-
Employee monitoring software is legal in the U.S., but legality depends on notice, consent, device ownership, scope, and how collected data is used.
-
Employers have the strongest legal footing when monitoring activity on employer-owned devices and company networks for legitimate business purposes.
-
Remote and hybrid work increases legal risk when monitoring becomes continuous, overly invasive, or spills into personal use, especially on BYOD setups.
-
Screenshots, keystroke logging, audio recording, and biometric monitoring are high-risk practices that require strict justification, safeguards, and often explicit consent.
-
Federal laws like the ECPA, wiretap rules, labor law, and anti-discrimination law set the baseline, but state laws can impose much stricter requirements.
-
Productivity monitoring should be proportionate and clearly separated from security monitoring, with different access controls and retention rules.
-
Monitoring data should never be the sole basis for discipline and must be reviewed with context, human oversight, and a clear appeals process.
-
Transparent, employee-facing monitoring policies are essential to reduce legal exposure and maintain trust.
-
BYOD and biometric monitoring demand heightened care, clear consent, and narrowly scoped technical controls.
-
The safest approach is insight-driven monitoring that prioritizes aggregated analytics over raw surveillance, which is where tools like Flowace are designed to fit.
Key Takeaways:
A recent college graduate in the U.S. revealed on TikTok that his employer installed monitoring software on his work laptop that takes a screenshot every 10 minutes, tracks keystrokes, mouse activity, and the websites visited during work hours. The employee described the experience as “pretty dystopian,” even though he understands why companies use such tools. His video has garnered significant attention on social media, sparking debate about remote work monitoring, employee privacy, and how productivity should be measured.
This left a lot of people wondering: Is employee monitoring software even legal in the USA?
The short answer is yes. But it is not as simple as that.
The difference between lawful productivity tracking and illegal surveillance often comes down to nuances like consent, device ownership, notice, and how data is used.
This guide explains what the law actually allows, where companies get into trouble, and how to monitor work without damaging trust or triggering legal exposure.
Is Employee Monitoring Software Legal in the USA?
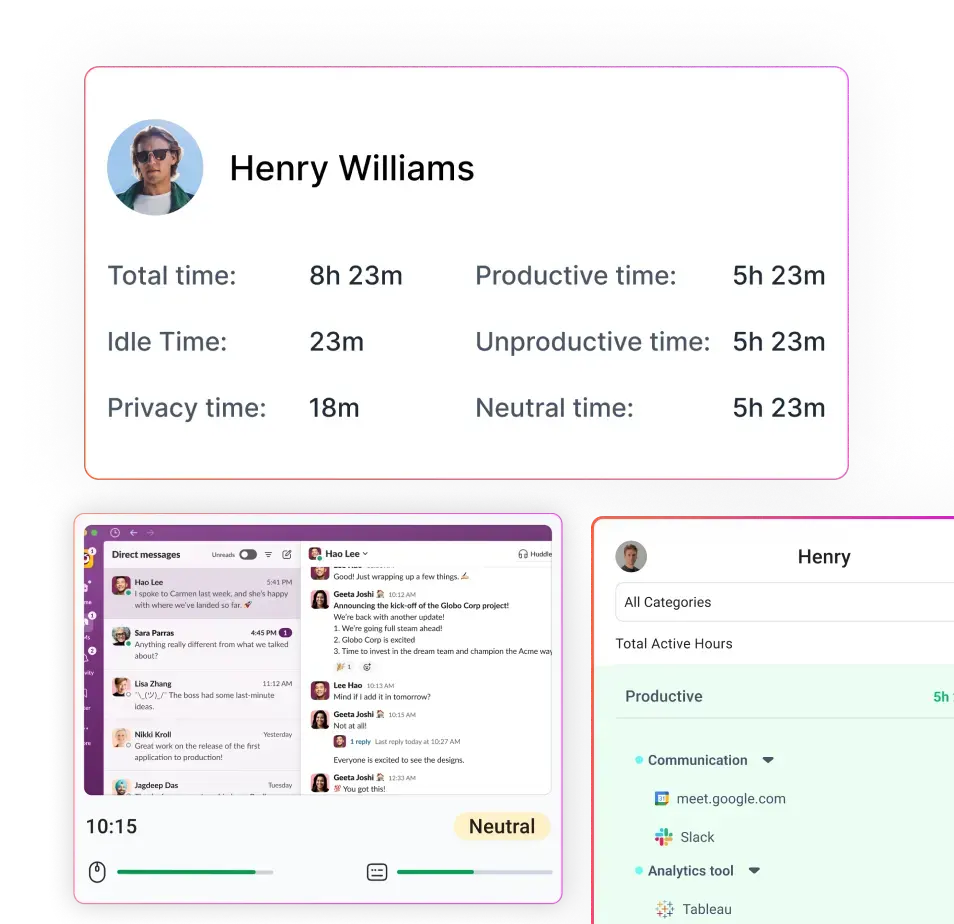
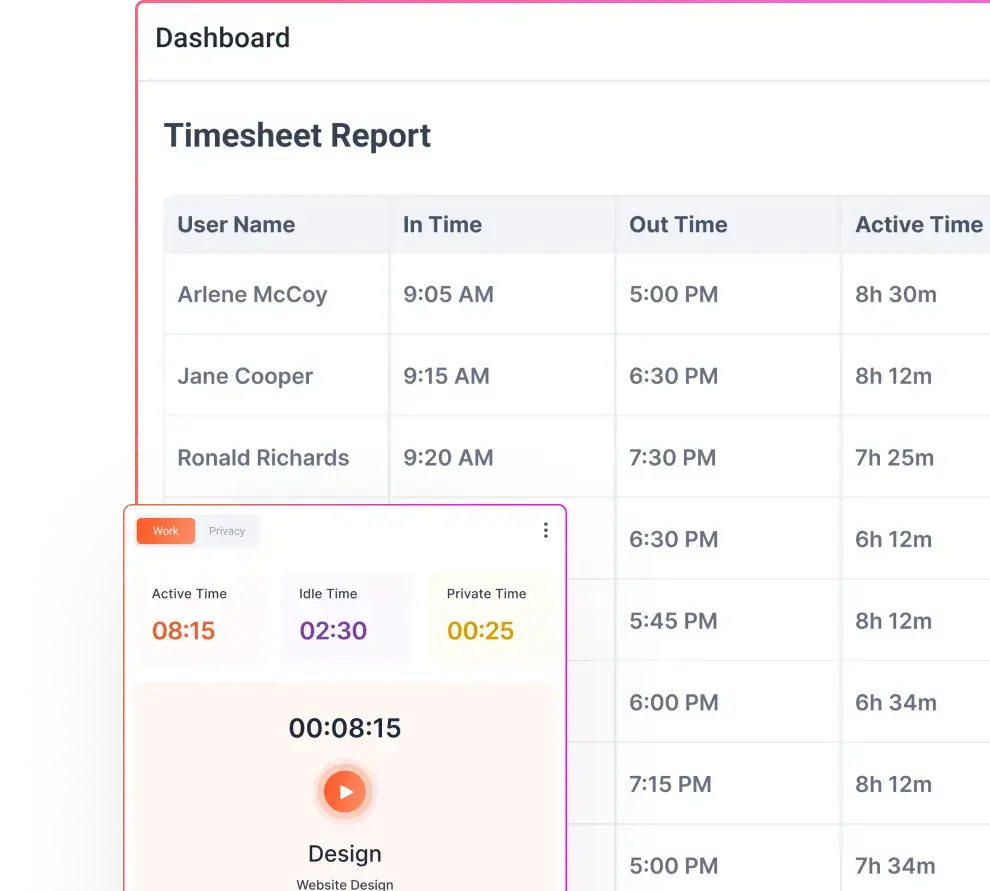
