How do you prove compliance and safeguard company assets without crossing into surveillance that damages trust? Regulators like the EU’s GDPR and California’s CCPA make the line razor-thin, and the stakes couldn’t be higher: multi-million-dollar fines, costly lawsuits, and the harder-to-repair loss of employee confidence.
This guide will walk you through how to navigate that balance, covering global compliance rules, data protection strategies, and best practices to implement employee monitoring that’s both legally sound and people-first.
Key Takeaways
|
GDPR Requirements for Employee Monitoring
If you’re an employer in 2025, you can’t even think about employee monitoring without bumping into GDPR. It’s the privacy rulebook that everyone looks to, whether you’re based in the EU or not. And while GDPR doesn’t ban monitoring, it does make one thing crystal clear: you need a solid, lawful reason to collect employee data.
That “reason” comes from GDPR’s legal bases for data processing. Out of the six options, only three realistically apply to monitoring. Let’s break them down in plain English.
Legal Basis Requirements for Monitoring

1. Contractual Necessity (Article 6(1)(b))
Sometimes, monitoring is baked right into the job itself. Think about a delivery driver—the company needs GPS tracking to make sure packages arrive where they should. That kind of tracking is tied directly to the employment contract, so it passes GDPR’s test. But here’s the catch: you can’t stretch this rule to cover things like keystroke logging or random screenshot capturing. Unless it’s absolutely essential for the job, this basis doesn’t hold up.
2. Legal Obligation (Article 6(1)(c))
In some industries, the law requires monitoring. For example, banks and trading firms must record certain communications to meet anti-fraud and insider trading rules. In this case, GDPR says: “Fair enough, you’re following the law.” If you’re in a heavily regulated sector, this is often your strongest justification.
3. Legitimate Interests (Article 6(1)(f))
This is the big one, and the one most companies lean on. It basically means: we have a good reason to monitor, and it outweighs the impact on employee privacy.
- Installing CCTV in the office lobby to prevent theft? Reasonable.
- Tracking work emails to prevent phishing attacks? Also reasonable.
- Running hidden software to record every keystroke? Not reasonable.
The golden rule here is balance. Your need to protect the business has to be weighed carefully against your employees’ right to privacy. And if the scale tips too far in your favor, GDPR won’t back you up.
Why Consent Doesn’t Work in the Workplace
At first glance, consent seems like the easiest path. Just ask employees to sign off, right? Wrong. Under GDPR, consent has to be freely given. And let’s be real, when your boss asks for consent, how “free” does that feel? Most employees won’t say no, even if they’re uncomfortable, because the power dynamic makes refusal nearly impossible.
That’s why European regulators rarely accept consent as a valid legal basis for workplace monitoring. It’s just too messy. Instead, you need to ground your monitoring in contractual necessity, legal obligation, or legitimate interest, and be ready to show your reasoning if regulators come knocking.
Core GDPR Data Protection Principles
Even if you’ve nailed down your legal basis for monitoring, that’s only step one. GDPR doesn’t stop there; it expects you to play fair with employee data at every stage. That’s where its core principles come in.
Think of these as the “rules of the road” for monitoring. If you ignore them, it doesn’t matter what justification you claim; your practices can still land you in hot water.
Let’s break them down in plain language.
1. Lawfulness, Fairness, and Transparency
Monitoring has to be lawful (tied to one of the legal bases we just covered), but also fair and transparent. This means no hidden software running in the background, no vague clauses buried deep in a contract. Employees should clearly know:
- What is being monitored
- Why it is being monitored
- How the data will be used
Transparency builds trust. A company that explains “We use activity monitoring to prevent data breaches” will always fare better than one that quietly logs every click.
2. Purpose Limitation
Under GDPR, you can’t collect data “just in case” you might need it later. Every monitoring activity has to be tied to a specific, legitimate purpose. For example:
- Recording calls in a call center for quality assurance = valid purpose.
- Recording calls and then using that same data to evaluate personal behavior unrelated to work = overstepping.
- Purpose creep—using data for something you never told employees about—is one of the fastest ways to fall foul of GDPR.
