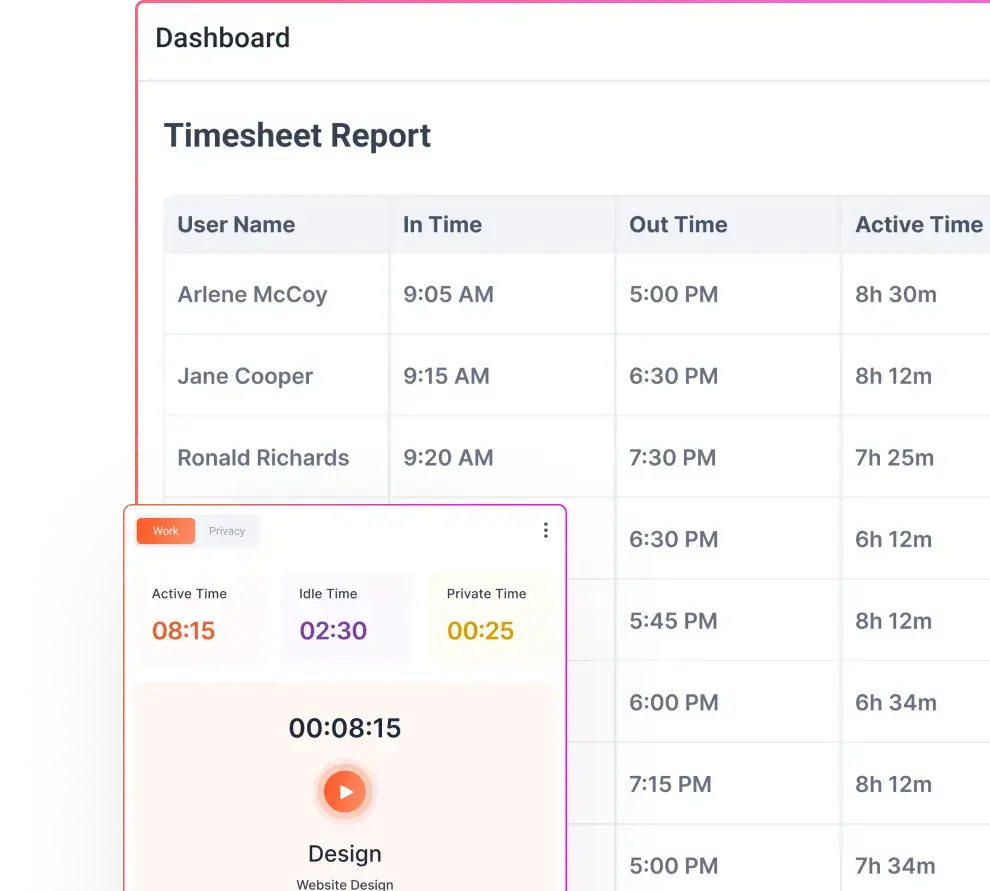
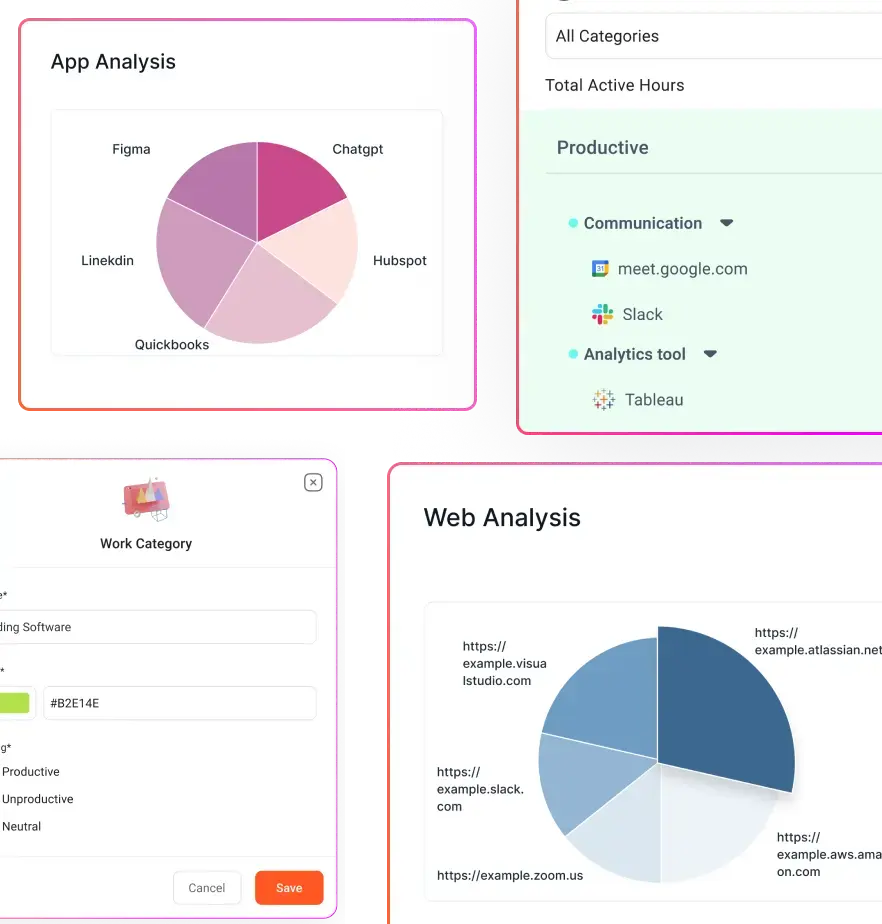
Employee monitoring is no longer a question of if but how. Companies need visibility into workplace productivity and data protection. But here’s the challenge: how do you implement monitoring in a way that boosts efficiency without compromising trust?
A poorly designed monitoring policy can feel invasive, making employees uncomfortable and even reducing morale. On the other hand, a well-structured, ethical approach ensures that monitoring is transparent, fair, and serves a legitimate purpose, whether it’s improving workflow, ensuring compliance, or safeguarding company data.
The key? Balance.
This blog will give you insights into how you can attain this delicate balance.
What is an Employee Monitoring Policy?
If a company is going to monitor its employees, there needs to be clear rules in place. That’s where an Employee Monitoring Policy comes in. It’s essentially a document that lays out what’s being monitored, why it’s being monitored, and how the company will handle the collected data. Think of it as the rulebook that ensures transparency between employers and employees when it comes to tracking work activities.
