ActivTrack uses AI to suggest productivity improvements based on employee behavior. Unlike some UAM tools, ActivTrak does not record keystrokes or capture screen recordings, making it more employee-friendly.
Advantages of User Activity Monitoring
Saves Time and Resources
Time and money are two of the most valuable assets in any business, yet they are often wasted without clear visibility into daily operations. Without monitoring tools, inefficiencies accumulate over time, leading to missed deadlines, bloated operational costs, and misallocation of resources.
UAM allows businesses to track exactly how time is being spent, which tasks are consuming more effort than they should, and where unnecessary expenditures are occurring.
For example, many companies unknowingly continue paying for unused software subscriptions or redundant tools. UAM provides data-driven insights into which applications are frequently used and which are gathering digital dust, allowing businesses to cut unnecessary expenses and redirect their budget toward more impactful investments.
Similarly, tracking workflow patterns helps organizations identify repetitive tasks that can be automated, further saving time and labor costs.
Another key advantage is in reducing time spent on internal investigations and compliance checks. When a security breach or policy violation occurs, businesses without UAM often have to manually sift through logs, emails, and reports to piece together what happened. UAM automates this process by maintaining detailed, time-stamped activity records, making it easier to resolve issues quickly and accurately.
Whether it’s IT troubleshooting, security audits, or performance evaluations, having a structured record of activities saves businesses countless hours and resources that would otherwise be spent on guesswork.
Productive Workflow
Many businesses struggle with unseen productivity roadblocks, such as inefficient processes, poor workload distribution, or employees spending excessive time on low-priority tasks. UAM provides organizations with a clear picture of how work progresses throughout the day, allowing them to refine workflows and improve overall efficiency.
Understanding these patterns helps leadership teams make informed decisions on how to optimize work processes, improve collaboration, and ensure that high-value tasks receive the attention they deserve. Instead of relying on periodic performance reviews or employee self-assessments, managers gain real-time insights into productivity trends, allowing them to take corrective action immediately rather than after inefficiencies have already taken a toll.
Another critical aspect of workflow optimization is balancing workloads across teams. UAM highlights whether some employees are consistently overloaded while others are underutilized and their utilization rate is disproportionate. This allows managers to adjust workloads accordingly, ensuring that tasks are distributed more effectively and preventing burnout while maintaining efficiency.
Better Security
Data breaches, insider threats, and cyberattacks are growing concerns for businesses of all sizes. UAM plays a vital role in strengthening security by providing continuous oversight of digital activities, ensuring that sensitive business data remains protected from both external threats and internal vulnerabilities.
When employees access critical files, move confidential documents, or attempt to log into restricted areas, UAM can immediately detect and flag any unusual or unauthorized behavior. This early detection helps businesses prevent security incidents before they escalate into major breaches.
Additionally, businesses that operate in compliance-heavy industries, such as finance, healthcare, or legal services, rely on UAM to maintain audit trails for regulatory purposes. Keeping track of user activities ensures that businesses can demonstrate compliance with data protection laws, avoid legal complications, and safeguard their reputation. Professionals looking to build expertise in this area can benefit from a post graduate program in cyber security, which covers the advanced tools and techniques needed to manage and mitigate these digital risks effectively. With cyber threats becoming increasingly sophisticated, having a robust monitoring system in place is no longer optional.
Benefits of User Activity Monitoring to Employees
At its core, UAM is a tool that helps employees in many positive ways. Rather than feeling like someone is looking over your shoulder, it creates a more transparent, balanced, and fair work environment. It’s all about helping you do your best work and making sure that your efforts don’t go unnoticed.
- UAM can serve as a personalized development tool, helping you pinpoint specific skills to improve. Rather than waiting for formal performance reviews, you can receive real-time feedback on your strengths and areas to work on.
- With UAM tools, communication becomes more transparent, as employees and managers both have access to the same data about workflows, productivity, and task completion. This shared understanding leads to clearer expectations and a more collaborative environment.
- When new employees join the team, there’s always a bit of a learning curve. UAM tools can make the onboarding process smoother by helping new hires understand what’s expected of them right from the start.
- UAM tools help shift the focus from simply “being at work” to delivering results. Since UAM tracks measurable productivity and performance, it encourages employees to focus on what really matters: getting things done effectively.
- With many employees working remotely or in hybrid models these days, it can be tough to manage and monitor productivity. However, UAM tools can bridge that gap by tracking productivity regardless of location. It ensures that remote workers have the same level of visibility and support as their in-office counterparts.
- We all know how easy it is to fall into the trap of overworking, especially in high-pressure environments. UAM can help by monitoring not just productivity but also work patterns that indicate burnout. If the system detects that an employee is consistently working long hours or seems to be under constant pressure, managers can take action to prevent burnout before it becomes a serious issue.
Disadvantages of User Activity Monitoring
If user activity monitoring is so great, what could possibly get in the way? A lot, actually.
