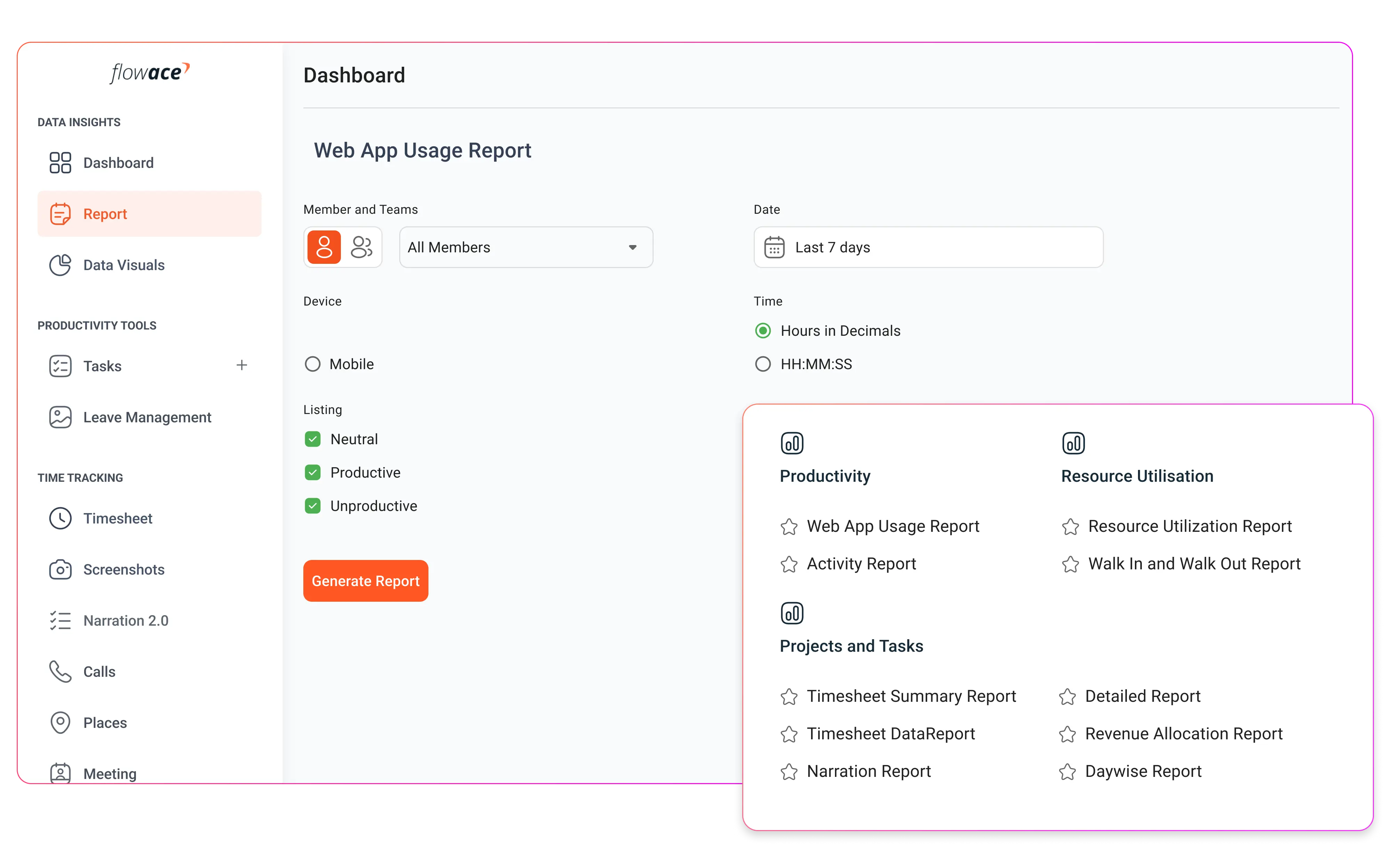
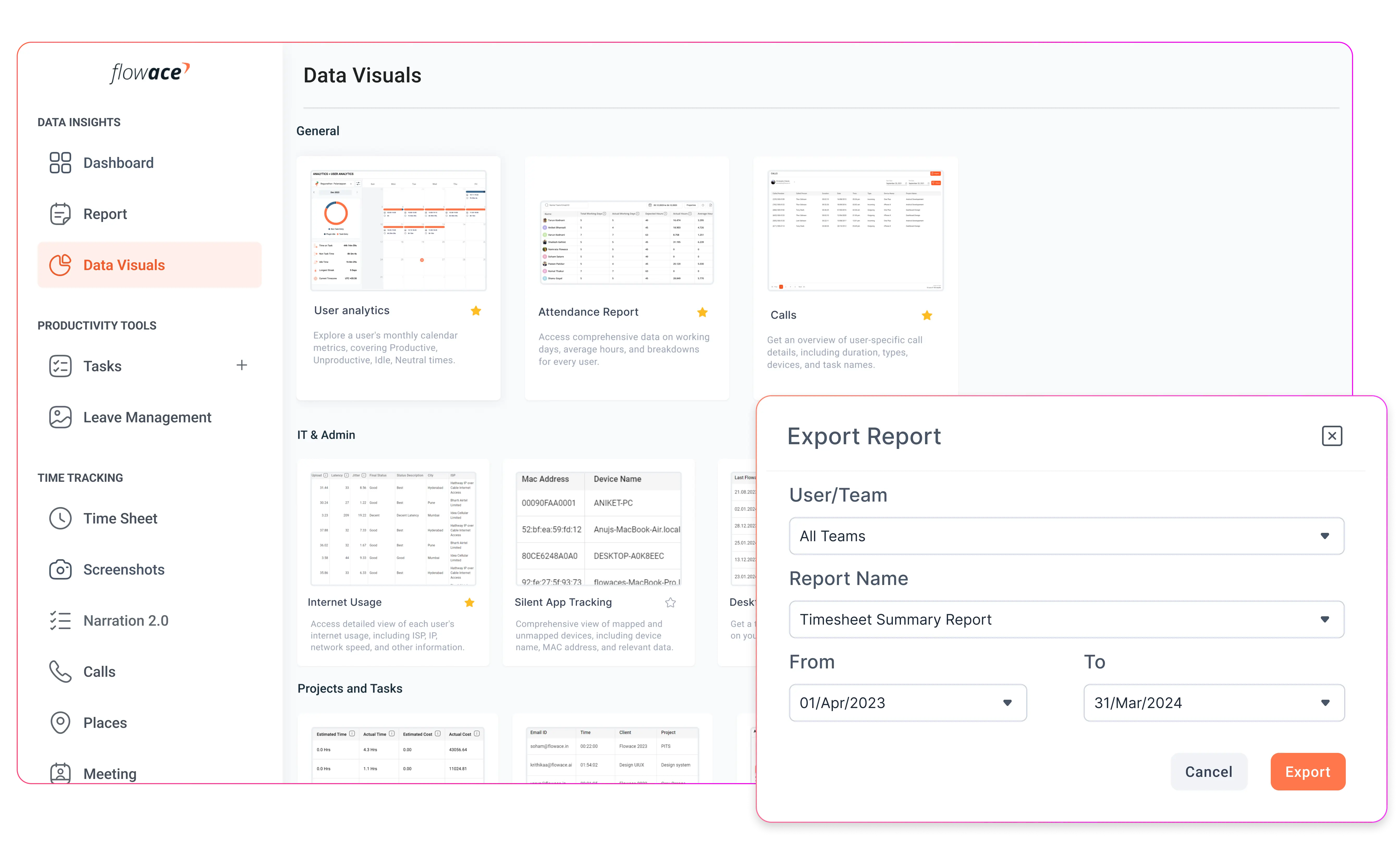
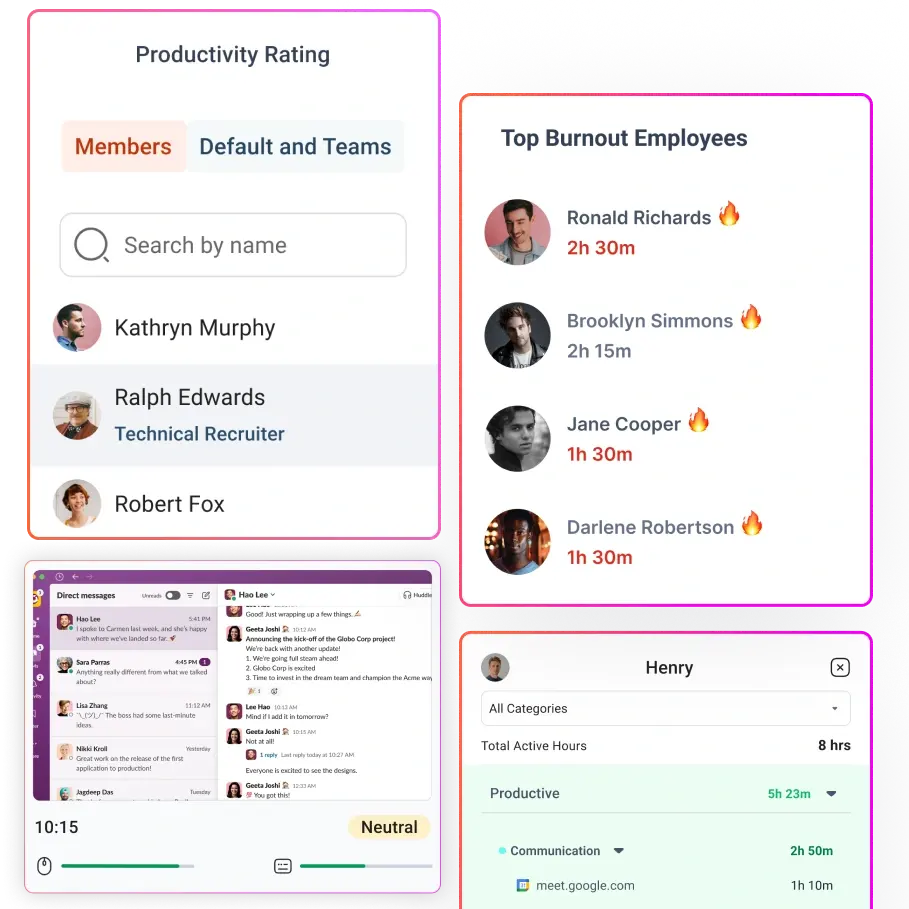
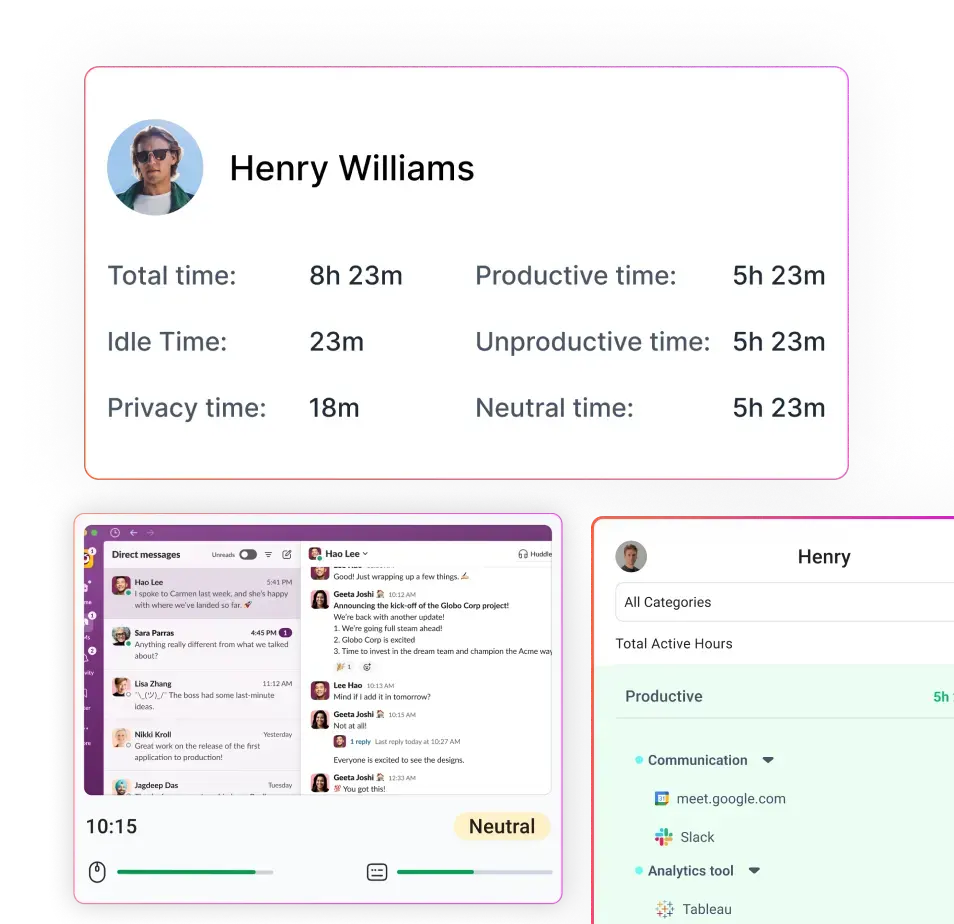
What is Stealth Employee Monitoring Software?
These days when every action leaves a digital footprint, businesses are seeking smarter and more precise ways to oversee operations without disrupting daily workflows. Stealth monitoring software provides exactly that. It delivers silent, continuous tracking that operates in the background, giving managers real-time visibility without alerting employees or interfering with their tasks.
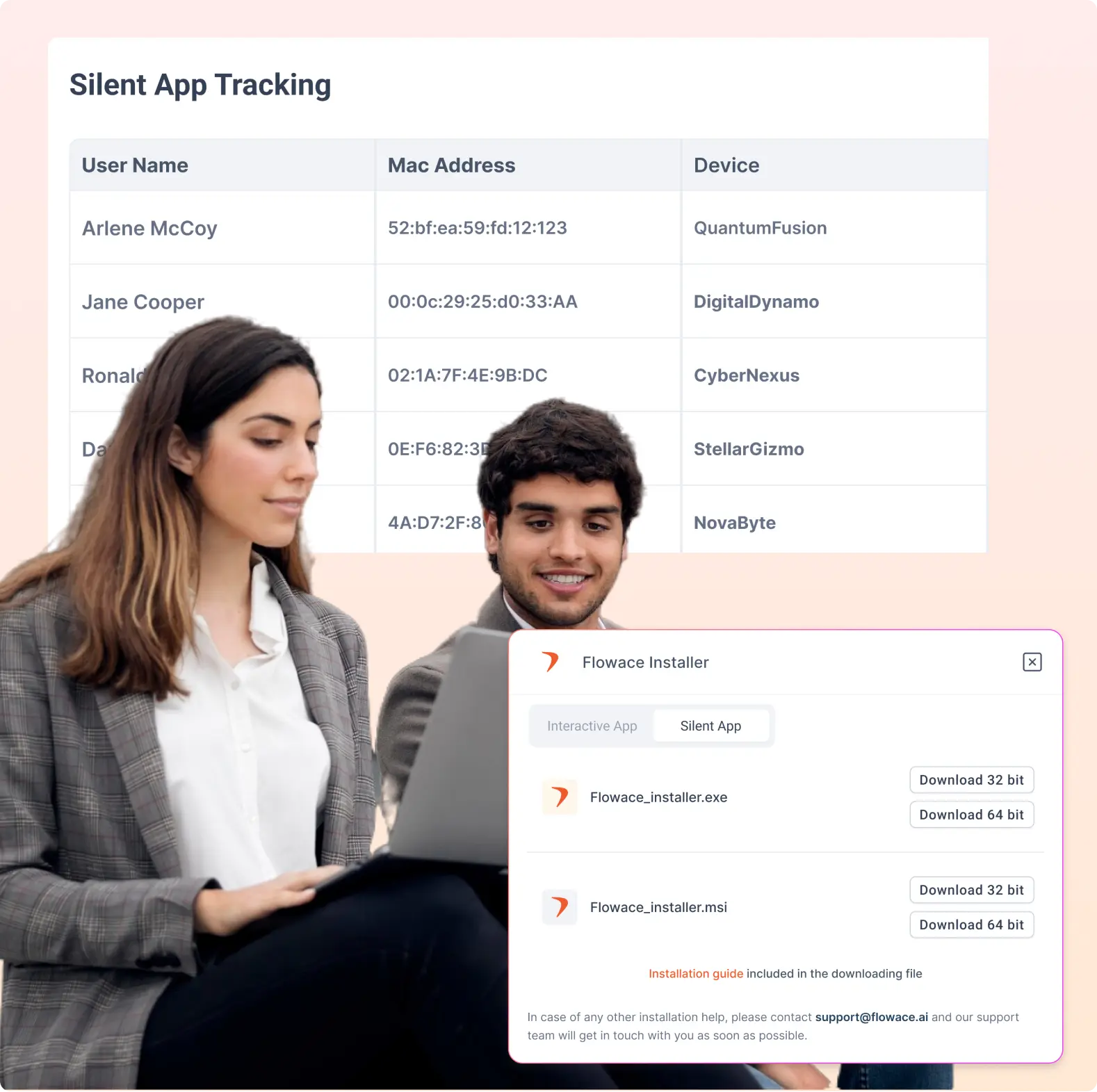
Unlike traditional monitoring tools that display visible indicators or require active participation, stealth employee monitoring software runs undetected on company devices. It automatically records essential activity such as application usage, website visits, work hours, and productivity patterns. This ensures managers have accurate and unfiltered data to guide operational and strategic decisions, while avoiding the artificial behaviors that often occur when employees know they are being watched.
Well-designed stealth monitoring software is not about micromanaging. It is about precision management and creating a complete picture of how work is actually being done. By operating quietly, it captures authentic workflows, detects potential risks, and supports compliance requirements without interrupting productivity. In industries where accuracy, security, and accountability are critical, this silent and reliable tracking method has become an indispensable asset for modern organizations.
Types of Businesses That Benefit from Stealth Monitoring
Stealth monitoring software can be valuable for almost any organization, but certain industries and work environments see the highest return on investment from its use. By providing discreet oversight and accurate activity data, it helps businesses address specific operational challenges while improving efficiency and accountability.
Remote and Hybrid Workforces
Managing productivity without direct, in-person supervision can be difficult. Stealth monitoring software ensures that work is accurately tracked across different time zones and schedules, without requiring constant check-ins or manual reporting.
BPOs and Outsourcing Firms
For companies that bill clients by the hour or by specific deliverables, accuracy is essential. Stealth monitoring software provides verifiable proof of work, supports Service Level Agreement compliance, and helps prevent disputes over billable hours.
IT Services and Cybersecurity Teams
Stealth monitoring software can quietly detect unusual access patterns, data transfers, or other behaviors that could indicate security risks, enabling faster intervention before problems escalate.