Imagine starting a new job, only to find out months later that your emails, browsing history, and even how long you stay away from your desk are being tracked, without you knowing! That’s a recipe for distrust. But if the company has a clear, well-communicated policy, employees understand the “what” and the “why” behind the monitoring, which makes it feel less intrusive and more like a productivity tool.
Why Prioritize Ethics in Employee Monitoring?

Whether it’s security cameras at work, time tracking software, or email monitoring, employees don’t want to feel like their every move is under a microscope. And honestly, businesses don’t want that either, because constant surveillance breeds distrust, stress, and resentment. That’s why ethics matter when it comes to employee monitoring.
Ethical monitoring isn’t just about avoiding lawsuits or compliance violations (although those are important too). It’s about creating a workplace where employees feel respected, valued, and trusted, even while tracking tools are in place. When done ethically, monitoring can actually boost productivity, strengthen workplace culture, and improve overall job satisfaction. But when done unethically? It can destroy morale, fuel high turnover rates, and even push top talent away.
There’s a big difference between keeping an eye on productivity and invading personal privacy. If monitoring is done without transparency, employees start wondering: Is my boss reading my personal messages? Are they tracking how often I go to the bathroom? Will I get in trouble if I take a few minutes to breathe between tasks?
When companies fail to communicate their monitoring policies openly, employees don’t just feel uncomfortable; they start working in fear. That’s when productivity actually drops instead of improving.
No one does their best work when they’re paranoid about being watched. Employees who feel respected and trusted work harder, stay longer, and contribute more. On the flip side, a company that prioritizes control over culture will struggle with disengagement, resentment, and high turnover.
Legal Considerations for Employee Monitoring
In the United States, federal laws generally allow businesses to monitor employees, but with some important restrictions. The Electronic Communications Privacy Act (ECPA) permits employers to track work emails, phone calls, and internet usage, but it draws a line at personal communications.
If an employee is using a company-provided device, monitoring is usually fair game, but secretly recording personal conversations can lead to legal trouble. Meanwhile, the National Labor Relations Act (NLRA) ensures that employees can freely discuss wages and working conditions without fear of surveillance or retaliation.
State laws add another layer of complexity. Some states, like California and Connecticut, require employers to notify employees before monitoring their communications. Others have stricter regulations around biometric data collection, such as fingerprint scans or facial recognition for attendance tracking. Illinois, for instance, has one of the strictest biometric privacy laws, requiring companies to obtain written consent before collecting or storing biometric data.
Additionally, some states regulate GPS tracking, ensuring that businesses don’t track employees outside of work hours without consent.
For companies with a global workforce, international laws introduce even stricter privacy requirements. The European Union’s General Data Protection Regulation (GDPR) demands transparency in employee monitoring.
Employers must clearly state what data they’re collecting, why it’s necessary, and how long they plan to store it. Employees also have the right to access their monitoring data and request its deletion. Canada’s PIPEDA law follows similar principles, requiring businesses to have a valid reason for tracking employees and to obtain their consent before collecting personal data.
Australia, Brazil, and India also have growing privacy regulations, making it essential for multinational companies to carefully review and comply with local laws.
The key takeaway for businesses is that legal compliance is a fundamental part of implementing any employee monitoring system. Transparency is critical; employees should always know what’s being monitored and why. Companies should also ensure that monitoring practices are reasonable and not overly intrusive.
A well-crafted employee monitoring policy should align with both business needs and legal requirements, striking the right balance between oversight and privacy. When done correctly, monitoring can enhance security and efficiency without compromising trust.
Employee Monitoring Policy Template (USA)

1. Purpose
This Employee Monitoring Policy sets out how [Company Name] monitors the use of company systems, networks, and resources to ensure security, compliance, and productivity, while respecting employee privacy rights.
2. Scope
This policy applies to all employees, contractors, and temporary staff of [Company Name] who use company-owned or company-managed systems, devices, or accounts.
3. Types of Monitoring
- Email & Communication Monitoring – for compliance and security
- Internet Usage Monitoring – to prevent misuse
- Computer Activity & Productivity Monitoring – to assess work efficiency
- Security & Access Logs – to safeguard company assets
4. Legal Compliance
[Company Name] complies with applicable federal and state laws, including the Electronic Communications Privacy Act (ECPA), CCPA/CPRA (California), and other relevant data protection laws.
5. Employee Rights
Employees have the right to:
- Be notified of monitoring activities
- Access their personal monitoring data upon request
- Raise concerns through HR
6. Consent
Employees must provide written consent before monitoring begins. Consent will be collected via the Employee Monitoring Consent Form attached to this policy.
7. Policy Review
This policy will be reviewed annually to ensure compliance with evolving laws and company practices.
Sample Employee Notification Letter
Subject: Notification of Employee Monitoring Policy
Dear [Employee Name],
As part of [Company Name]’s commitment to security, compliance, and productivity, we have implemented an Employee Monitoring Policy. This ensures proper use of company resources while protecting sensitive data.
Monitoring will include: [types of monitoring here].
Please review the attached policy and consent form. Your acknowledgment is required before [date].
