Security & Compliance
1. FLOWACE PROTECTS YOUR DATA
Thank you for choosing Flowace Technologies Private Limited (hereinafter referred as “Flowace” / “our” / “we” / “us”). We are committed to transparency and ensuring your privacy. This guide details the data accessible through our application and underscores the sensitive information that remains private. At Flowace, we prioritize the security of your data by implementing top-tier security measures and continuously improving our protocols. To do so we follow the enhanced security measures mentioned herein below.
Capitalized terms used but not defined in this document have the meaning given to them in the Terms of Service.
2. ENHANCED SECURITY MEASURES
2.1. Encrypted data transfer
All data exchanged between your device and our servers is encrypted using HTTPS, ensuring safe transmission.
2.2. Strong password management policy
We enforce strong password policies and encryption techniques to protect your login credentials.
2.3. Internal system logging
Our systems maintain comprehensive logs to monitor and respond to any suspicious activity.
2.4. Network & Infrastructure Protection
We deploy advanced security measures to protect our network and infrastructure from potential threats.
3. EXTERNAL SECURITY AUDITS AND PENETRATION TESTING
At Flowace, we are dedicated to maintaining highest level of security for our users. To achieve this, we collaborate with external security firms that conduct regular penetration testing, vulnerability assessments, patching and security audits. These proactive measures help us identify and remediate potential risks swiftly. Flowace presently partners with ‘Pentest’ to perform routine security scans along with in-depth penetration testing, ensuring our systems remain secure and resilient against evolving threats.