Staffing and Recruitment
Recruitment agencies and staffing firms rely on transparent activity data to ensure that candidates are being sourced, screened, and followed up on efficiently. Stealth monitoring helps managers verify recruiter productivity without micromanaging—tracking outreach volume, time spent on sourcing platforms, and engagement patterns. This ensures fair performance evaluation, reduces missed opportunities, and ultimately improves placement success rates.
Healthcare and Compliance-Sensitive Sectors
In highly regulated industries, compliance with standards such as HIPAA, GDPR, or SOC 2 is critical. Stealth monitoring software helps maintain detailed workflow records for audits without interfering with sensitive processes or patient care.
High-Security Operations
Government contractors, defense-related industries, and organizations handling sensitive intellectual property rely on stealth monitoring software to ensure that confidential data remains secure and that any suspicious activity is logged for review.
By working silently in the background, stealth monitoring software gives these businesses a reliable way to maintain performance, protect assets, and meet compliance obligations without creating unnecessary disruption.
Features of Stealth Employee Monitoring Software
The effectiveness of stealth monitoring software comes from its ability to capture detailed and accurate data without interrupting an employee’s workflow. The best solutions combine precision tracking with secure data handling, giving managers valuable insights while protecting sensitive information.
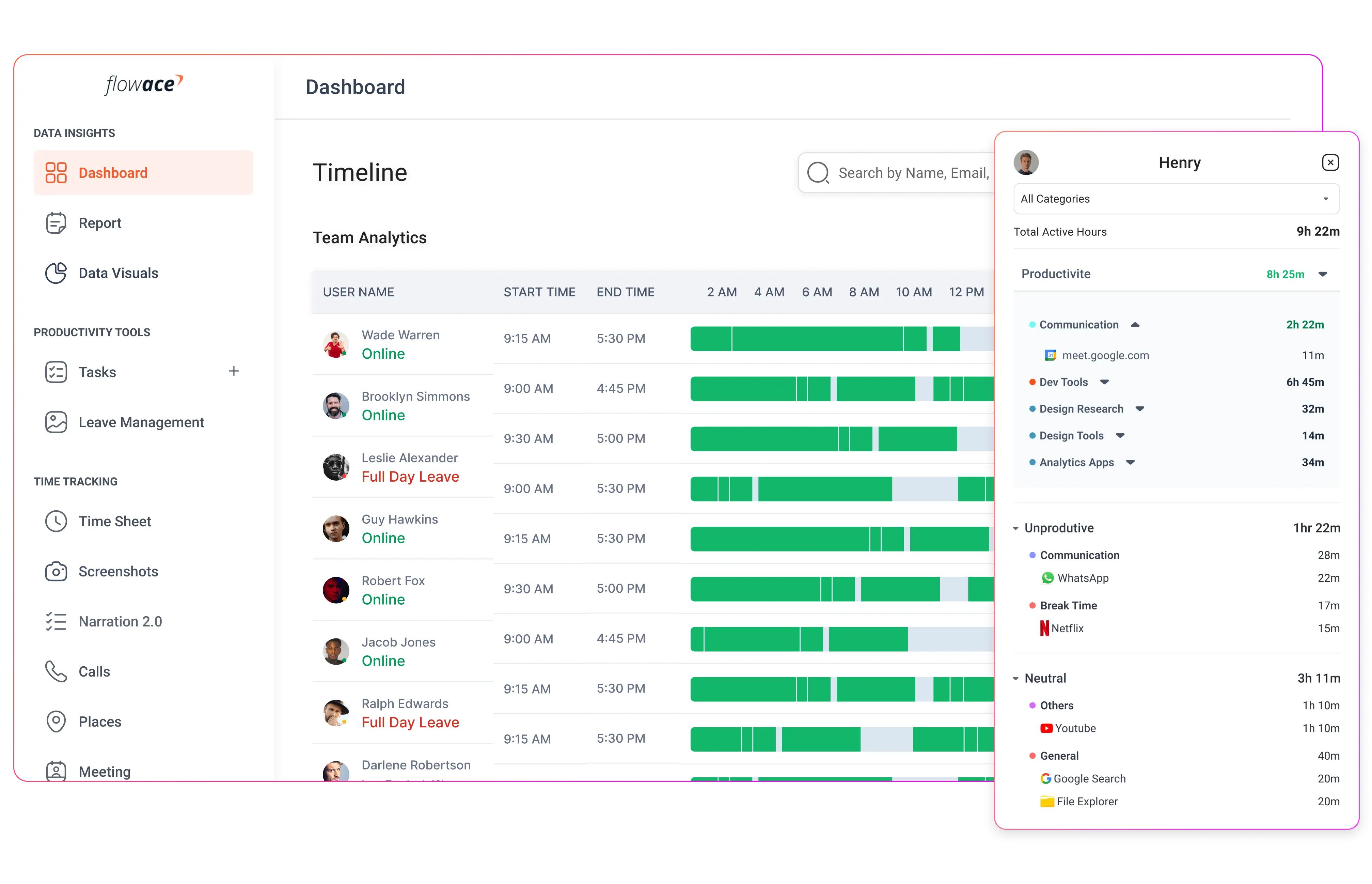
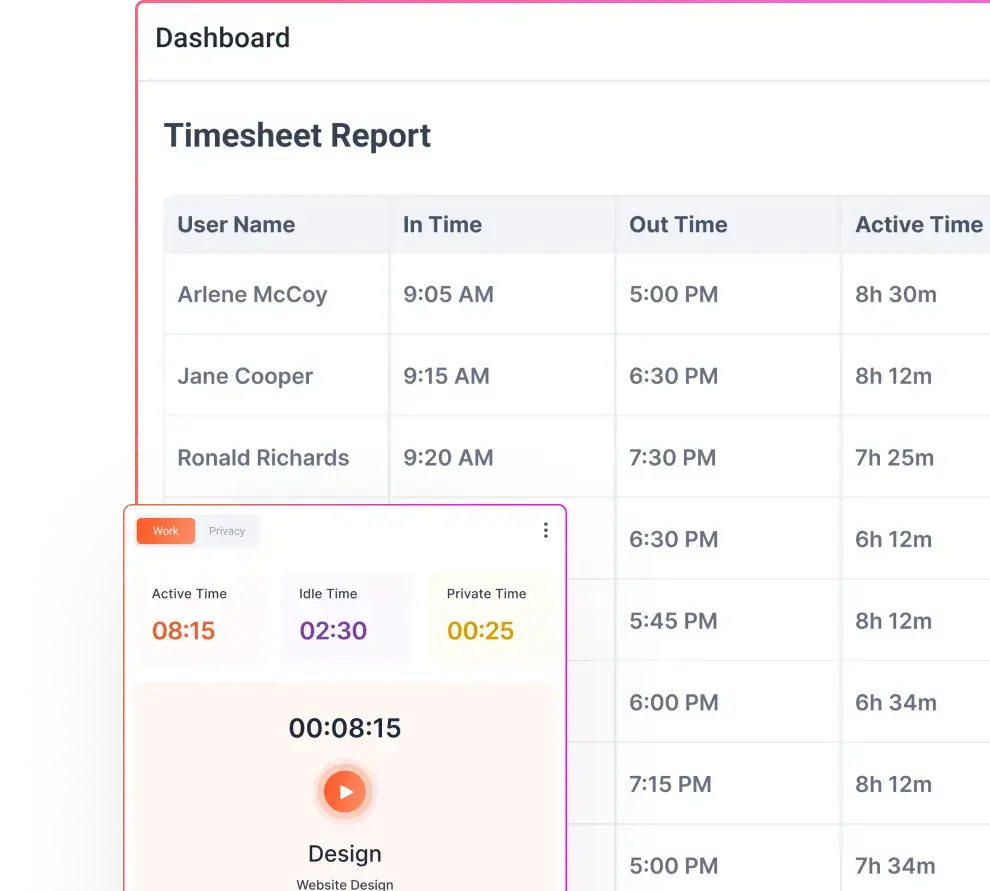
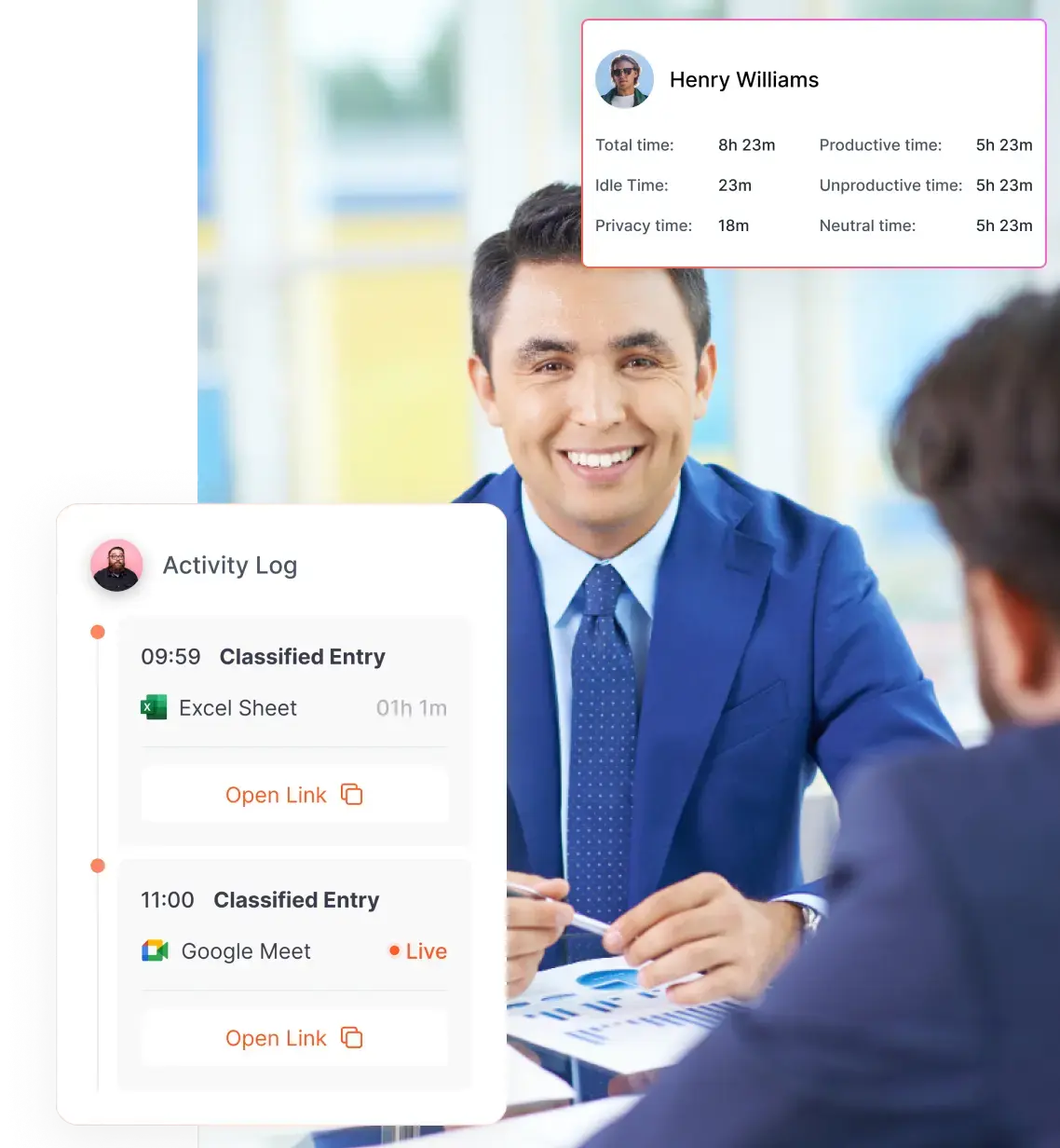
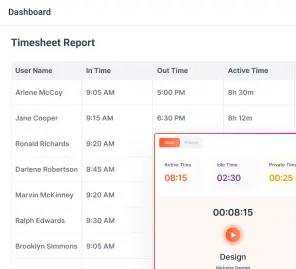
Invisible Time Tracking
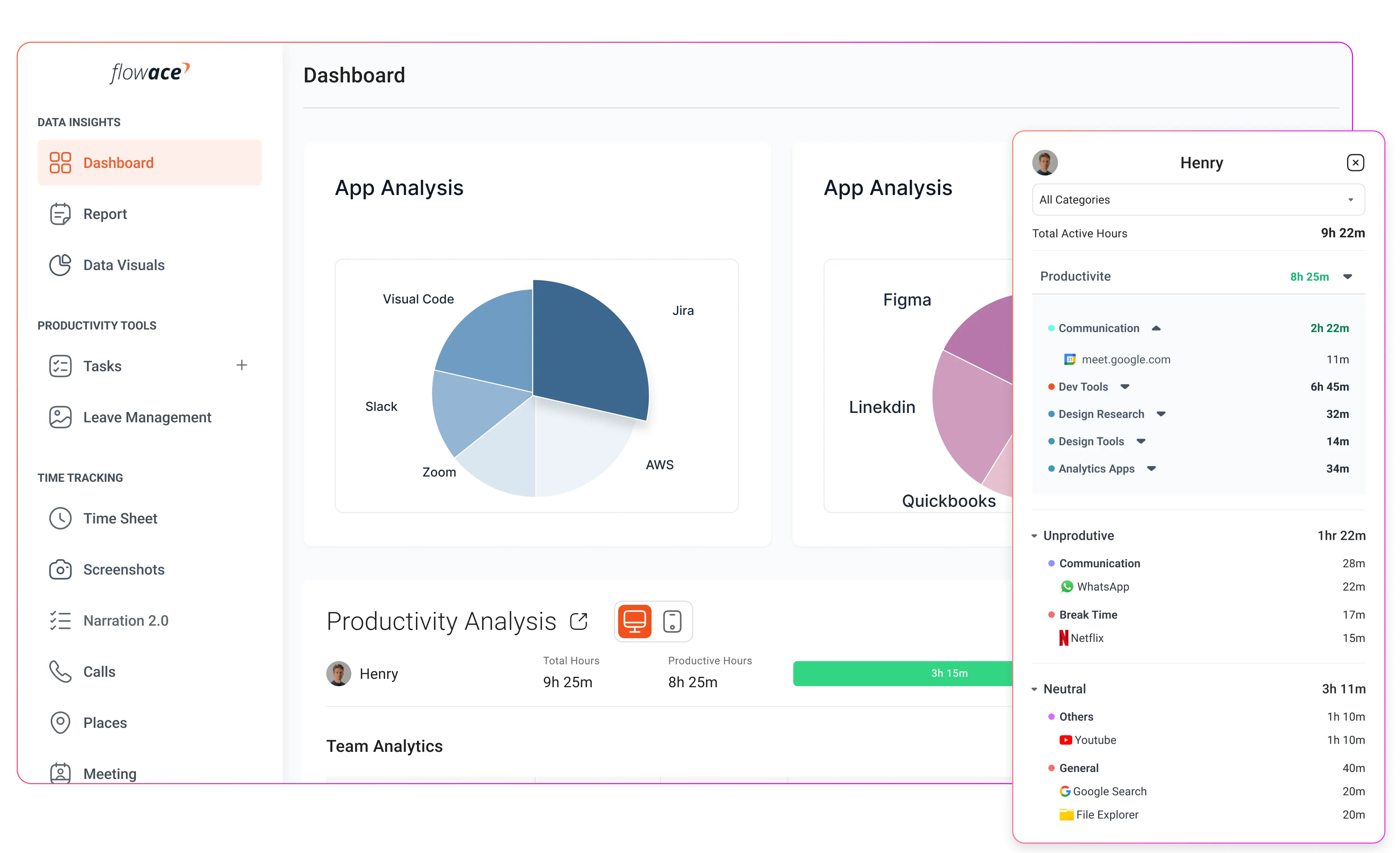
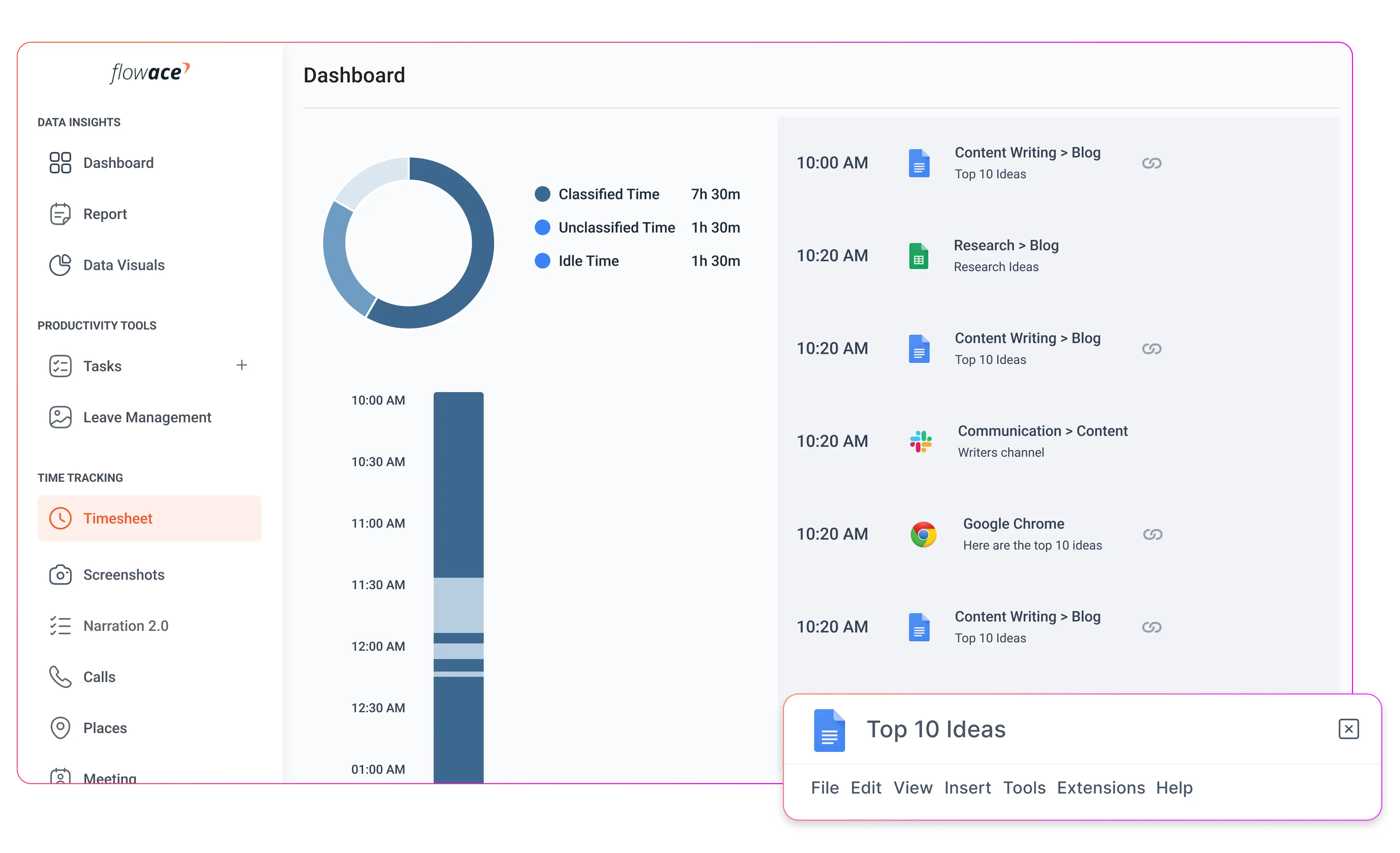
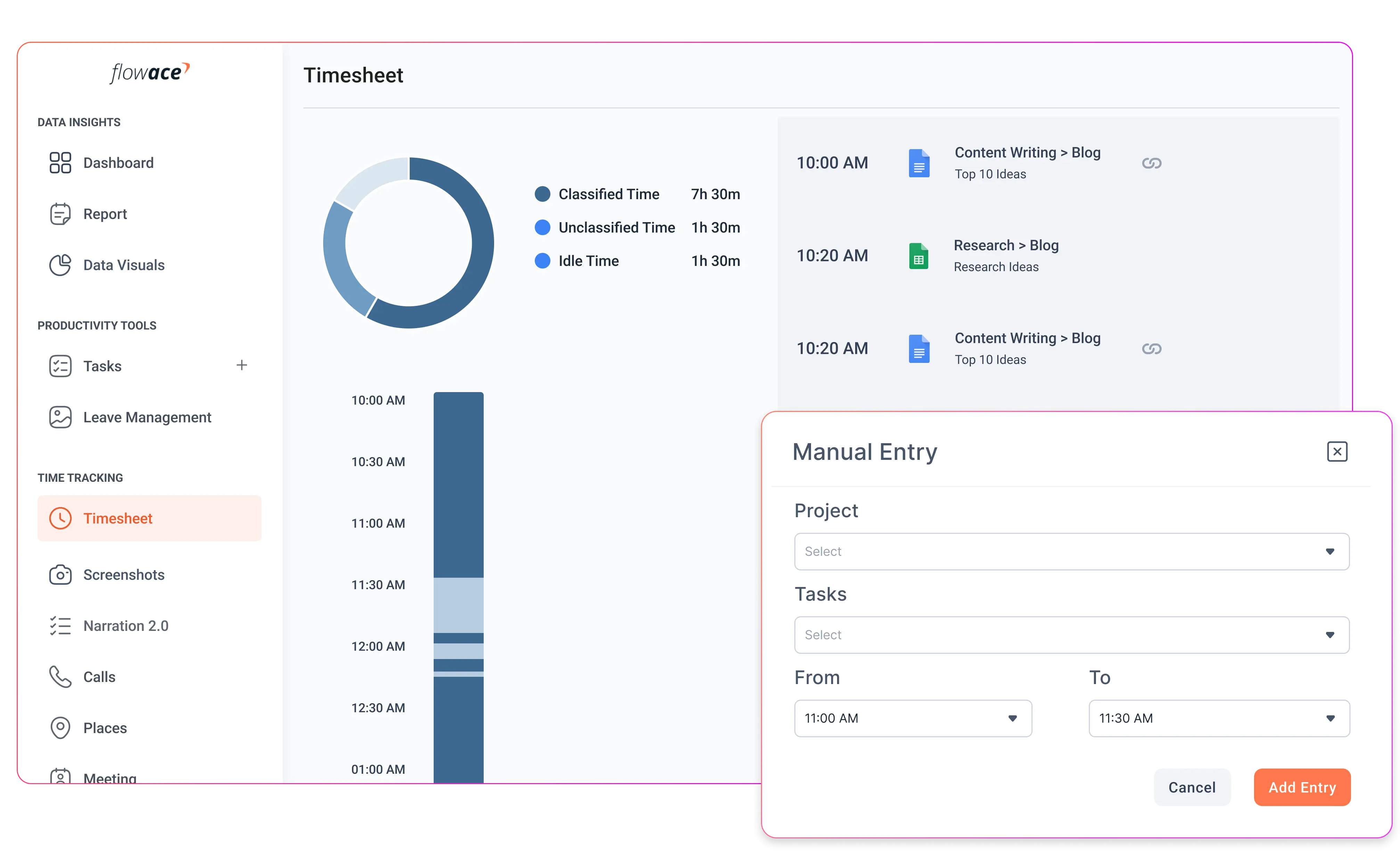
Stealth monitoring software automatically records work hours in the background. There is no need for employees to manually start or stop timers, which eliminates human error and ensures that the time data is accurate and complete.