Employee monitoring is the practice of collecting data about employees’ behavior, communications, location, or device activity while they perform work. Employee monitoring tools range from simple time-tracking apps and VPN/logging records to advanced software that takes periodic screenshots, logs keystrokes, records websites visited, tracks app usage, collects GPS or wearable health data, or processes video and biometric identifiers.
The goal can be productivity measurement, security (detecting data exfiltration), compliance, or attendance tracking with a single productivity tool. But the data collected can also raise serious privacy, labor-law, and discrimination risks.
In many circumstances, employers may legally monitor employees, especially on employer-owned devices and company networks. This has become particularly relevant in remote and hybrid work environments, where work no longer happens inside a controlled office setting.
However, the legal tolerance for monitoring in remote and hybrid contexts still depends on scope and proportionality. Continuous surveillance, invasive techniques like constant screenshots or keystroke logging without clear justification, or monitoring that spills into personal use (especially on BYOD setups) increases legal risk.
As a result, employers cannot rely on technology alone to justify monitoring. They must also comply with applicable employee monitoring laws and regulations, which govern what data can be collected, how it may be used, and when employee notice or consent is required. Honoring these legal boundaries is essential not only to reduce regulatory and litigation risk, but also to maintain employee trust in increasingly flexible work environments.
Federal Laws Governing Employee Monitoring
Employee monitoring in the United States is governed by several federal and state laws. These employee monitoring laws set the baseline for what employers may do when they track communications, devices, or activity.
In the USA,
- Federal law (ECPA) allows monitoring on employer-owned devices for legitimate business purposes, especially with notice. It is breached by secret interception, particularly audio recording or monitoring personal devices without consent.
- Wiretap rules make audio recording the highest-risk activity. Recording conversations without proper consent is often illegal.
- Stored Communications rules allow access to work emails and data stored on company systems, but accessing third-party or personal accounts without authorization is a breach.
- State laws can be stricter than federal law. States like California require proportional, disclosed monitoring, while Illinois (BIPA) strictly regulates biometric attendance data. Violations can trigger heavy penalties.
- Labor law (NLRB) allows reasonable monitoring, but surveillance that discourages wage discussions, organizing, or other protected collective activity is unlawful.