3. Data Minimization
Collect only what you need, and nothing more. If monitoring internet use, for instance, you may only need to know time spent on work-related vs. non-work-related sites, not the exact pages someone browsed on their lunch break. GDPR is clear: the less personal data you collect, the safer you are.
4. Accuracy and Relevance of Monitoring Data
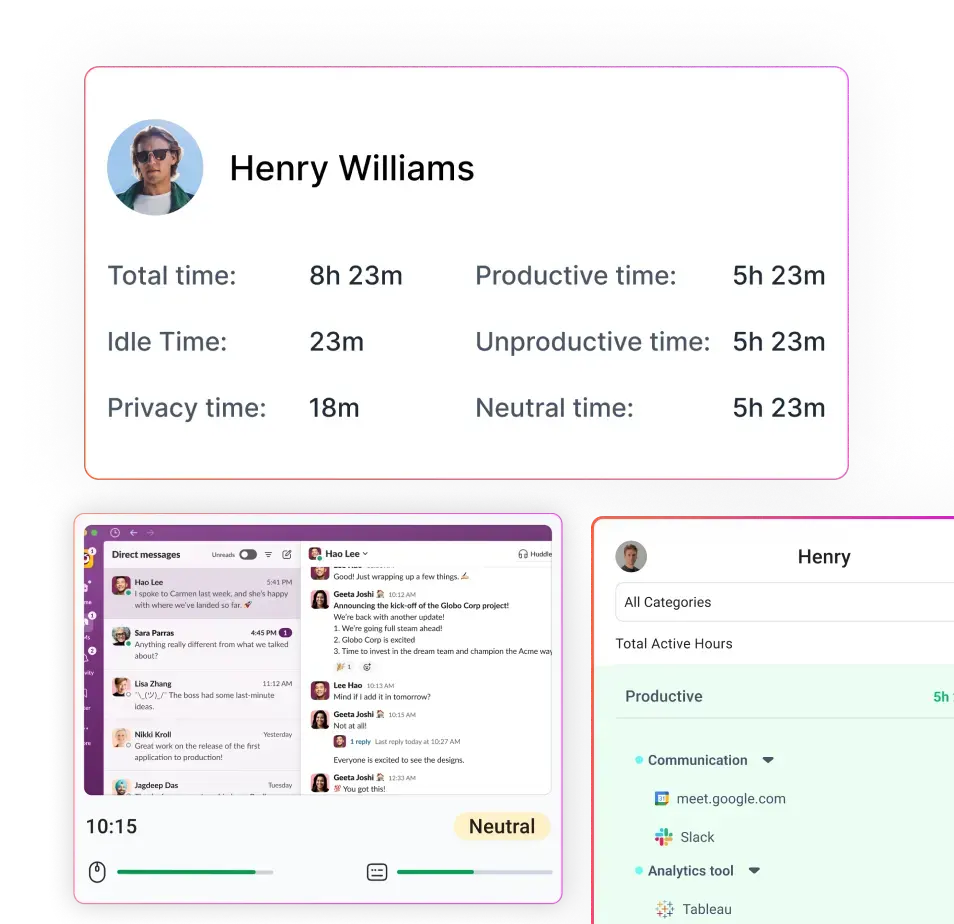
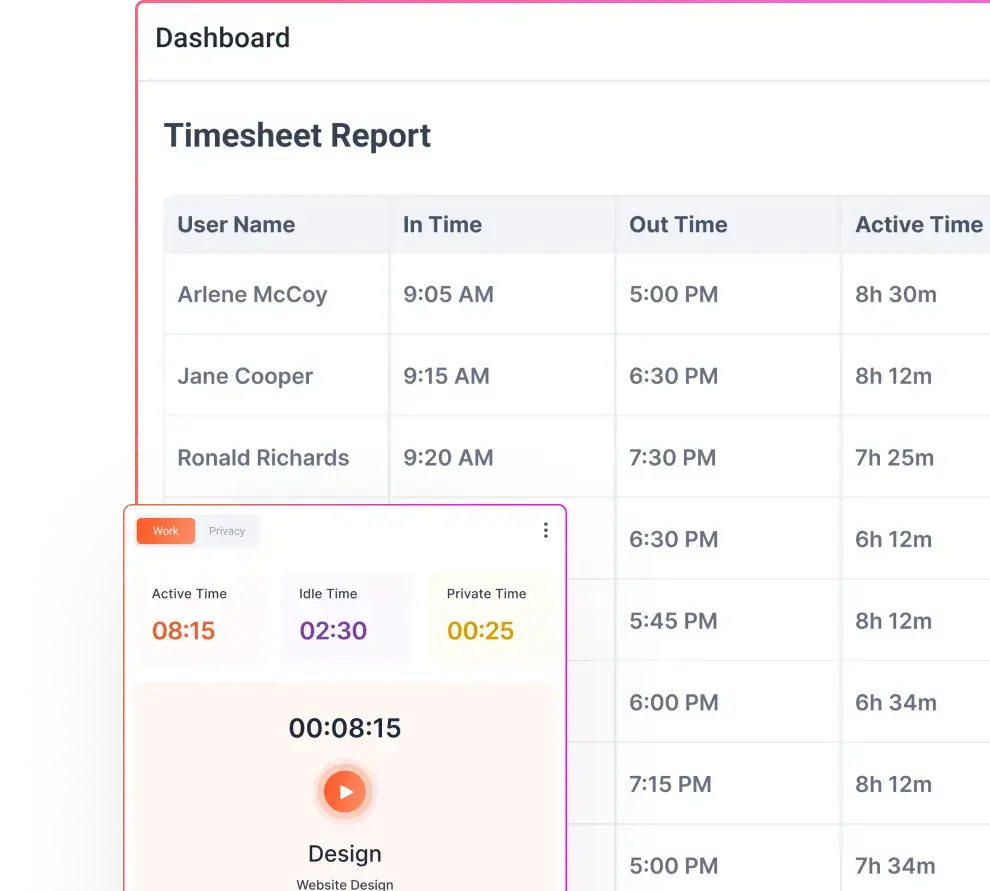
If you’re going to monitor, the data you collect has to be accurate and relevant. Imagine disciplining an employee based on flawed time-tracking software that recorded idle time when they were actually on a client call; that’s not just unfair, it’s potentially unlawful. Employers must ensure that monitoring tools are reliable and that the data reflects the reality of work.
5. Storage Limitation and Retention Periods
Data shouldn’t live forever on your servers. GDPR requires that monitoring records be kept only for as long as they serve the stated purpose. For example, call recordings for training might only be kept for six months, not indefinitely. Setting and sticking to clear retention policies is critical, not only for compliance but also for showing employees their data isn’t being hoarded.
6. Integrity, Confidentiality, and Security
Collecting data means you’re responsible for protecting it. That includes technical safeguards (like encryption and access controls) and organizational measures (like restricting who can view the data). A leak of sensitive employee monitoring data, say, screenshots, location logs, or keystrokes, can be devastating, both legally and reputationally. GDPR makes it your duty to ensure data stays safe, private, and confidential.
Employee Rights Under GDPR
- Right to be informed: Employees must be clearly told what monitoring happens, why, and how their data is used.
- Right of access: Employees can request to see the monitoring records collected about them.
- Right to rectification: Employees can demand correction of inaccurate or misleading monitoring data.
- Right to erasure: Employees may request deletion of monitoring data that is excessive or no longer needed.
- Right to data portability: Employees can obtain their personal data in a structured, machine-readable format.
- Right to object: Employees may object to monitoring if it outweighs their privacy rights.
- Automated decisions: Employees have the right to challenge and seek human review of decisions made solely by monitoring algorithms.
Global Data Protection Laws for Employee Monitoring

United States
California (CCPA / CPRA)
California gives employees/consumers rights to access, correct, delete, and restrict certain uses of personal data; the CPRA (expanded in 2023) strengthens protections for “sensitive” employee data and adds obligations for businesses.
Biometric rules (BIPA – Illinois)
Illinois’ BIPA tightly restricts biometric collection (fingerprints, face, retina) and generally requires informed written consent and clear policies; recent legislative tweaks have altered liability, but BIPA remains a major constraint on biometric monitoring.