Thank you for your cooperation,
[Manager/HR Contact]
State-by-State Legal Requirements Table for the USA
| State | Notice Required | Consent Required | Specific laws/notes | Penalties/consequences |
| Alabama | Varies/recommended | One-party | State wiretap statute generally permits one-party recording. | Civil & criminal penalties possible if violated. |
| Alaska | Varies/recommended | One-party | One-party recording permitted. | Civil/criminal penalties if violated. |
| Arizona | Varies/recommended | One-party | One-party consent for recordings. | Civil/criminal. |
| Arkansas | Varies/recommended | One-party | One-party consent. | Civil/criminal. |
| California | Varies/recommended (employers usually notify) | All-party (strong protections for audio) | CA Penal Code §632 (eavesdropping) + CCPA/CPRA protections for personal data. Employers commonly give written notice; audio recordings without consent risk statutory damages. | Statutory civil damages possible; criminal penalties for illegal interception; consumer/CCPA enforcement can apply. |
| Colorado | Varies/recommended | One-party | One-party recording for most communications. | Civil/criminal. |
| Connecticut | Yes — written notice required for certain monitoring | All-party (electronic) | Conn. Gen. Stat. §31-48d requires conspicuous notice for electronic monitoring in certain contexts; recording/consent rules are stricter for electronic communications. | Civil penalties; potential criminal charges for unlawful recordings. |
| Delaware | Yes — notice required (electronic monitoring rules) | All-party (per many lists) | Delaware wiretap statutes; employers must be careful to provide notice for electronic intercepts. | Criminal penalties and civil liability possible. |
| Florida | Varies/recommended | All-party (per common lists) | Florida has all-party consent rules for many recordings (phone). | Criminal penalties and civil exposure for unlawful recordings. |
| Georgia | Varies/recommended | One-party | One-party consent state for recording. | Civil/criminal. |
| Hawaii | Varies/recommended | Mixed (some two-party rules for certain private places) | Some nuance: depends on in-person vs electronic and place of recording. | Varies; risk of civil/criminal liability. |
| Idaho | Varies/recommended | One-party | One-party recording allowed. | Civil/criminal. |
| Illinois | Varies/recommended | All-party (strong laws for private conversations) | Illinois statute is strict for non-electronic private conversations and imposes serious penalties for unlawful recordings (BIPA is separate re: biometrics). | Potential felony/misdemeanor liability and civil damages; high-risk area. |
| Indiana | Varies/recommended | One-party | One-party consent for recordings. | Civil/criminal. |
| Iowa | Varies/recommended | One-party | One-party. | Civil/criminal. |
| Kansas | Varies/recommended | One-party | One-party. | Civil/criminal. |
| Kentucky | Varies/recommended | One-party | One-party. | Civil/criminal. |
| Louisiana | Varies/recommended | One-party | One-party. | Civil/criminal. |
| Maine | Varies/recommended | One-party | One-party. | Civil/criminal. |
| Maryland | Varies/recommended | All-party | Maryland requires all-party consent for many recordings. | Criminal & civil penalties possible. |
| Massachusetts | Varies/recommended | All-party (secret recordings limited) | Strong restrictions on secret recordings; limited public-location exceptions. | Criminal & civil remedies; potential fines. |
| Michigan | Varies/recommended | All-party (varies by context) | Michigan has complex rules — in some circumstances, all-party consent is required. | Civil/criminal penalties possible. |
| Minnesota | Varies / recommended | One-party | One-party. | Civil/criminal. |
| Mississippi | Varies / recommended | One-party | One-party. | Civil/criminal. |
| Missouri | Varies / recommended | One-party | One-party. | Civil/criminal. |
| Montana | Varies / recommended | All-party / notification rules (listed by some sources) | Montana has particular restrictions / notification rules. | Criminal/civil penalties if violated. |
| Nebraska | Varies / recommended | One-party | One-party. | Civil/criminal. |
| Nevada | Varies / recommended | Mixed — some sources list all-party for phone/text; in-person may differ | Nevada’s law has distinctions between types (phone vs in-person). | Civil/criminal; special rules for electronic communications. |
| New Hampshire | Varies / recommended | All-party (listed by some sources) | New Hampshire appears on several all-party lists. | Civil/criminal penalties possible. |
| New Jersey | Varies / recommended | One-party | One-party. | Civil/criminal. |
| New Mexico | Varies / recommended | One-party | One-party. | Civil/criminal. |
| New York | Varies / recommended | One-party | New York is commonly classified as one-party for recordings, but employers should still provide notice as best practice; NY labor law contains employer disclosure obligations in some contexts | Civil liability possible; statutory fines vary |
| North Carolina | Varies / recommended | One-party | One-party | Civil/criminal |
| North Dakota | Varies / recommended | One-party | One-party | Civil/criminal |
| Ohio | Varies / recommended | One-party | One-party | Civil/criminal |
| Oklahoma | Varies / recommended | One-party | One-party | Civil/criminal |
| Oregon | Varies / recommended | Mixed (sources vary; some list all-party for in-person) | Oregon can be one-party for phone, but has some two-party aspects for in-person recordings — treat as nuanced | Civil/criminal; check the exact statute |
| Pennsylvania | Varies / recommended | All-party (listed by several sources) | Pennsylvania courts/statutes have all-party consent for many phone recordings | Civil/criminal penalties |
| Rhode Island | Varies/recommended | One-party (but privacy expectations matter) | Consent is sometimes not required where no expectation of privacy | Civil/criminal |
| South Carolina | Varies/recommended | One-party | One-party | Civil/criminal |
| South Dakota | Varies/recommended | One-party (with caveats) | One-party in many cases, but there are caveats depending on who records | Civil/criminal |
| Tennessee | Varies/recommended | One-party | One-party | Civil/criminal |
| Texas | Varies/recommended | One-party (but audio consent rules vary) | Texas is generally one-party for recordings, but the recording of certain communications may trigger stricter rules | Civil/criminal |
| Utah | Varies/recommended | One-party | One-party | Civil/criminal |
| Vermont | Varies/recommended | Mixed / sometimes listed as all-party | Some lists include Vermont as all-party for some situations — ambiguous in secondary sources | Civil/criminal potential |
| Virginia | Varies/recommended | One-party | One-party | Civil/criminal |
| Washington | Varies/recommended | All-party (listed by several sources) | Washington is commonly listed among all-party states for recordings | Criminal penalties and civil exposure for unlawful recordings |
| West Virginia | Varies/recommended | One-party | One-party | Civil/criminal |
| Wisconsin | Varies/recommended | One-party | One-party | Civil/criminal |
| Wyoming | Varies/recommended | One-party | One-party | Civil/criminal |
Types of Employee Monitoring
There is a spectrum of employee monitoring methods, from traditional in-person oversight to high-tech digital surveillance. Here are the varied types of employee monitoring:
Invasive vs. Non-Invasive Monitoring
Not all monitoring methods are created equal. Some are highly intrusive, tracking every keystroke and screen movement, while others focus on general productivity insights without prying into personal details. Understanding the difference is crucial for businesses that want to monitor ethically.
Keystroke logging is one of the most invasive methods, as it records everything an employee types, emails, passwords, personal messages, and even accidental typos. While some companies use it to detect data breaches, it can feel like a huge invasion of privacy and often leads to resentment among employees. Phone call monitoring is another sensitive area. While recording work-related calls can help with quality control and compliance, secretly listening in on personal conversations is a serious breach of trust.
On the other hand, non-invasive methods like activity tracking and automated time management tools focus on outcomes rather than micro-managing behavior. For instance, monitoring overall work hours, app usage trends, and project timelines helps companies understand efficiency without crossing ethical lines. Ethical alternatives, such as self-reported time tracking or AI-driven productivity analytics, provide insights without making employees feel like they’re under surveillance.
Ultimately, the difference between invasive and non-invasive monitoring comes down to intent. If monitoring is used to support and empower employees, it can be a valuable tool. But if it’s used as a means of control or punishment, it can quickly become toxic.