- Anti-discrimination law (EEOC/ADA) allows productivity tracking but treats monitoring that reveals health, disability, or biometric data as high risk.
You can see a detailed breakdown of each federal and state law, what they allow, and where employers cross the line in our complete guide to Employee Monitoring Laws.
What Employers Can Legally Monitor
A practical, low-risk approach is to collect only the data you need to meet a legitimate business purpose and to design monitoring so it minimizes employee privacy intrusion. That means following best practices for employee monitoring.
Monitoring On Employer-owned Devices
You generally have the clearest legal footing to monitor activity on devices and accounts you own because courts and statutes recognize employer control over employer systems. But that doesn’t create a free pass.
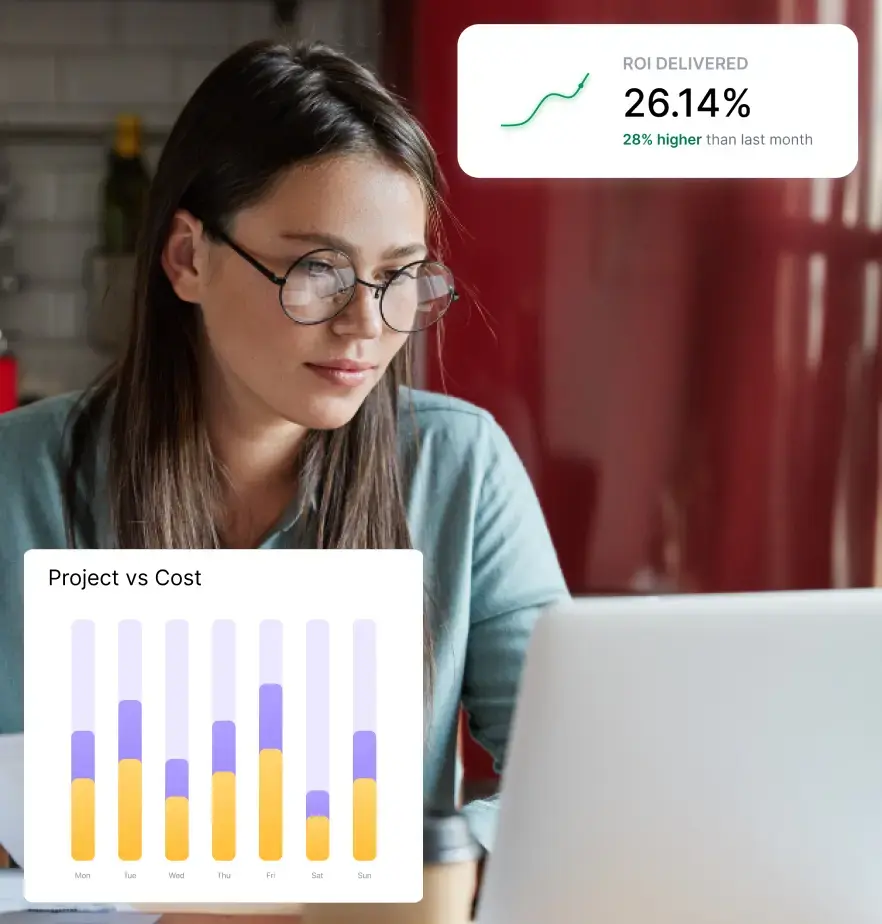
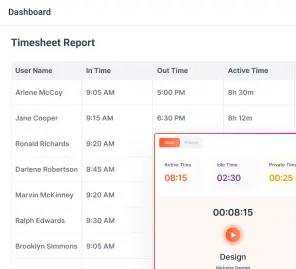
Modern workforce analytics platforms are increasingly built around these principles: measuring how work time is distributed rather than recording everything an employee does.
Low-risk implementation looks like this:
- Publish an acceptable-use and monitoring policy that is easy to find and written in plain language.
- Put employees on notice before enrollment (email + signed acknowledgement for higher-risk monitoring).
- Limit monitoring to defined business purposes (security, time tracking compliance) and document those purposes.
- Use technical separation where possible (work profiles, MDM containers, separate user accounts), so personal activity is segregated.
- Encrypt collected data, log access, and restrict who can view raw records.
Systems that focus on work profiles, application-level analytics, and project-based time data align more closely with how employer access rights are interpreted under U.S. and international law.