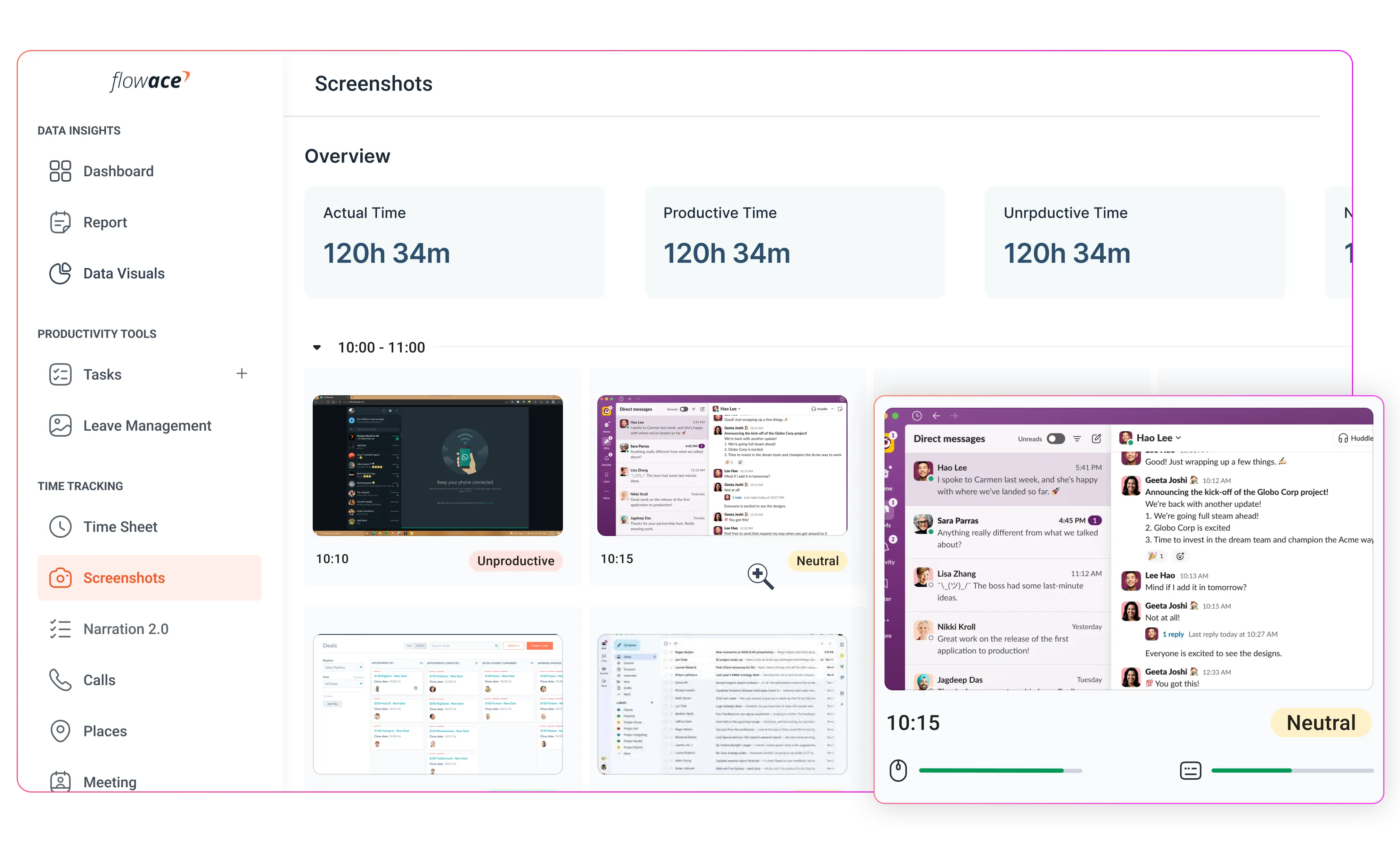
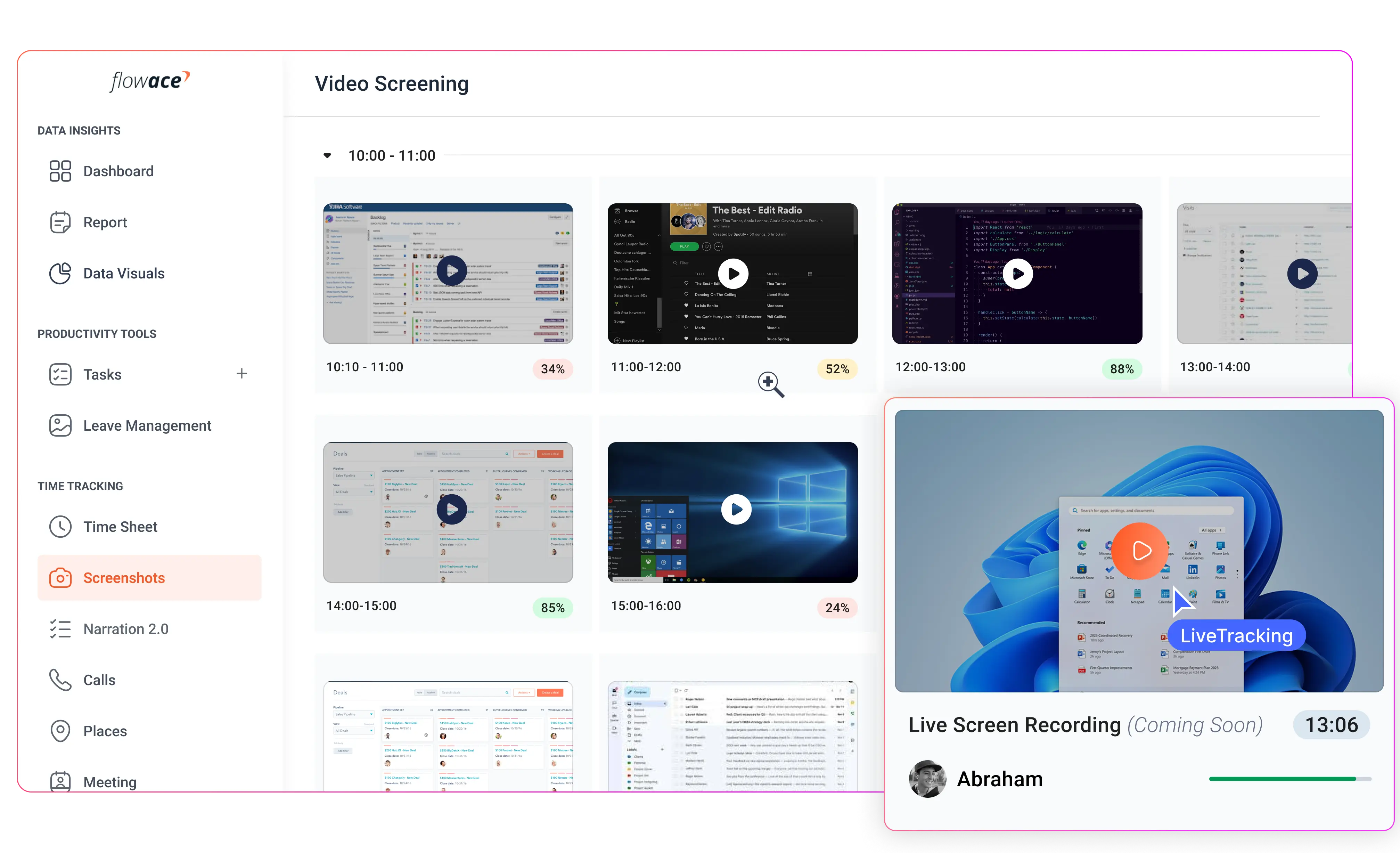
Stealth Screenshots and Screen Recording
Configurable screenshot intervals and optional video playback give managers a clear view of active projects. These features help verify work quality, confirm task completion, and identify potential bottlenecks.
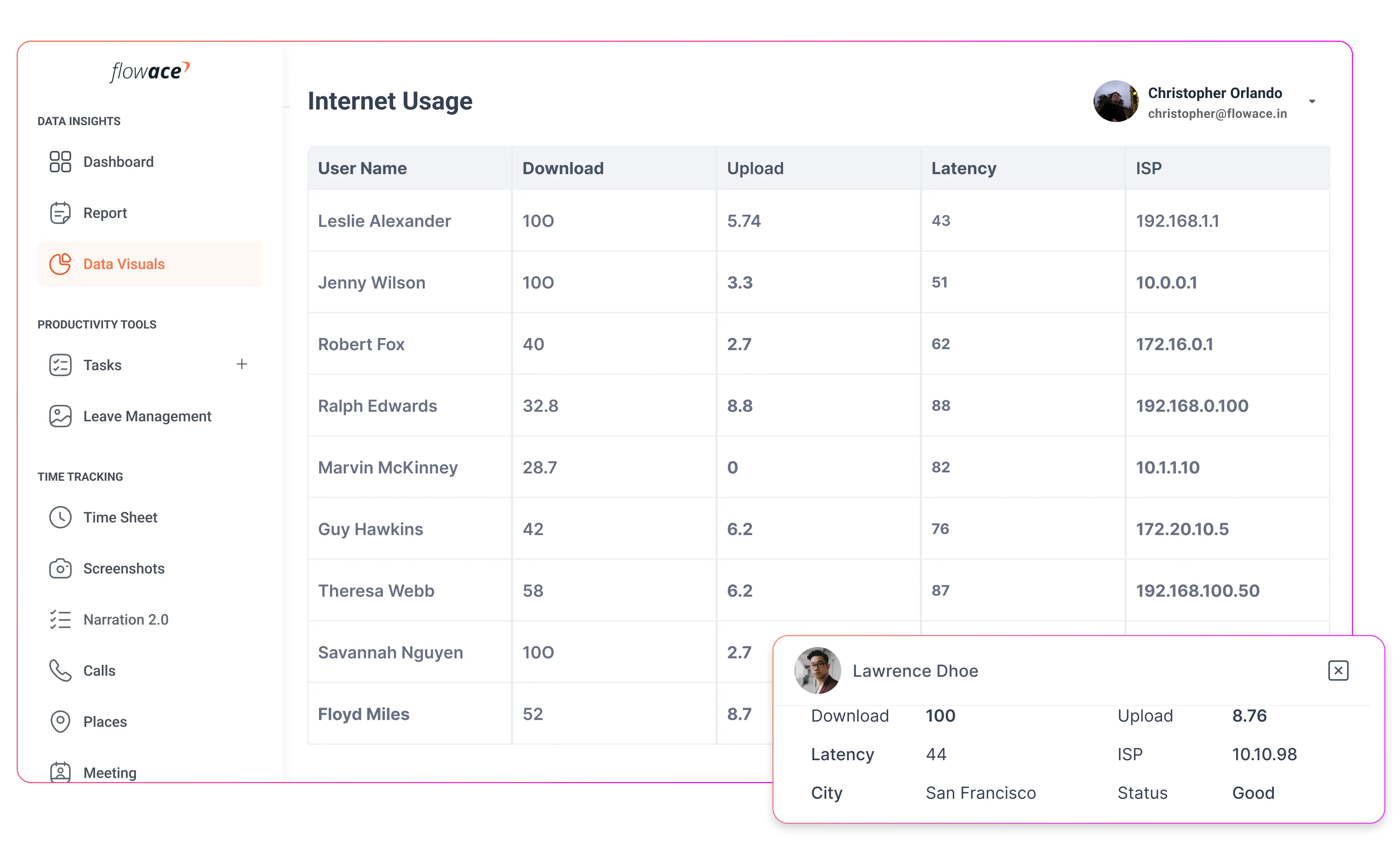
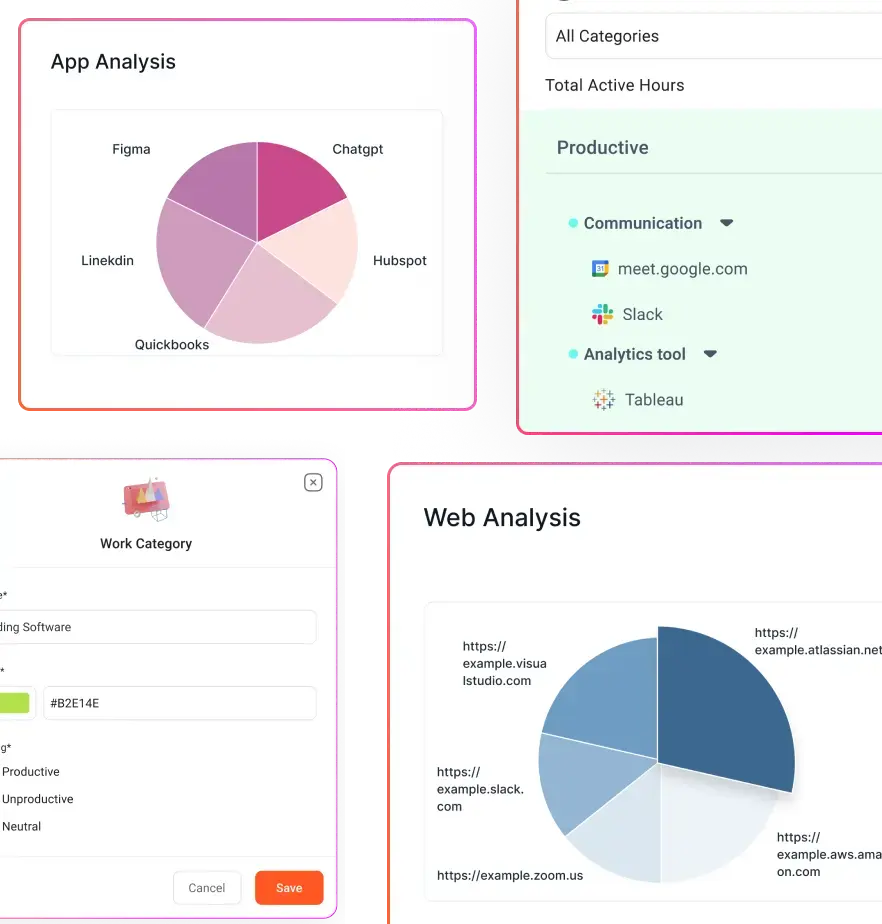
Silent Application and Website Tracking
The software logs which programs and websites are used during work hours, along with the duration of use. This allows managers to distinguish between productive and unproductive activities without drawing attention to the monitoring process.