- UAM tools can sometimes feel intrusive to employees, as they track personal behavior, online activities, and even communications. This can lead to privacy issues if employees feel they are constantly being watched, potentially affecting trust and morale.
- While UAM tools are designed to improve efficiency, they can sometimes give managers a false sense of control.
- UAM tools are primarily driven by data, and while data is valuable, over-reliance on it can ignore important nuances like employee context or circumstances.
- Data collected by UAM tools may be misinterpreted if not properly understood.
- Many employees may resist the implementation of UAM tools, especially if they feel that the monitoring is unwarranted or too invasive.
- Depending on the region, the use of UAM tools might be subject to strict regulations, especially concerning employee data privacy.
- Constant monitoring can erode trust between employees and management, especially if the purpose of the monitoring isn’t clearly communicated.
Legal Consideration While Implementing Tracking Applications
One of the most critical legal aspects when implementing tracking applications is obtaining employee consent. In many jurisdictions, businesses are required to inform employees about the monitoring activities and get their explicit consent before starting any tracking or surveillance. This consent should be clear and informed, meaning employees must fully understand what data is being collected, how it will be used, and for how long it will be retained.
Employers should not assume that consent is automatically implied when employees sign a general employment contract. Instead, they need to outline tracking policies in a transparent manner, possibly within a company’s code of conduct or an updated employee handbook. This ensures that employees feel comfortable and aware of what they’re agreeing to, reducing the chances of misunderstandings or complaints later on.
Each country (and sometimes even regions within countries) has its own set of privacy laws governing the collection, storage, and use of personal data. For instance, in Europe, the General Data Protection Regulation (GDPR) sets strict guidelines on how companies must handle personal information. It includes provisions on data minimization, meaning businesses can only collect data that is necessary for the specific purpose it was gathered.
Tracking applications generate a lot of data, and companies must establish clear data retention and deletion policies. Legally, data should only be retained for as long as it is necessary to fulfill its purpose. Once the purpose has been achieved or if the data is no longer needed, it must be securely deleted or anonymized. Holding onto data for too long can lead to potential legal and compliance risks, especially in jurisdictions with stringent data protection laws.
While implementing tracking tools, companies must ensure that their monitoring practices are non-discriminatory and applied equally to all employees. It’s essential that no group of employees is unfairly targeted or subjected to more scrutiny than others based on age, gender, race, or any other protected characteristic.
It’s also important to be mindful of how monitoring can affect different employee groups. For example, monitoring tools used in customer-facing roles may not be appropriate for remote employees. Applying policies uniformly can help avoid legal claims related to discrimination or unequal treatment.
User Activity Monitoring Best Practices
- Always inform employees about monitoring and get their clear, written consent. Make sure they understand what data is being tracked and why. Transparency is key to maintaining trust.
- Set clear guidelines about what activities will be monitored and ensure these policies are communicated effectively to all employees. Policies should address the scope, purpose, and limitations of monitoring to avoid confusion.
- Make sure your UAM tools and practices comply with data protection regulations like GDPR, CCPA, or other local laws.
- Only track activities that are necessary for legitimate business purposes, such as improving productivity or ensuring security.
- Ensure that any data collected through UAM tools is securely stored and protected from unauthorized access.
- While monitoring is helpful, avoid crossing the line into micromanagement. Focus on results and outcomes, not excessive tracking of every detail, which can lead to employee frustration and disengagement.
- Conduct regular audits of your UAM policies and the data collected to ensure compliance and identify any areas for improvement.
How To Identify Which User Activity Monitoring Tools Are Suitable For You?
1. Understand Your Business Needs
The first thing you need to do is take a step back and think about why you need a UAM tool in the first place. Are you more concerned about security, protecting your company from insider threats and data breaches? Or are you looking to optimize productivity, track how employees spend their time, and identify areas for improvement?
If security is your primary concern, you’ll want a tool that offers features like keystroke logging, session recording, and real-time alerts for suspicious activities. On the other hand, if you’re more interested in tracking productivity, look for a tool that focuses on app usage, idle time, and work habits.
2. Evaluate Your Budget
Like any software, UAM tools come in a range of price points. Some tools are more affordable and offer the basics, while others are premium solutions that come with extensive features but might also come with a hefty price tag. It’s important to figure out how much you’re willing to spend based on your needs.
If you’re a smaller business with a tight budget, there are plenty of affordable options that still offer solid features like activity tracking and reporting. However, if you’re in a larger organization with complex monitoring needs, you might want to invest in a more feature-rich tool that can scale as your business grows.
3. Look for Integration with Existing Systems
Any good UAM tool should seamlessly integrate with your existing systems. Whether you’re using HR software, productivity tools, or other internal systems, you want a UAM tool that won’t disrupt your workflow.
For instance, if your business relies heavily on project management tools like Trello, Slack, or Asana, check if the UAM tool can integrate with these platforms. You don’t want to be juggling multiple tools that don’t communicate with each other. Integration capabilities can also help streamline data collection and provide a more holistic view of employee performance.