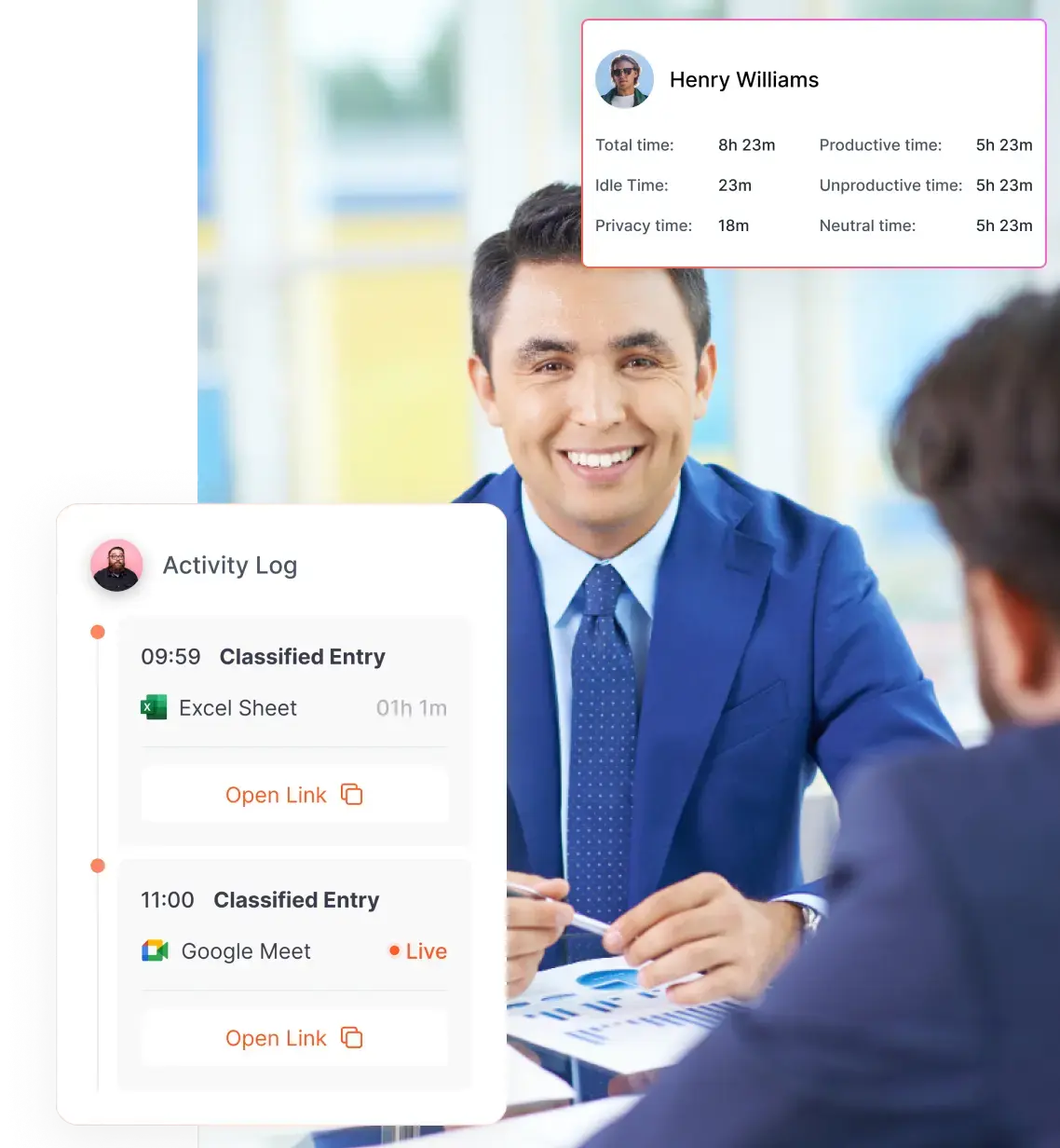
Screenshots, Keystroke Logging, And Activity Tracking
Screenshots and keystroke logging are among the riskiest forms of monitoring because they capture rich, often sensitive content. If your business genuinely requires them, apply layered safeguards:
- Question the necessity. Ask whether summaries (app usage, time on task, window titles) would meet the business need before resorting to screenshots or keystroke logs.
- Limit frequency and scope. Reduce screenshot cadence (e.g., once per hour), restrict screenshots to work applications, and avoid capturing known sensitive windows (banking, health portals, password managers).
- Implement automatic redaction/filters. Use tools or rules that detect and blur password fields, PII patterns, or certain domain names before storing images.
- Human review rules. Only escalate flagged items for human review and record who reviewed them and why. Prefer automated alerts that point to metadata rather than exposing full screenshots to reviewers by default.
- Retention & purge. Keep raw captures for the shortest necessary period (e.g., 7–30 days) and then delete or permanently redact them.
- Notice & consent. Give clear notice and, when required by state law or contract, obtain written consent.