Monitoring Specific Communication Channels
Communication monitoring is one of the most common forms of employee tracking, as companies want to ensure that work-related conversations remain professional and secure. However, not all communication channels are monitored in the same way, and different methods have different implications.
Email monitoring is widely used, especially in industries that handle sensitive data. Employers can scan for keywords, attachments, or suspicious messages to prevent data leaks or inappropriate communication. However, privacy concerns arise when personal emails get caught in the mix, which is why clear policies and disclaimers are essential.
Telephone call monitoring is more common in customer service and sales teams. Many businesses record calls for quality assurance and training purposes, ensuring that employees handle clients professionally. However, employees must be notified that calls are being recorded, and monitoring should never extend to personal calls.
Internet usage tracking helps businesses understand how employees spend their time online. It can reveal productivity trends, flag excessive social media usage, and even prevent security risks from unsafe browsing. However, overly strict restrictions can frustrate employees and create a culture of distrust. Instead of blocking everything, many companies prefer to track patterns and offer guidance on appropriate internet use.
Social media monitoring is a gray area. While employers can monitor public social media posts, tracking private messages or personal accounts crosses ethical boundaries. Some companies use AI tools to flag negative mentions of the company online, but this must be done carefully to respect employees’ freedom of speech outside work hours.
The key to ethical communication monitoring is transparency. Employees should always know what’s being tracked and why, so there are no surprises.
Tools & Techniques
Technology has made employee monitoring easier than ever, with a wide range of software and tools available for businesses. However, choosing the right tool depends on what the company wants to achieve, security, productivity, compliance, or all three.
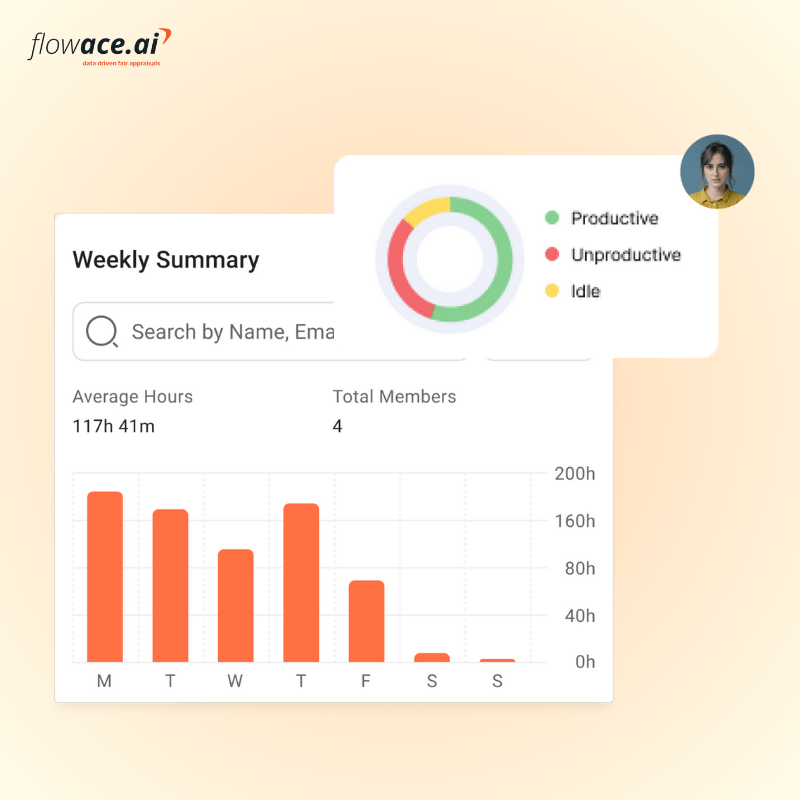
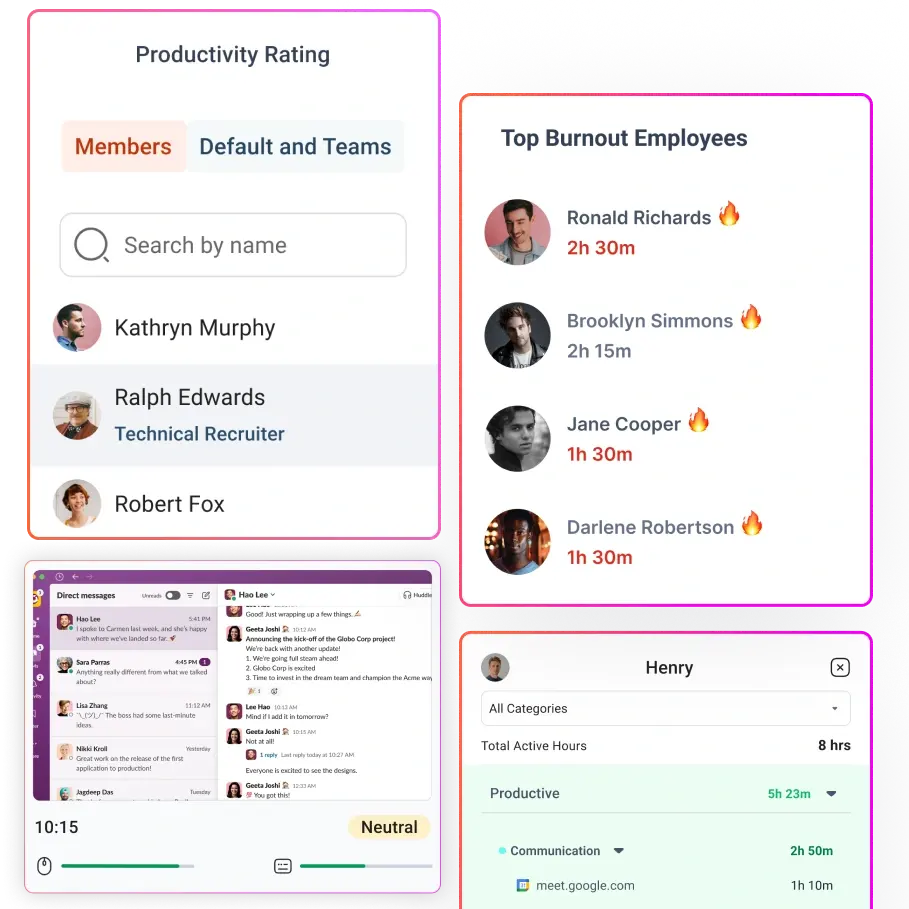
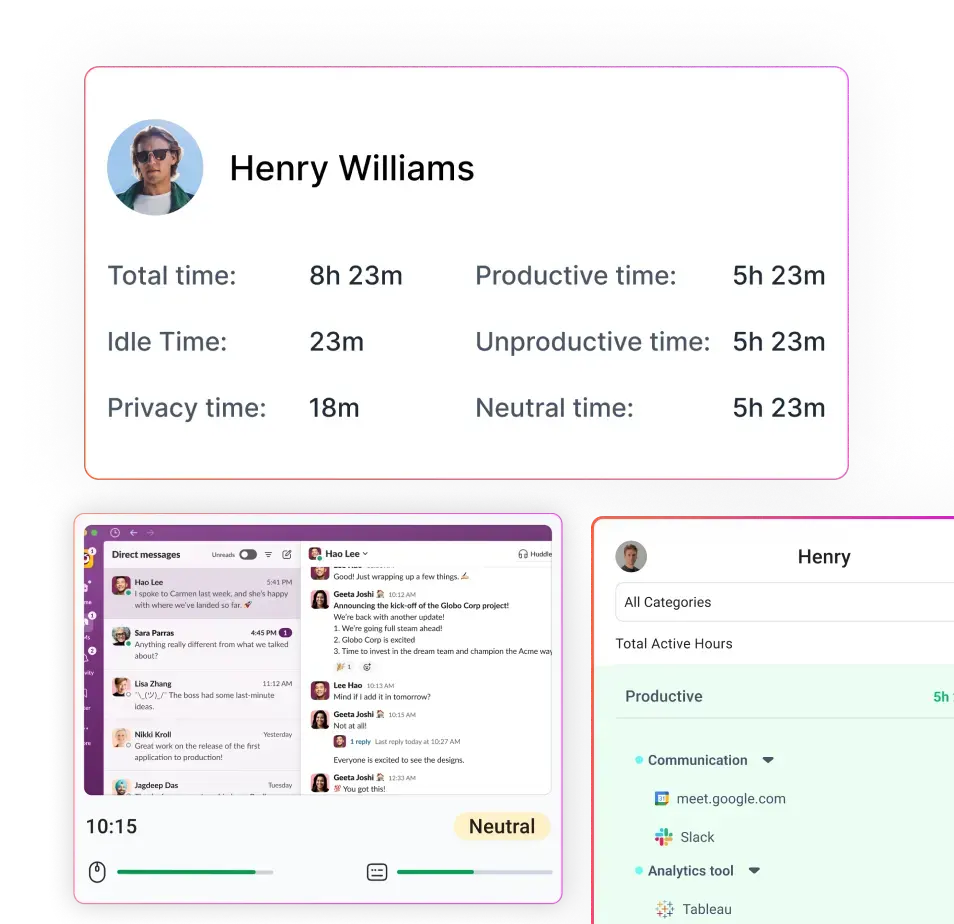
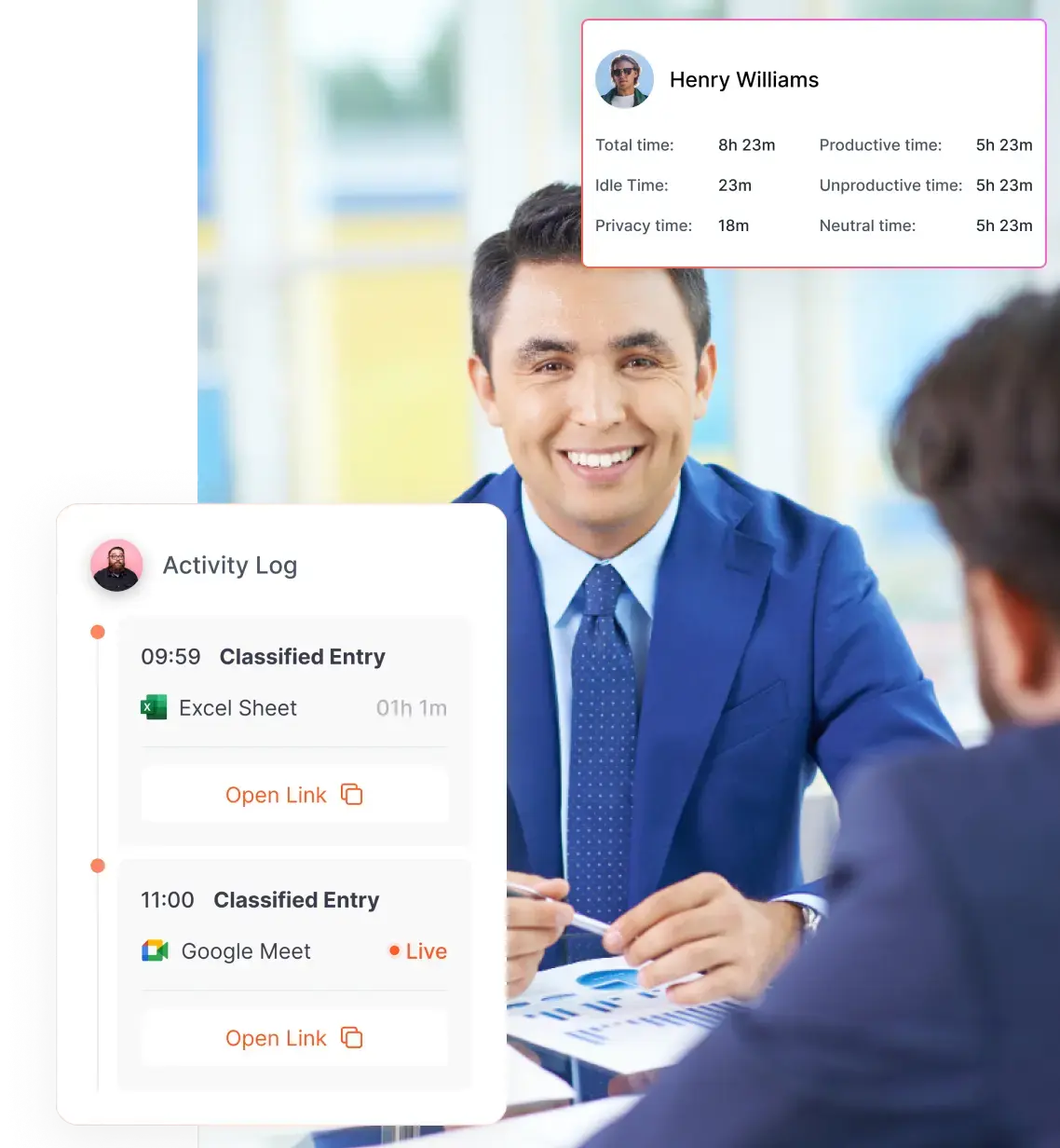
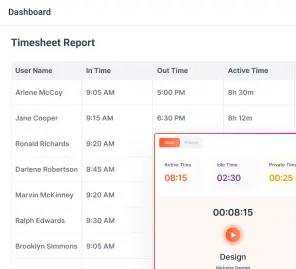
Time-tracking software, such as Flowace, helps employees log their work hours automatically without the hassle of manual input. It records work activities, app usage, and project timelines while keeping employee privacy in mind. Unlike intrusive keystroke loggers, Flowace provides insightful analytics without making employees feel micromanaged.