4. Consider Ease of Use
No matter how advanced a UAM tool is, it won’t be useful if it’s too complicated to use. Ease of use is a major factor to consider when choosing a UAM solution. You want a tool that’s intuitive, with a user-friendly interface and easy-to-navigate dashboards. This will make it easier for both HR and management to quickly analyze data without needing a steep learning curve.
You can usually get a feel for this by requesting a demo or trial version of the software. Take note of how quickly you or your team can set it up and whether the dashboards and reports are easy to understand.
5. Review the Features That Matter Most to You
Each UAM tool comes with its own set of features, so it’s important to focus on the ones that matter most for your business. Here are some questions to ask yourself. Does the tool offer features like real-time monitoring, session recording, or alerts for suspicious activity? Does it help track app usage, idle time, and work habits? Does the tool help you meet compliance regulations, especially if you’re in an industry with strict data privacy laws (like GDPR or HIPAA)?
Can the tool be customized to suit your specific needs? For example, can you create custom reports, set alerts, or monitor specific apps? Does the tool offer detailed reports and analytics that help you draw insights from the data collected? Can you generate reports on demand or on a scheduled basis? By zeroing in on the specific features that align with your business goals, you can better assess which tools offer the functionalities you need.
6. Prioritize Employee Transparency and Trust
The best UAM tools are the ones that are implemented transparently and with trust in mind. You want a tool that helps you improve productivity and security without making employees feel like they’re being spied on.
Look for tools that offer clear policies and communication features. Some tools include features that allow employees to see what’s being tracked or give them access to their own data. Having these features will help you build trust with employees and ensure they understand the reasons for monitoring. Trust is key in maintaining morale and ensuring that the tool is used for the right purposes.
7. Test the Customer Support and Reliability
When implementing a new tool, you want to ensure that it’s backed by strong customer support. Any technical issues or questions should be addressed quickly and efficiently. Before you commit to a particular UAM tool, make sure it offers solid customer support options, whether it’s live chat, email support, or a comprehensive knowledge base.
8. Consider Scalability
Finally, consider whether the UAM tool can grow with your business. If you’re a growing organization, you’ll need a tool that can scale to handle increased employee numbers, more devices, and more data. Look for tools that offer flexible plans so you can upgrade as your needs change over time.
User Activity Monitoring With Flowace
When it comes to User Activity Monitoring (UAM), one of the tools gaining attention is Flowace. Flowace is designed to be an all-in-one solution that helps businesses not only track employee activity but also optimize productivity and manage time efficiently. If you’re exploring UAM tools for your organization, Flowace might be worth considering due to its user-friendly interface and powerful features.
One of the standout features of Flowace is its time-tracking capabilities. The tool automatically tracks how long employees spend on different tasks, applications, and websites. Whether you’re in an office environment or managing remote teams, Flowace allows you to monitor digital activity across various platforms without any hassle. What’s helpful here is that you can categorize tasks and projects, allowing you to get a clearer view of how much time is being spent on productive vs. non-productive activities.
With Flowace, you can track app usage, measure focus levels, and detect time-wasting activities. For example, if you see that employees spend a significant amount of time on social media or chat apps, you can introduce policies or encourage them to use work-focused apps during work hours.
What’s interesting about Flowace is how it doesn’t just record data for the sake of it. It gives managers actionable insights that help improve overall productivity without coming off as controlling. It allows for a much more balanced approach to time management, where employees can also reflect on their productivity and adjust where needed.
As more businesses move to remote work or hybrid models, managing remote teams has become more challenging. Flowace offers features that help you monitor remote employees’ activities in real time, ensuring that they stay on task while giving them the flexibility they need. You can see how employees in different locations are spending their time, even if they aren’t physically present in the office. This visibility is crucial for remote-first companies or those with employees spread across different regions.
Another key feature of Flowace is its focus on employee wellbeing. While it’s easy to get caught up in tracking tasks and productivity, Flowace ensures that monitoring doesn’t come at the cost of employee morale. The tool provides regular feedback so employees can see their progress and make adjustments without feeling micromanaged. It’s about creating a healthy work environment where employees are motivated to improve their productivity without feeling over-surveilled.
Want to see how we can customize Flowace to suit your working style? Book a demo today.
Related Articles
- Employee Monitoring: Complete Guide 2025
- How to Choose Employee Monitoring Software
- 9 Ways Employees Fool Monitoring Software
- Employee Monitoring Data Protection Guide
- How Employee Monitoring Software Works & Matters
- What is Employee Task Tracking? Complete Guide
- Best Employee Monitoring Software 2025
- Employee Idle Time Tracking Software Guide
- Employee Monitoring Best Practices 2025
- Employee Monitoring Laws: Legal Guide 2025
- Remote Team Monitoring: Perspectives & Insights
- Employee Monitoring Statistics 2025
- Performance Monitoring: Benefits & Concerns
- Employee Monitoring Myths Debunked
- Employee Wellbeing Monitoring Solutions
- Create Ethical Employee Monitoring Policy