4. DATA BACKUP AND SYSTEM RELIABILITY
We implement daily automated backups to maintain data consistency and facilitate rapid recovery if restoration is ever required. This ensures uninterrupted service and robust data protection in the event of any system failure or data loss. Please note, restoration of data is subject to our data retention and deletion policy, available on our website.
5. SOFTWARE DEVELOPMENT SECURITY
Flowace utilizes a Git version control system for managing its code. All modifications to the code base undergo automated testing followed by manual review. Once the automated tests are passed, the changes are deployed to a staging environment. In the staging environment, Flowace employees test the changes before they are released to the production servers. Critical updates, whether for security or other urgent reasons, are expedited to production, but they still undergo thorough testing.
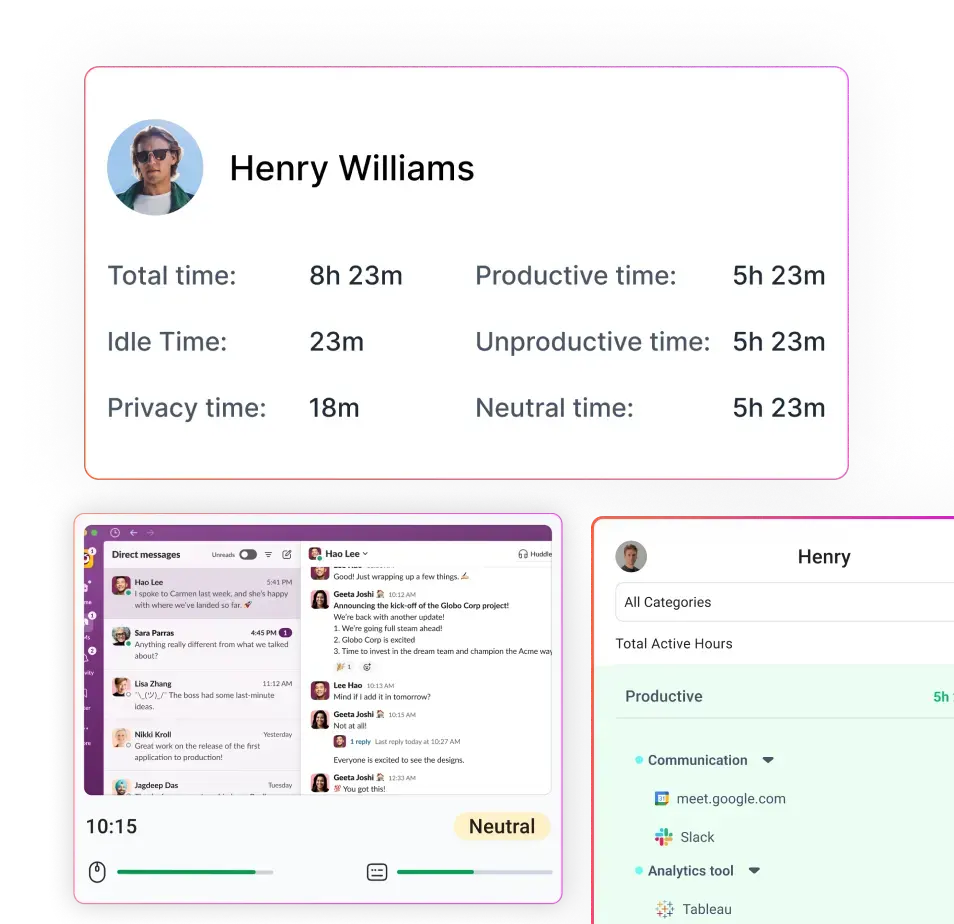
6. EMPLOYEE DATA ACCESS AND CONFIDENTIALITY
We impose strict controls on our employees’ access to the data you and your users store with Flowace. Only a small number of our employees, those who require access for troubleshooting or support, are permitted to access this data.
No employee at Flowace will access Permitter User accounts unless necessary for troubleshooting or support purposes. During support activities, we make every effort to respect your privacy by accessing only the files and settings essential to resolve your issue.
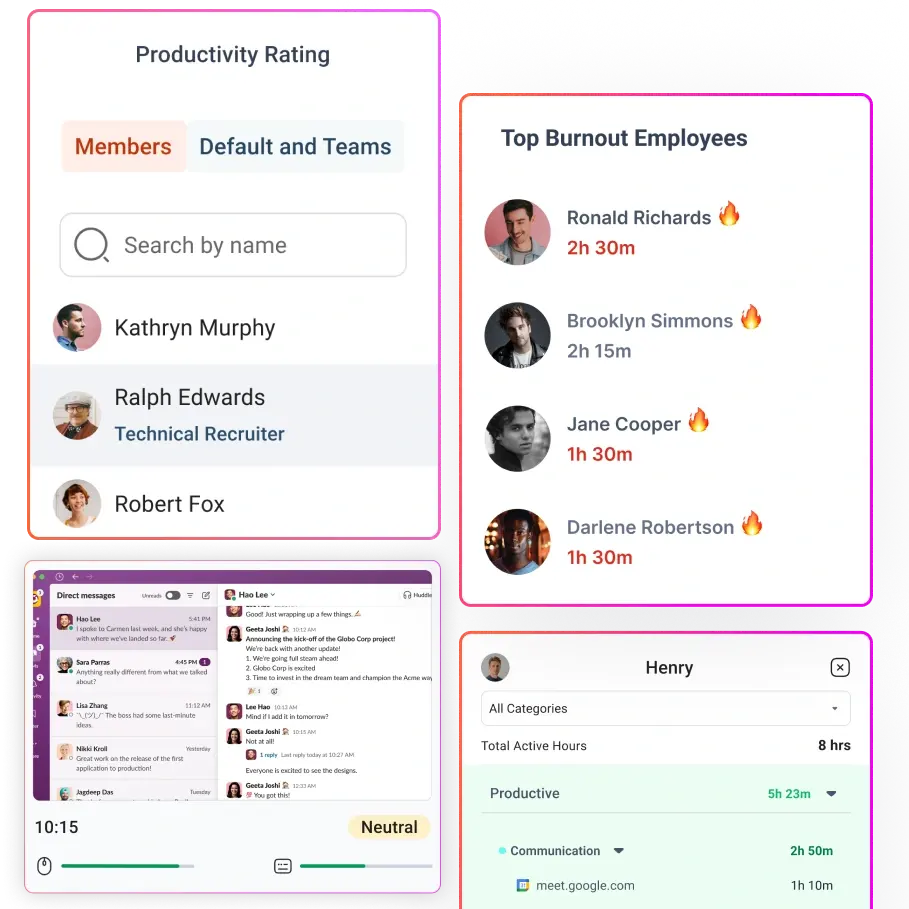
7. SCREENSHOT SECURITY
The screenshot feature in Flowace is optional. If enabled, it captures and securely stores screenshots at specified intervals. All communications are secured by SSL encryption, and our servers are located in secure data centres with 24/7 monitoring.