Project management tools like Trello, Asana, and ClickUp track task progress and team collaboration rather than individual employee behavior. These platforms help managers see who’s working on what without monitoring personal activities.
Screen monitoring tools like Hubstaff and Teramind take things a step further, capturing screenshots or real-time activity. While useful for remote teams, these tools can feel intrusive if used excessively. Employers must set clear boundaries and avoid constant surveillance.
AI-powered analytics tools analyze productivity trends rather than tracking individuals. These tools offer a big-picture view of workplace efficiency, helping companies make data-driven decisions without singling out employees unfairly.
The right monitoring tool should support business goals while respecting employees’ time, privacy, and autonomy. Companies that take an ethical approach to monitoring will see better engagement, improved trust, and a more productive workforce overall.
How to Create an Ethical Employee Monitoring Policy
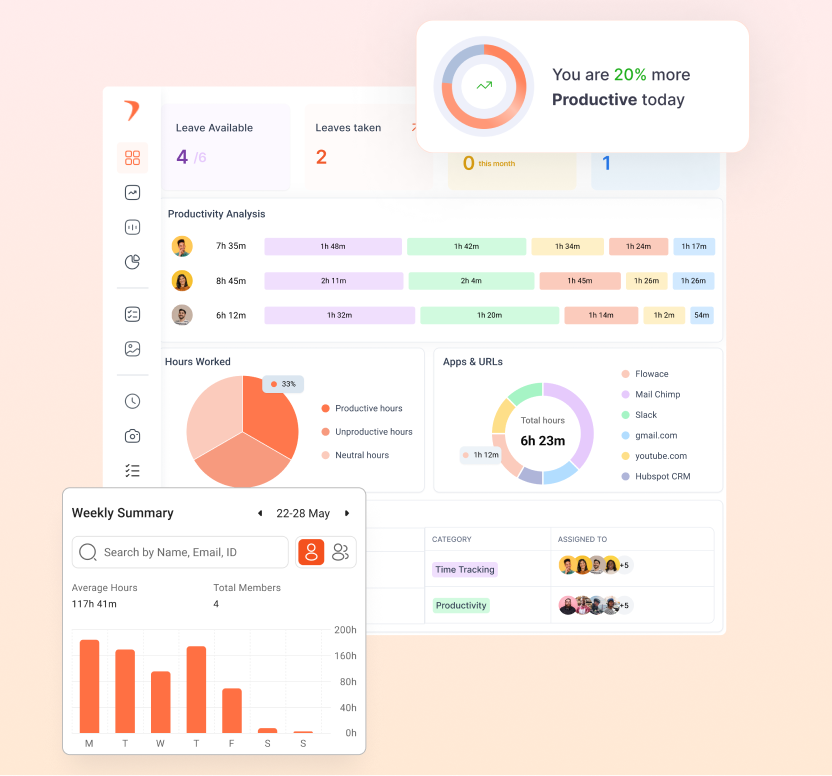
Clarifying the Purpose
Before rolling out any kind of monitoring, ask yourself: Why are we doing this? If the answer is “to keep tabs on employees”, then stop right there; that’s the fastest way to destroy morale. Employee monitoring should always have a clear business purpose, whether it’s ensuring data security, improving efficiency or complying with regulations.
Be upfront with employees about why monitoring is necessary. Are you using time-tracking to streamline project management? Security monitoring to prevent data leaks? Understanding the purpose makes it easier for employees to accept monitoring rather than feel watched. The clearer you are about intent, the less resistance you’ll face.
Defining What & How to Monitor
Employees don’t like feeling like they’re under a microscope, and for good reason. That’s why your policy needs to spell out exactly what’s being monitored and how. Will it be work emails? Internet activity? GPS tracking for field employees? The more precise you are, the fewer misunderstandings there will be.
Make sure monitoring is reasonable. Tracking work-related activities? Fair. Logging keystrokes and watching employees through webcams? Creepy. Employees should always know what data is being collected and how it’s being used. If they don’t, the first time they find out might be when a manager calls them in for “not working hard enough”, and that’s how trust breaks down.
Data Usage and Access
Now that you’re collecting data, the next question is: Who has access to it, and how is it being used? This is where companies often slip up. It’s one thing to track data for security reasons, but if managers start using it to micromanage employees’ every move, things will go south fast.
Your policy should clearly state: Who can see the data (HR? IT? Direct managers?) What it will be used for (Performance tracking? Compliance? Security?) How long it will be stored (Is old data deleted regularly?)
Employees should never feel like their personal space is invaded, and no one should be snooping into data that’s irrelevant to their job. Keep access limited and ensure that data isn’t being used to punish employees unnecessarily.
Policy Scope and Applicability
Every policy needs to be crystal clear about who it applies to. Does it cover all employees or just specific teams? Are remote workers monitored differently? Are company-owned devices tracked differently than personal ones? These details matter.
For instance, if you’re monitoring only company devices, clarify that personal devices are off-limits. If remote employees are subject to different tracking, state exactly how that works. Employees should never be surprised by what’s being monitored.
Think of it this way: a good monitoring policy should answer all the “what-ifs” before an employee asks them. The more thorough and transparent it is, the less room there is for confusion.
Including an FAQ Section
No matter how detailed your policy is, employees will always have questions and concerns. That’s why adding an FAQ section is a great way to address common doubts upfront.
For example: “Will my personal emails be monitored?” – No, only work emails sent through company accounts. “Can I be tracked when I’m off duty?” – No, monitoring applies only during work hours. “What happens if I accidentally visit a non-work-related site?” – Reasonable personal browsing is fine; excessive distractions will be addressed through coaching, not punishment.
An FAQ section shows employees that you understand their concerns and are addressing them openly. It humanizes the policy, making it feel less like a rulebook and more like a guide to a fair workplace.