Email, Chat, And Internet Usage Monitoring
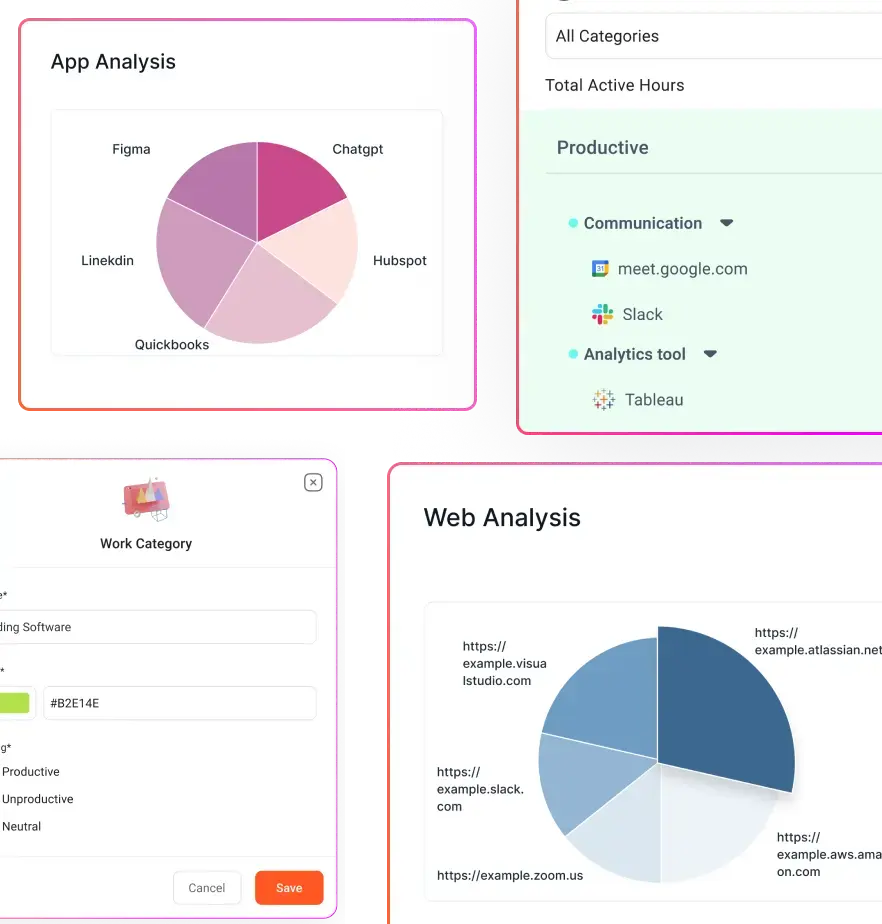
Monitoring email, chat, and web use on corporate systems is commonly lawful for security, compliance, and productivity reasons. As generative AI tools become part of everyday work, employee monitoring extends to AI usage and whether sensitive or proprietary data is shared through them.
You can reduce risk and employee pushback by adopting these practices:
- Prefer metadata first. Track sender/recipient, timestamps, attachment size, and domain access rather than full message content unless necessary.
- Use DLP (Data Loss Prevention) rules for specific risks. Instead of blanket content review, configure DLP to trigger on defined patterns (SSNs, credit card numbers, export of large file sets). Only pull message content when DLP rules are triggered.
- Automated alerts + staged review. Let automated systems generate alerts; require at least one human-in-the-loop decision before taking adverse action.
- Avoid personal communications deep inspection. If personal email/chat is allowed on corporate devices, avoid routine content review of clearly personal messages. If you must search content (e.g., for legal discovery), follow a documented legal hold and counsel review process.
- Record retention & legal holds. Define retention schedules and override them only with documented legal holds. Delete extraneous content per policy.
These approaches reduce privacy intrusion while preserving the employer’s ability to detect data exfiltration and enforce policies.
Special Considerations For Byod And Remote/Hybrid Work
BYOD and hybrid setups raise additional risks because personal privacy expectations are higher when employees use their own devices or work from home.
Best practices:
- Offer a work container / corporate profile. Require that monitoring be limited to a company-controlled container rather than the whole device.
- Make monitoring optional or provide an alternative. For employees unwilling to enroll personal devices, offer a company device or other alternatives.
- Separate policies by location. Map rules to employee physical location — a monitoring practice lawful in one state may be unlawful in another.
- Limit location tracking. If GPS is needed for safety or logistics, restrict it to work hours and allow opt-out where possible for nonessential roles.
When BYOD is unavoidable, obtain clear consent and explain exactly what the employer can and cannot access.
Security Monitoring Vs. Productivity Monitoring
Security monitoring (endpoint detection, SIEM, anti-malware, DLP) is often essential to protect company assets and customers. Productivity monitoring is more intrusive and should be justified by clear operational needs.
- Segregate teams and access. Security teams may need raw telemetry; HR should not have unfettered access to the same raw feeds. Build role-based access and separation-of-duties controls.
- Use different retention/visibility rules. Security telemetry can be retained longer for incident investigation; productivity captures should be more tightly scoped and shorter lived.
- Document business justification. Keep a record explaining why any particularly invasive capability (keystroke logs, screenshots) is required and what less invasive options were considered.
Human Review, Discipline, And Fairness
- Don’t use monitoring as the only basis for discipline. Corroborate monitoring signals with work output, manager notes, and context.
- Build an appeals process. Allow employees to contest adverse actions and explain anomalies.
- Train managers. Managers should understand the limits of monitoring data and how to use it responsibly.
- Audit access. Log who accessed monitoring data and why; review access logs periodically to prevent misuse.