Idle Time and Activity Level Detection
Stealth monitoring software can detect when a device is inactive, recording idle periods separately from active work time. This helps organizations understand how work is distributed throughout the day.
Keystroke and Input Activity (When Compliant)
In compliance-friendly setups, keystroke frequency and mouse activity can be tracked without storing the actual text typed. This provides a measure of engagement without capturing sensitive or personal data.
Automated Alerts and Triggers
Managers can set rules for detecting unusual behavior, such as large file transfers or access to restricted data. Stealth monitoring software can silently flag these incidents for review, enabling faster responses to potential security issues.
Secure Data Storage
Whether cloud-based or on-premise, stealth monitoring software should offer encryption and role-based access controls. This ensures that monitoring data is only accessible to authorized personnel.
By combining these features, stealth monitoring software delivers precise oversight that strengthens productivity, security, and compliance, all while remaining unobtrusive to day-to-day operations.
Use Cases of Stealth Monitoring
Stealth monitoring software is a versatile tool that can be applied in a wide range of business scenarios. Its ability to operate quietly in the background makes it especially valuable in environments where accuracy, security, and efficiency are priorities. Below are some of the most common and impactful use cases.
Productivity Optimization
Managers can use stealth monitoring software to identify work patterns and assess how time is spent across teams. This allows businesses to streamline workflows, reduce inefficiencies, and allocate resources more effectively without disrupting employee focus.
Security and Insider Threat Detection
By tracking system access, file transfers, and application usage, stealth monitoring software can detect behaviors that indicate potential security risks. Since the monitoring is silent, it does not alert malicious actors, giving security teams time to respond before damage occurs.
Compliance Auditing
Industries with strict regulations, such as healthcare, finance, and legal services, benefit from the detailed records generated by stealth monitoring software. These records provide an auditable trail for compliance checks and help demonstrate adherence to industry standards.
Remote Team Management
For distributed teams, stealth monitoring software offers visibility into productivity and task completion without the need for constant check-ins. This supports flexible work arrangements while maintaining accountability.
Process Improvement Initiatives
The data collected by stealth monitoring software can be analyzed to identify workflow bottlenecks, inefficient tool usage, or repetitive manual tasks. These insights help guide process automation and operational improvements.
Whether the goal is improving productivity, strengthening security, or ensuring compliance, stealth monitoring software delivers the accurate and actionable data needed to make informed business decisions without interfering with day-to-day operations.
Importance of Stealth Monitoring Software
In an era where work happens across offices, homes, and global locations, having a clear and accurate view of operations is no longer optional. Stealth monitoring software plays a critical role in enabling businesses to maintain productivity, protect sensitive information, and stay compliant with regulations, all without disrupting the natural flow of work.
One of the most important benefits of stealth monitoring software is the authenticity of the data it captures. When employees know they are being monitored in a visible way, their behavior can change, sometimes leading to skewed performance metrics. Stealth monitoring software removes this influence by working silently in the background, allowing managers to see genuine workflows and make decisions based on real patterns.
From a security perspective, stealth monitoring software is essential for detecting potential threats before they escalate. Whether it is unauthorized file transfers, unusual login activity, or inappropriate use of company resources, silent tracking ensures these incidents are flagged discreetly and addressed promptly.
Compliance is another key area where stealth monitoring software proves its value. Many industries require detailed records of activity for audits and legal protection. Stealth monitoring ensures that this information is collected automatically and stored securely, reducing the administrative burden on teams while providing a reliable audit trail.
In short, stealth monitoring software is not simply a productivity tool. It is a strategic business asset that empowers organizations to operate with greater efficiency, tighter security, and stronger compliance oversight. By delivering actionable insights without creating unnecessary friction in the workplace, it supports both business performance and operational integrity.
Challenges in Using Stealth Monitoring Software
While stealth monitoring software offers clear advantages in productivity, security, and compliance, it is not without its challenges. Businesses considering its implementation must be aware of these factors to ensure a smooth and ethical rollout.
Legal Compliance
Laws regarding digital monitoring vary widely by country and, in some cases, by state or region. Before deploying stealth monitoring software, organizations must review relevant labor laws, privacy regulations, and consent requirements to ensure compliance. In some jurisdictions, even silent monitoring may require clear disclosure to employees.
Privacy Concerns
Although stealth monitoring software focuses on work-related activity, there is always a risk of capturing personal information if employees use company devices for personal tasks. Without proper safeguards and access controls, this can raise privacy concerns and impact employee trust.
Data Security Risks
The detailed records generated by stealth monitoring software can include sensitive business and operational data. If not stored securely, this information could become a target for cyberattacks. Encryption, role-based access, and secure storage solutions are critical to mitigating these risks.
Cultural Resistance
Some employees may react negatively if they discover monitoring was conducted without their knowledge, even if it was legal and justified. This can lead to morale issues, reduced trust in leadership, and potential public relations challenges if not managed carefully.
Implementation Complexity
Choosing the right stealth monitoring software is only the first step. Businesses must also ensure proper configuration, integration with existing systems, and training for managers who will interpret the data. Poor setup can lead to incomplete or misleading insights.
By anticipating these challenges and addressing them proactively, organizations can maximize the benefits of stealth monitoring software while minimizing potential downsides. A responsible and well-planned approach ensures that monitoring strengthens the business without compromising legal, ethical, or cultural standards.
How to Choose the Right Stealth Monitoring Software
Selecting the right stealth monitoring software requires careful evaluation. The goal is to find a solution that delivers accurate insights, strengthens security, and supports compliance while remaining easy to manage and ethically sound.
Define Your Objectives
Before comparing options, identify the primary reason for implementing stealth monitoring software. Are you aiming to improve productivity, ensure compliance, protect sensitive data, or all of the above? Clear objectives will guide your decision and prevent unnecessary feature overload.
Prioritize Stealth and Accuracy
The main strength of stealth monitoring software is its ability to operate quietly while capturing accurate activity data. Look for solutions that remain completely invisible to the end user while offering precise tracking of time, applications, and websites.
Evaluate Security Measures
Since stealth monitoring software collects sensitive operational data, strong security is essential. Features such as encryption, role-based access controls, and secure cloud or on-premise storage help safeguard the information from unauthorized access.
Check Compliance Capabilities
If your business operates in a regulated industry, make sure the stealth monitoring software can generate the reports and audit logs required for compliance. This includes time-stamped activity records, user-specific data, and long-term storage options.
Consider Ease of Integration
The best stealth monitoring software should work seamlessly with your existing systems. Look for compatibility with your operating systems, project management tools, and authentication protocols.
Assess Reporting and Analytics
Raw data is only valuable if it can be interpreted effectively. Choose a solution with robust reporting and analytics features that transform activity logs into actionable insights for managers and decision-makers.
Review Vendor Reputation and Support
Reliable customer support is essential for troubleshooting, updates, and training. Select a vendor with a proven track record and positive client feedback.
By focusing on these factors, businesses can select stealth monitoring software that meets their needs today while offering scalability and adaptability for the future. The right choice will provide reliable oversight without creating friction in day-to-day operations.
Compliance and Privacy Safeguards
While stealth monitoring software delivers valuable insights, its deployment must be handled with a strong commitment to legal compliance and ethical responsibility. Protecting both the organization and its employees requires a balance between effective monitoring and respect for privacy.
Understand Applicable Laws
Before implementing stealth monitoring software, review all relevant workplace monitoring laws in your jurisdiction. Requirements may vary between countries and even states. In some regions, employee consent or formal notification may be mandatory, while in others silent tracking is permissible under certain conditions.
Define Clear Policies
A written policy outlining the scope, purpose, and limitations of stealth monitoring software can help prevent misunderstandings. Even if monitoring is conducted discreetly, having documented rules protects the company from potential disputes.
Limit Data Collection
To reduce privacy risks, configure stealth monitoring software to collect only data that is necessary for business purposes. Avoid tracking personal accounts, private messages, or activities outside of work hours unless there is a clear and legal reason.
Secure the Data
The activity logs and records generated by stealth monitoring software may contain sensitive information. Encryption, secure servers, and role-based access controls should be in place to ensure that only authorized personnel can review the data.
Prepare for Audits
In regulated industries, the ability to produce accurate historical records is critical. Stealth monitoring software should be configured to store data in a format that meets audit requirements without compromising security.
Maintain Ethical Standards
Even when legal, silent monitoring can create trust issues if mishandled. Organizations should ensure that the use of stealth monitoring software aligns with their values, brand reputation, and workplace culture.
By taking compliance and privacy safeguards seriously, businesses can enjoy the full benefits of stealth monitoring software while minimizing risks. This responsible approach ensures that monitoring strengthens both operational performance and corporate integrity.
Benefits of Stealth Monitoring Software
Implementing stealth monitoring software gives organizations a competitive edge by providing visibility into operations without interrupting workflow. Its silent, precise tracking capabilities bring a range of measurable advantages for businesses of all sizes.
Authentic Productivity Insights
Because stealth monitoring software works in the background, employees are less likely to alter their work habits in response to visible monitoring. This ensures the data reflects genuine work patterns, making performance evaluations and process improvements more accurate.
Enhanced Security Awareness
By capturing activity logs and alerting managers to unusual behavior, stealth monitoring software serves as an early-warning system for potential security breaches. This discreet detection helps prevent data loss, insider threats, and unauthorized access.
Improved Accountability
With detailed time and activity records, teams can be held accountable for their work without the need for constant supervision. This fosters a results-oriented culture while reducing micromanagement.