Implementing Best Practices & Oversight
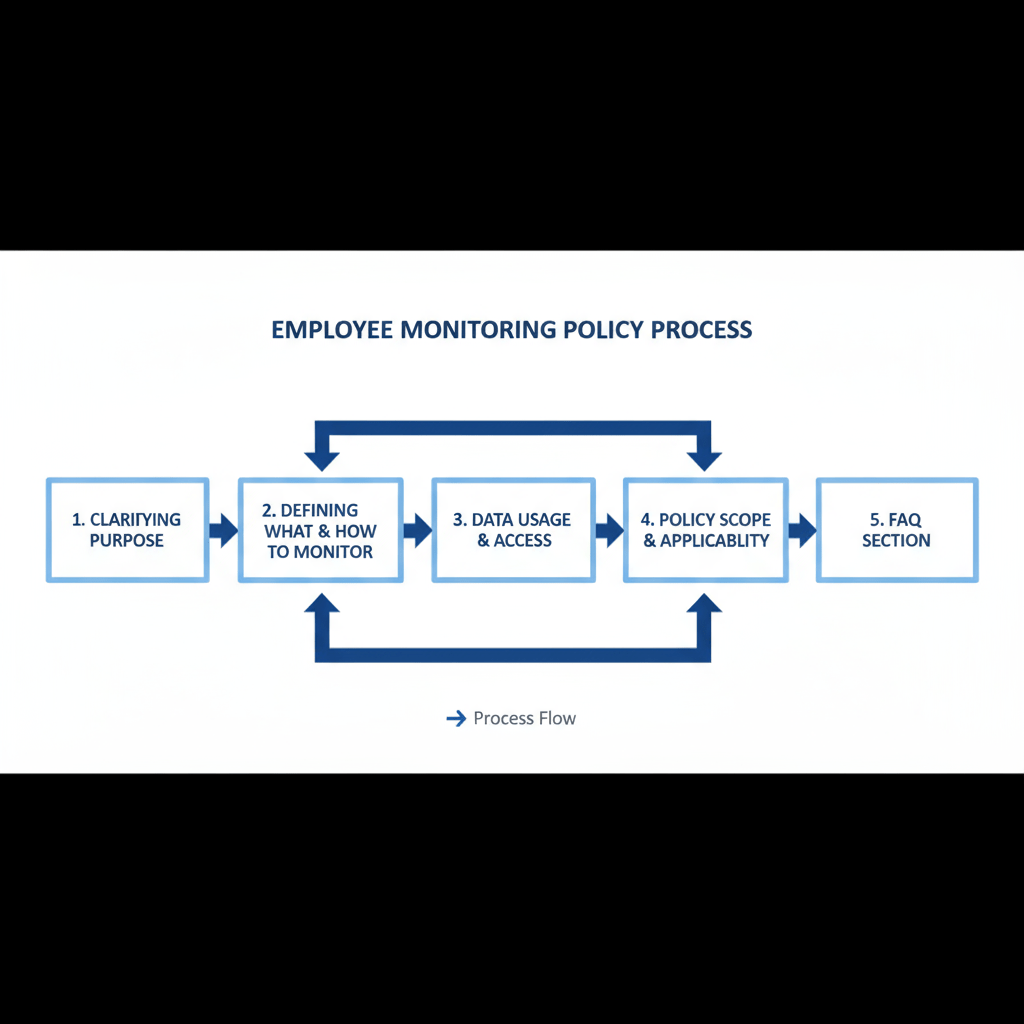
Pre-Implementation (Week 1–2)
The first stage focuses on laying the groundwork for a legally compliant and operationally sound employee monitoring program. During this phase, the company must conduct a thorough legal review and compliance check. This involves identifying all jurisdictions where employees work and mapping the intended monitoring activities, such as email, internet usage, keystroke logging, or audio/video recordings, against relevant federal and state statutes, including wiretap laws, the Electronic Communications Privacy Act (ECPA), and state-specific data protection laws.
Any high-risk areas should be flagged, and guidance should be provided for necessary consent language and data retention policies. Simultaneously, a draft policy document should be prepared by HR and legal teams, clearly outlining the purpose, scope, monitoring methods, data usage, retention timelines, and employee rights.
This draft should be reviewed and refined to include company-specific examples and practical scenarios. Finally, the policy must undergo a formal stakeholder approval process, involving HR leadership, legal counsel, IT security, and executive management. This ensures that all key decision-makers understand and endorse the policy, and that any concerns regarding privacy, operational impact, or employee relations are addressed before the program begins.
Implementation (Week 3–4)
Once the pre-implementation groundwork is complete, the focus shifts to effectively communicating the policy to employees, collecting necessary consent, and configuring monitoring systems. The first step in this stage is employee notification.
All staff should receive formal notice through email, intranet postings, or other internal communications, detailing what monitoring activities will occur, why they are necessary, how the collected data will be used, and who will have access.
These communications should be supported by clear and accessible FAQs, and live Q&A sessions should be offered to ensure employees can seek clarification. Alongside notification, comprehensive training should be provided for both employees and managers. Training modules should explain the monitoring tools and practices, emphasize privacy and ethical use, and provide guidance on raising concerns.
Employees should acknowledge completion, ideally through a brief quiz or digital acknowledgment form, which ensures understanding of the policy.
The next focus is on collecting employee consent. HR teams must ensure that each employee signs a consent form, either digitally or in writing, documenting their acknowledgment of and agreement to the monitoring activities outlined in the policy. This consent should be tracked carefully, with a system in place to follow up with any non-responders.
In parallel, IT and security teams are responsible for system setup, configuration, and testing. Monitoring software must be installed in pilot groups first, and all functionalities should be validated to ensure that the data collected aligns strictly with the policy. Security controls, such as role-based access, encryption, and retention policies, must be implemented, and any pilot feedback should be addressed before full deployment.
Once the system is verified in the pilot phase, full deployment can occur, ensuring that every in-scope employee has been notified, trained, and has provided consent.
Post-Implementation (Ongoing)
After the system is live, continuous oversight is critical to ensure compliance, address employee concerns, and improve operational effectiveness. Regular policy reviews should be scheduled to reassess the policy’s alignment with changing laws, technological updates, or operational needs. These reviews should involve HR, legal counsel, and IT security, and the policy must be updated and republished when necessary.
Compliance audits should be conducted periodically to verify that consent records are complete, data retention and access rules are enforced, and monitoring logs are properly maintained. Any discrepancies or violations should be documented and remediated promptly. Employee feedback mechanisms, such as surveys or dedicated reporting channels, should be maintained to capture concerns and suggestions. These inputs should be logged, investigated, and addressed transparently.