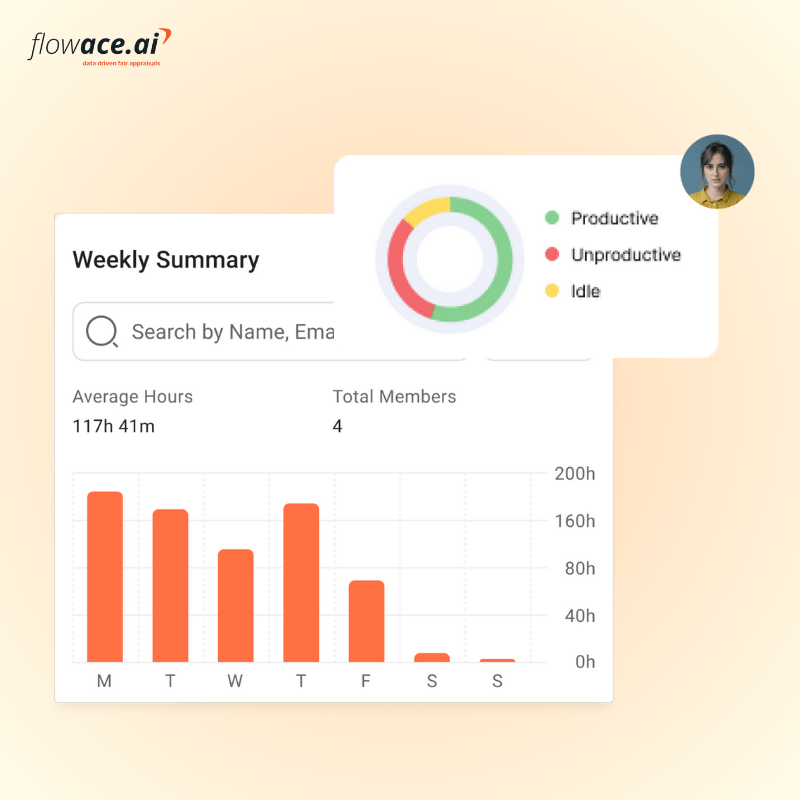
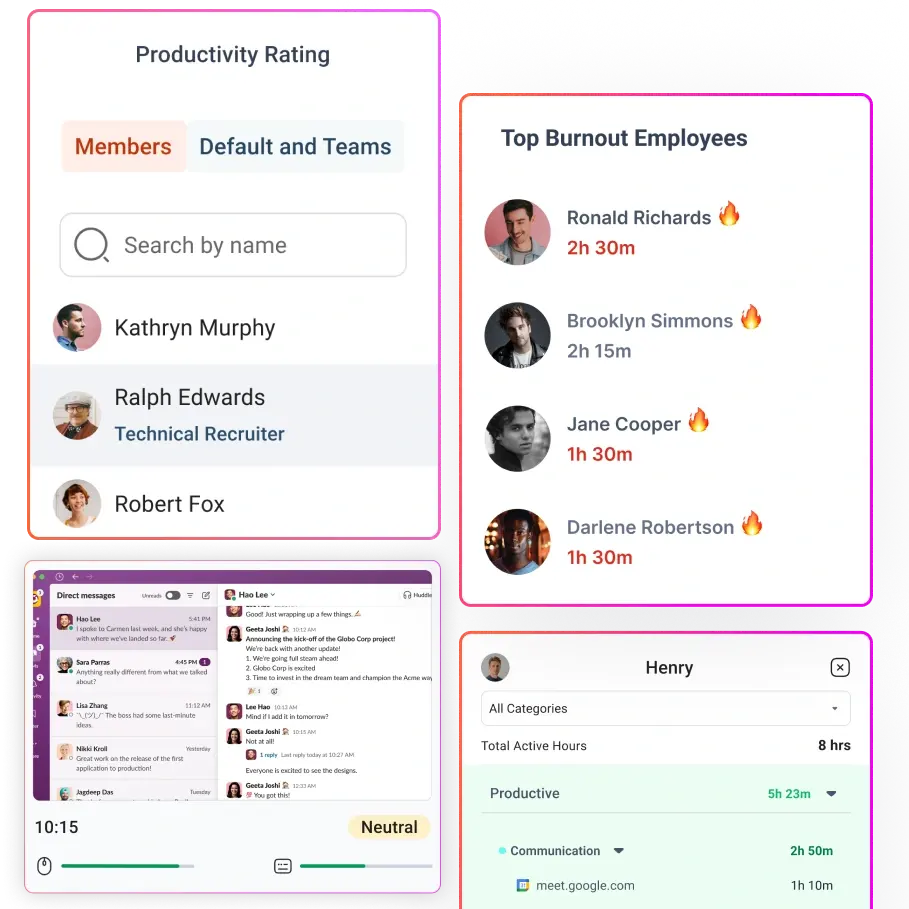
These steps reduce wrongful discipline claims and lessen discrimination risk. Flowace is designed to fit within this low-risk, defensible framework by emphasizing work analytics over surveillance. Flowace aligns with the above principles by:
- Prioritizing time distribution, application usage patterns, and productivity summaries over constant content capture.
- Allowing employers to configure periodic, scoped screenshots rather than continuous monitoring.
- Supporting role-based access, so raw activity data is not broadly visible.
- Enabling short retention windows and automatic data cleanup.