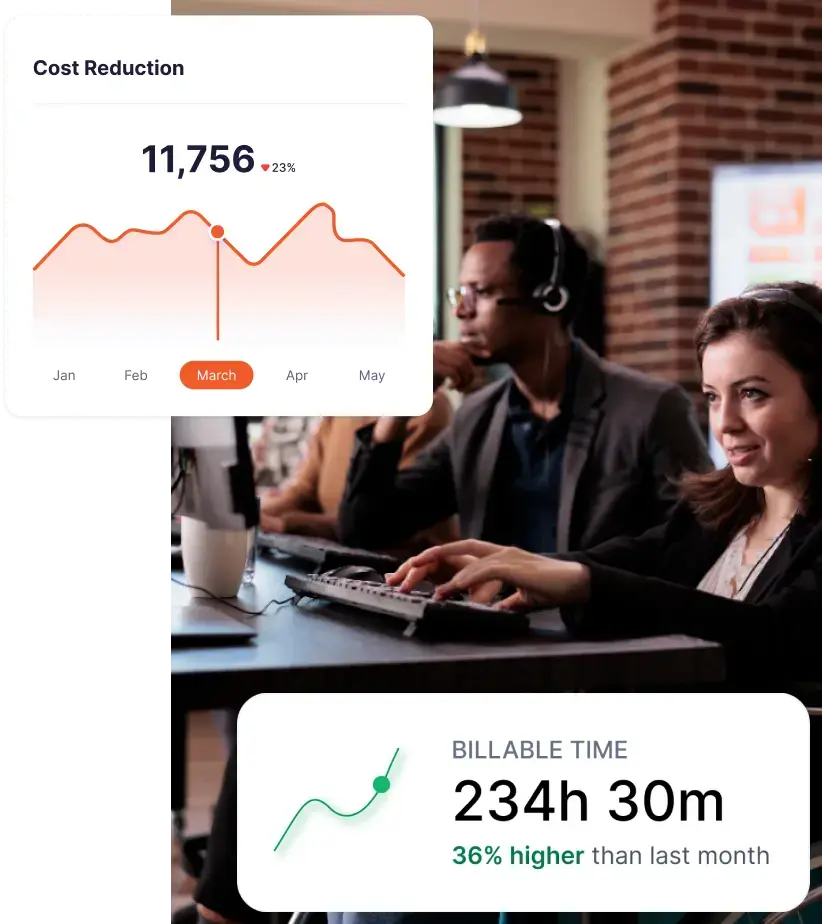
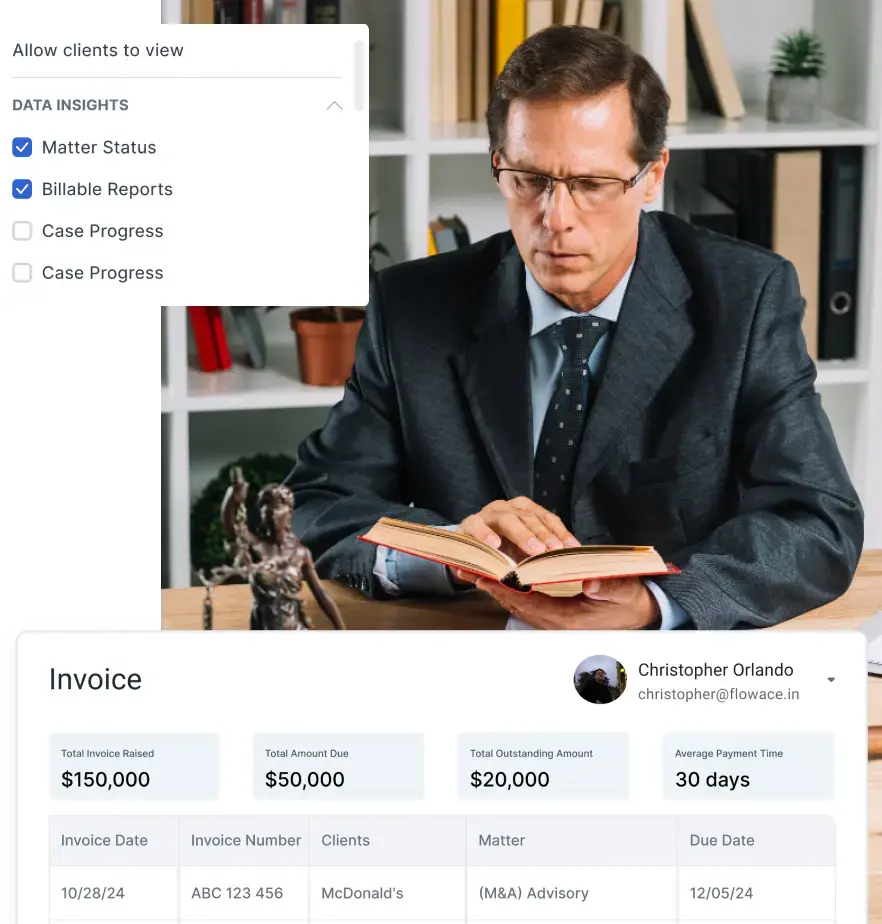
Accurate and Transparent Billing
For service-based companies, stealth monitoring software offers verifiable proof of work that supports precise client billing. This transparency helps maintain strong client relationships and reduces payment disputes.
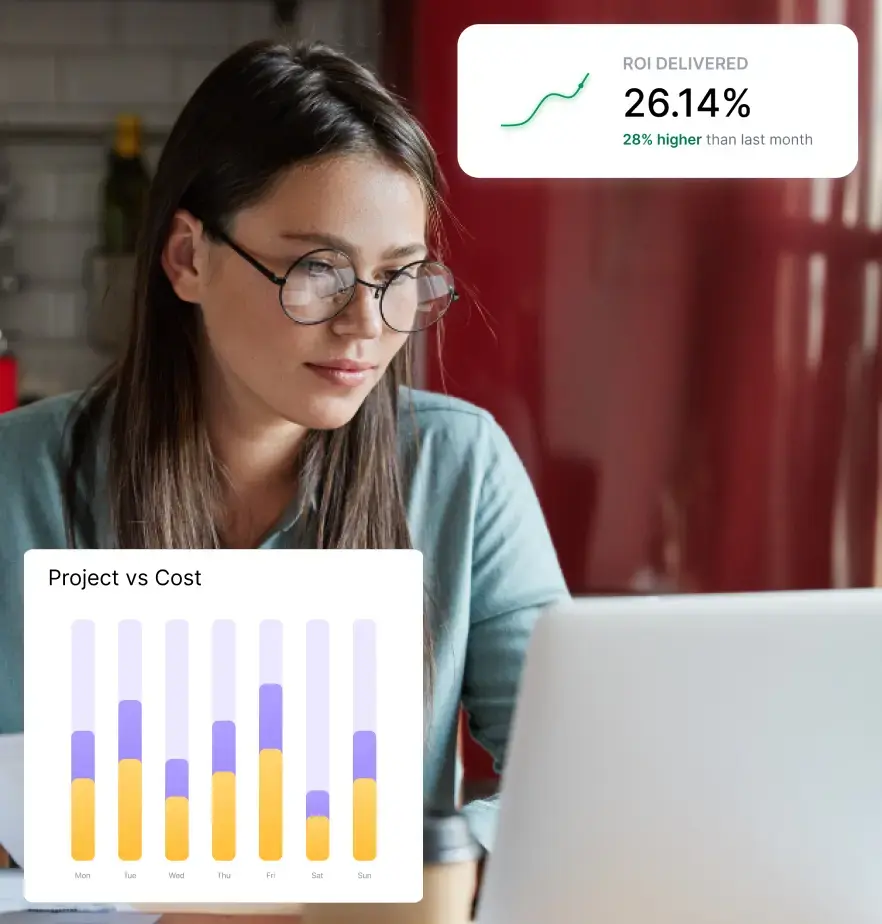
Operational Efficiency
The analytics generated by stealth monitoring software reveal inefficiencies, repetitive tasks, and underutilized resources. These insights allow managers to optimize workflows and improve productivity across departments.
Regulatory Compliance
Industries with strict compliance requirements benefit from the automated, time-stamped records generated by stealth monitoring software. This reduces the burden of manual documentation and helps avoid costly compliance violations.
Support for Hybrid and Remote Work
In a distributed workforce, maintaining oversight without constant check-ins is essential. Stealth monitoring software enables managers to track productivity and security remotely, ensuring consistent performance standards across all work environments.
By delivering these benefits discreetly, stealth monitoring software empowers organizations to work smarter, operate more securely, and make better-informed decisions—without disrupting the natural rhythm of daily tasks.
Conclusion
Running a business without clear visibility into daily operations is like trying to steer a ship through fog. You need accurate, real-world data to make the right calls—and that’s exactly what stealth monitoring software delivers.
With Flowace, that visibility comes without the drawbacks of traditional monitoring tools. It works quietly in the background, capturing genuine activity patterns so you can see how work actually gets done. The result? You get the insights you need to improve productivity, protect sensitive information, and stay compliant—without disrupting your team’s flow.
Flowace doesn’t just track; it translates raw activity data into meaningful reports you can act on. Whether you’re identifying process bottlenecks, spotting security risks, or keeping accurate client billing records, the software provides the kind of clarity that drives better decisions.
When used responsibly, Flowace’s stealth monitoring software becomes more than a productivity tool—it becomes a partner in building a secure, efficient, and accountable workplace. And for leaders who want to guide their teams with confidence, that kind of quiet power can make all the difference.