8. BILLING INFORMATION PROTECTION
When you register for a paid account on Flowace, we do not retain any of your credit card information.
All credit card transactions are handled through Stripe’s secure encryption, employing the same level of security used by major financial institutions. Card details are transmitted, stored, and processed in accordance with PCI-compliant standards to ensure the highest level of security.
Please go through the privacy policy of our payment gateways as well, to understand how your credit card information may be stored.
9. LICENSED SOFTWARE FEATURES, REPORTING AND SECURITY COMPLIANCE
9.1. All program enhancements to the Licensed Software shall be provided to the Licensee as part of the software as a service (SaaS) model.
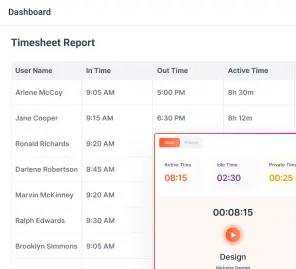
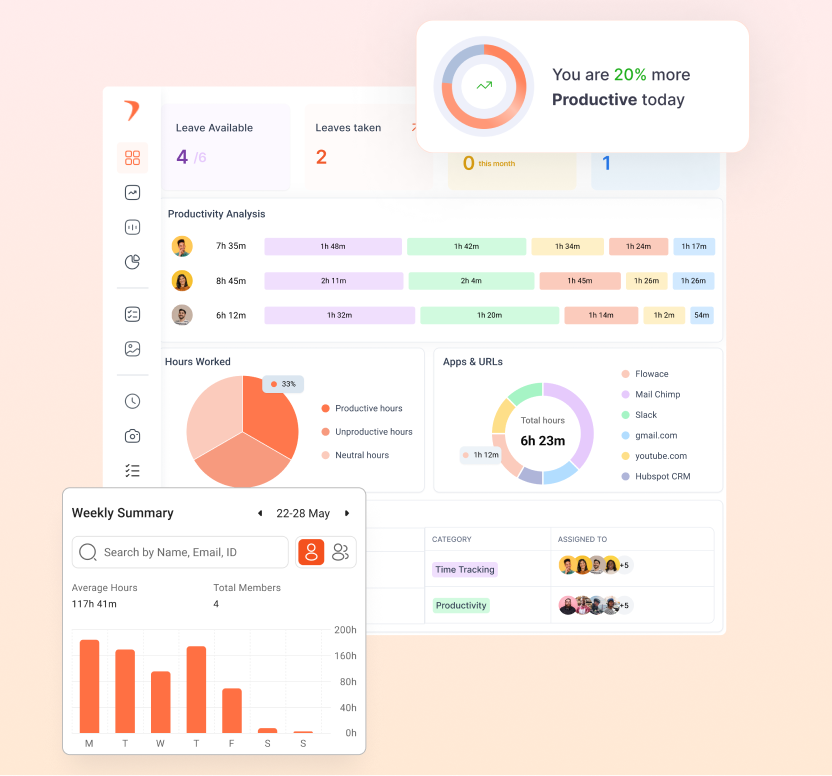
9.2. Standard reporting shall be provided on a daily and weekly basis in the Licensed Software.
9.3. All data pertaining to the Permitted Users and the Licensed Software shall be retained in the S3 bucket (AWS Cloud Storage) for a period of 1 (one) year for compliance purposes pursuant to General Data Protection Regulation (GDPR), Health Insurance and Portability and Accountability Act (HIPAA) and International Organization of Standardization (ISO).
9.4. At the time of deletion of a user account, the data pertaining to such deleted user shall be retained/deleted as per our data retention and deletion protocol, available on our website.
10. YOUR PRIVACY MATTERS
Your privacy is paramount to us. We are transparent about the data we collect and ensure your personal information is treated with care and respect.