- Distinguishing productivity analytics from security tooling.
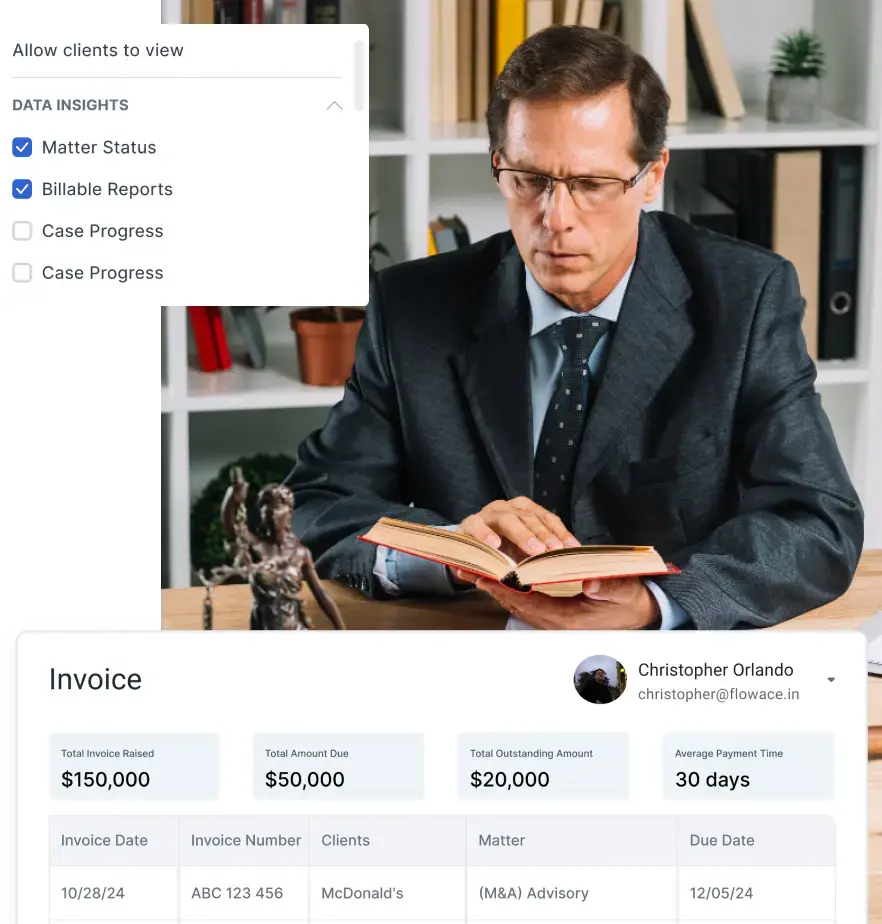
- Supporting transparency through dashboards and documented policies.
- Allowing organizations to scale monitoring intensity based on business need and jurisdiction.
When deployed with clear notice, limited scope, and human oversight, Flowace fits squarely within modern legal expectations.
High-Risk and Often Illegal Monitoring Practices
Some employee monitoring practices sit squarely in high-risk territory and, depending on how and where they’re used, can be outright illegal. These are the areas where employers most often cross the line, especially in remote and hybrid work setups.
Audio and Video Recording Without Consent
Recording employees through microphones or webcams without clear, informed consent is one of the fastest ways to invite legal trouble. In many U.S. states, audio recording is governed by wiretapping laws that require consent from one or all parties. Even video monitoring, while sometimes allowed in limited workplace contexts, becomes problematic when it captures private spaces, off-hours activity, or personal conversations.
Monitoring Personal Devices and BYOD Risks
When employees use their own laptops or phones for work, your legal footing weakens significantly. Monitoring that spills into personal devices can easily capture private communications, personal browsing, or non-work activity, raising privacy and labor-law concerns. Even with BYOD policies in place, courts and regulators expect you to narrowly limit monitoring to work-related applications or containers, clearly disclose what is collected, and avoid blanket device-level surveillance.
Biometric and Facial Recognition Monitoring
Biometric data, such as facial scans, fingerprints, voiceprints, or behavioral identifiers, is treated as highly sensitive under U.S. law. States like Illinois, Texas, and Washington impose strict rules on how biometric data can be collected, stored, and used, often requiring explicit written consent and clear data retention limits. Facial recognition for attendance, identity verification, or productivity tracking may seem efficient, but it carries disproportionate legal and ethical risk, especially if alternatives exist.
Employee Monitoring Policy Framework
If you’re going to monitor employee activity, you need more than a tool. You need an ethical employee monitoring policy that clearly explains why monitoring exists, what is being monitored, and where the boundaries are. This framework is designed to help you implement employee monitoring in a way that is transparent, proportionate, and defensible.
Scope And Purpose Of Monitoring
You’ll want to open with a short, plain-language statement that says what you monitor and why. Keep it concrete and business-focused so employees immediately understand the justification.
Suggested structure:
- Purpose: Explain the legitimate business reasons (security, protecting customer data, regulatory compliance, timekeeping, fraud prevention, maintaining service levels).