Additionally, metrics and KPIs should be tracked to assess the effectiveness of the monitoring program. This includes monitoring consent coverage, training completion rates, and the frequency of access requests or complaints. Technical maintenance is equally important, ensuring that monitoring software remains updated, secure, and compliant with vendor and internal standards.
Finally, processes for handling employee data requests or grievances should be clearly documented and executed within defined timelines, reinforcing trust and compliance. A continuous improvement loop should be established where audit findings, feedback, and metrics inform refinements to policies, communications, and system configurations.
This ongoing cycle ensures that the monitoring program remains effective, transparent, and legally compliant while respecting employee privacy.
International Compliance Section

Creating an ethical employee monitoring policy for a global workforce requires attention to data privacy laws in every country of operation. Compliance not only meets legal obligations but also builds employee trust.
GDPR (EU)
Employee monitoring is considered personal data processing. Organizations must have a clear purpose, limit data collection, provide transparency, obtain a lawful basis, and implement strong safeguards. Employees have the right to access, correct, restrict, or object to their data. Non-compliance can result in significant fines and reputational risk.
PIPEDA (Canada)
Monitoring must be reasonable and proportionate. Employees must be informed of what data is collected and why. Consent is required for intrusive monitoring, and safeguards must be in place. Employees can request access or corrections, with violations reviewed by the Privacy Commissioner.
Australia Privacy Act
Employers must manage personal data transparently, provide clear notice, and ensure data security. Employees have the right to access and correct their information, and state-level workplace surveillance rules may also apply.
Data Localization
Some countries, like Russia, China, and certain EU states, require employee data to be stored locally. Cross-border transfers must comply with legal frameworks such as GDPR Standard Contractual Clauses.
In short, ethical international monitoring policies combine transparency, legal compliance, and strong safeguards, fostering trust while reducing regulatory risk.
Conclusion
Flowace is one of the best time tracking tool that helps businesses implement fair, non-intrusive monitoring without making employees feel watched. Flowace allows organizations to clearly define and communicate what’s being tracked. With its self-tracking features, employees can see their own work patterns, time logs, and productivity insights. This eliminates the fear of hidden surveillance, making monitoring feel more like a self-improvement tool rather than a control mechanism.
Instead of micromanaging every keystroke or mouse movement, Flowace focuses on measurable productivity metrics. Its robust productivity tracking capabilities help businesses monitor work hours, project progress, and efficiency, ensuring that monitoring is about enhancing performance rather than nitpicking behaviors.
With automatic time tracking, Flowace gives employees the ability to review their own performance data and make adjustments where necessary. This empowers employees to take ownership of their productivity rather than feeling like they’re being constantly policed.
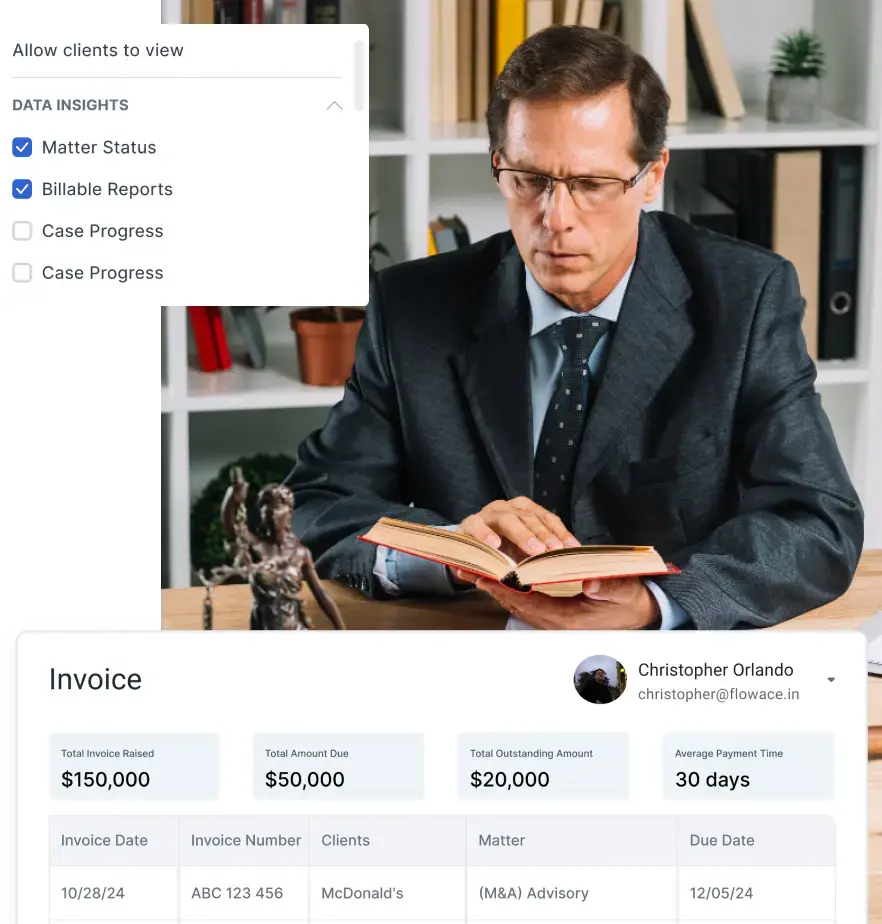
Different businesses have different monitoring requirements, and Flowace offers customizable tracking settings. Whether it’s light-touch monitoring for a creative team or detailed tracking for a compliance-heavy industry, companies can set the right level of monitoring that aligns with their ethical policies.
Flowace is also widely regarded as the best time tracking tool for marketing agencies, especially those managing remote teams, tight campaign deadlines, and multiple client projects. It provides marketing leaders with visibility into task timelines and performance without resorting to invasive tactics.
Sign up for a free trial today to see these features in action. Our team will help you set up seamlessly and give you a head start.
Related Articles
- Employee Monitoring: Complete Guide 2025
- How to Choose Employee Monitoring Software
- 9 Ways Employees Fool Monitoring Software
- Employee Monitoring Data Protection Guide
- How Employee Monitoring Software Works & Matters
- What is Employee Task Tracking? Complete Guide
- Best Employee Monitoring Software 2025
- Employee Idle Time Tracking Software Guide
- Employee Monitoring Best Practices 2025
- Employee Monitoring Laws: Legal Guide 2025
- Remote Team Monitoring: Perspectives & Insights
- Employee Monitoring Statistics 2025
- Performance Monitoring: Benefits & Concerns
- Employee Monitoring Myths Debunked
- Employee Wellbeing Monitoring Solutions