- Scope: State who is covered (employees, contractors), which devices/accounts (company-owned laptops, corporate apps, work profiles on BYOD), and when monitoring applies (work hours, remote work sessions, company networks).
- Limitations: Call out what you will not do (no monitoring in restrooms/locker rooms; no routine inspection of personal accounts; no secret audio recording without consent).
- Jurisdictional note: Tell employees you’ll follow the law where they’re physically located and that local rules may shape what you collect.
Types Of Monitoring Disclosed (Be Specific And Transparent)
List the concrete technical capabilities so there’s no ambiguity. For each type of employee monitoring, add a one-line rationale and the retention period you intend to use.
Example list:
- Application and website usage (metadata only): Which apps and domains are used and time spent — used for performance analytics; retain 90–180 days.
- Email and chat metadata / DLP triggers: Sender, recipient, timestamps, and content access only when DLP rules fire — used to prevent data leaks; retain per legal hold or 180 days.
- Screenshots (restricted): Periodic screenshots limited to work apps, redacted automatically — used only for specific investigations or fraud detection; retain 7–30 days before purge.
- Keystroke logging (rare, controlled): Only with documented justification and consent; apply filters to exclude PII — minimized and retained no longer than necessary.
- Endpoint security telemetry: Antivirus, patch status, process lists — used for security operations; retain 1–2 years for forensic needs.
- Location tracking (role-based): GPS only for roles requiring it (drivers) and restricted to work hours — retain 30–90 days.
For each capability you list, include: business purpose, who can access the data, retention period, and escalation rules.
Employee Rights And Acknowledgement
Make this section clear and practical for employees by explaining what information may be monitored, when and why it happens, and what is explicitly out of scope.
Core elements to include:
- Notice: You will tell employees about monitoring before it begins (email + policy + intranet).
- Consent & opt-ins: Where law requires or the monitoring is high risk (biometrics, BYOD), you’ll obtain written or electronic consent.
- Access & correction: Employees can request a copy of monitoring data about them and ask for corrections or context notes.
- Usage limits: Data won’t be used for unrelated purposes (e.g., marketing) without new notice.
- Appeal process: Define how to contest discipline or data inaccuracies (manager → HR review → escalation to privacy officer).
- Privacy contact: Give a named contact (privacy officer or HR) and a link to the full policy.
Pre-Implementation Legal Review (What You Must Check Before Rollout)
You need a documented legal sign-off before you flip the switch on anything intrusive.
Legal review checklist:
- Applicable laws: Map state and local wiretapping, biometric, and data protection laws by employee location.
- Union/bargaining considerations: Check collective bargaining agreements or notice obligations.
- Contractual constraints: Review customer contracts and vendor terms for data transfer limits.
- Data transfers: Identify cross-border transfers and apply appropriate safeguards.
- Regulated data: Confirm whether monitoring could capture regulated categories (health, financial) and plan exclusions
- Documentation: Save written legal opinions or memos describing why monitoring is lawful and proportionate.
Conclusion
So, is employee monitoring software legal in the USA? Yes.
But, only when it is implemented thoughtfully, within clearly defined legal boundaries. As this guide shows, the difference between lawful employee monitoring and illegal surveillance is rarely about the tool itself. It comes down to how monitoring is designed, disclosed, limited, and governed.
Employers have broad rights to monitor activity on company-owned devices and systems, especially for security, compliance, and operational needs. However, those rights shrink quickly when monitoring becomes excessive, covert, or disconnected from a legitimate business purpose.
The safest path forward is not more surveillance, but smarter monitoring. That means prioritizing aggregated insights over raw content, and separating security monitoring from productivity analytics
This is exactly where platforms like Flowace fit in. Flowace is designed to support modern, remote-first teams by focusing on work analytics rather than invasive surveillance. By emphasizing time distribution, application usage patterns, and productivity summaries, Flowace helps organizations stay aligned with U.S. employee monitoring laws while still gaining the visibility they need to manage employee performance.
If you’re evaluating employee monitoring software and want to avoid legal pitfalls while still improving productivity and accountability, Flowace offers a practical, low-risk approach.
Start a free trial of Flowace to see how compliant, insight-driven monitoring works in practice. Or book a free demo to explore how Flowace can be configured for your team, location, and legal requirements.
FAQs:
Can Employers Track Screens Remotely in the U.S.?
Yes, employers can remotely track screens on employer-owned devices for legitimate business purposes, but they must provide notice and avoid excessive or continuous surveillance without justification.
Is Employee Consent Always Required?
Not always, but consent is often required for higher-risk monitoring such as audio recording, biometric data collection, or monitoring personal devices under BYOD arrangements.
Can Monitoring Be Used for Discipline or Termination?
Monitoring data can be used as part of disciplinary decisions, but it should not be the sole basis and must be corroborated with context, performance records, and fair review processes.
What Are the Penalties for Illegal Monitoring?
Penalties can include civil lawsuits, statutory damages, regulatory fines, injunctions, and, in some cases, criminal liability depending on the law violated.