State-level notice laws
Several states (e.g., NY, CT, DE) require employers to provide explicit notice of electronic monitoring (sometimes on hire and/or daily reminders), so U.S. compliance often means tailored state-level disclosures.
Canada
PIPEDA & provincial regimes
Canada’s federal privacy framework (and some provincial laws) requires that employee monitoring be reasonable, necessary, and proportionate; employers should document purpose, limit collection, and enable access/rectification. Guidance emphasizes transparency and a reasonableness standard for workplace monitoring.
Australia
Privacy Act 1988 + state laws: The federal Privacy Act doesn’t explicitly ban monitoring, but employers must follow the Act plus state/territory workplace surveillance rules; states such as NSW have specific Workplace Surveillance Acts requiring notices and limits on covert surveillance. National discussions about closing employee-record exemptions continue.
United Kingdom
UK GDPR & Data Protection Act 2018
Post-Brexit UK retains GDPR-style protections; monitoring must meet data-protection principles (lawful basis, fairness, minimization) and be defensible under legitimate interests or other bases. The ICO’s Employment Practices Code and worker-monitoring guidance are essential reading for employers.
Other Jurisdictions & Cross-border Notes
EU member-state nuances: Member states add local rules and stronger worker protections in areas like strict works-council consultation, sectoral limits, or pending national employee-data acts (e.g., Germany’s draft Employee Data Act). Employers must map both EU GDPR and local laws.
Cross-border monitoring implications
Global employers must consider data-transfer rules, differing legal bases, and local consent/notice requirements; a one-size-fits-all monitoring policy often fails. Implement country-specific controls, DPIAs, and contractual/data-transfer safeguards.
Data Protection Impact Assessment (DPIA)
A Data Protection Impact Assessment (DPIA) is like a risk radar for employee monitoring. It forces employers to slow down and ask: Is this monitoring truly necessary? What risks does it create for our people? How do we protect them?
When a DPIA Is Required
You’ll almost always need a DPIA if your monitoring falls into these scenarios:
- Continuous tracking of employees’ online activity, emails, or movements across the entire workforce triggers the DPIA requirement.
- Tools that scan faces, fingerprints, or keystrokes, or algorithms that score productivity, raise significant privacy and fairness concerns, demanding a DPIA.
- If monitoring captures sensitive data like health, union membership, or religious beliefs (even indirectly), the risks are heightened, and a DPIA becomes essential.
- Deploying new, intrusive tech, like always-on webcam monitoring, GPS trackers, or emotion-recognition software, falls squarely into the “high risk” category.
Steps to Conduct a DPIA
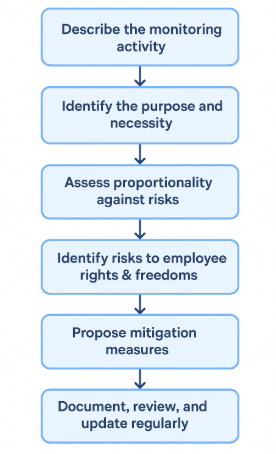
A DPIA doesn’t have to be intimidating. Think of it as a structured checklist for doing monitoring responsibly and defensibly. Here’s how to approach it:
Describe the monitoring activity
What exactly are you doing? Spell out the type of monitoring (e.g., keystroke logging, GPS tracking) and how it works.
Identify the purpose and necessity
Why are you doing this? Is it to protect sensitive data, ensure employee productivity, or meet legal obligations? Be specific and honest.
Assess proportionality against risks
Does the benefit of monitoring outweigh the intrusion into employee privacy? Could a less invasive method achieve the same goal?
Identify risks to employee rights & freedoms
Think worst-case: Could the data be misused? Could employees feel unfairly targeted, discriminated against, or constantly under pressure?
Propose mitigation measures
List the safeguards you’ll put in place: data minimization, anonymization, access controls, retention limits, and clear employee communications.
Consult employees/unions where required
In some jurisdictions (like Germany or France), consultation with employee representatives is mandatory. Even where it isn’t, involving staff builds trust.
Document, review, and update regularly
A DPIA isn’t a one-time box-tick. Keep records, revisit them when the technology changes, and update whenever the monitoring scope expands.
Protecting Employee Privacy During Monitoring
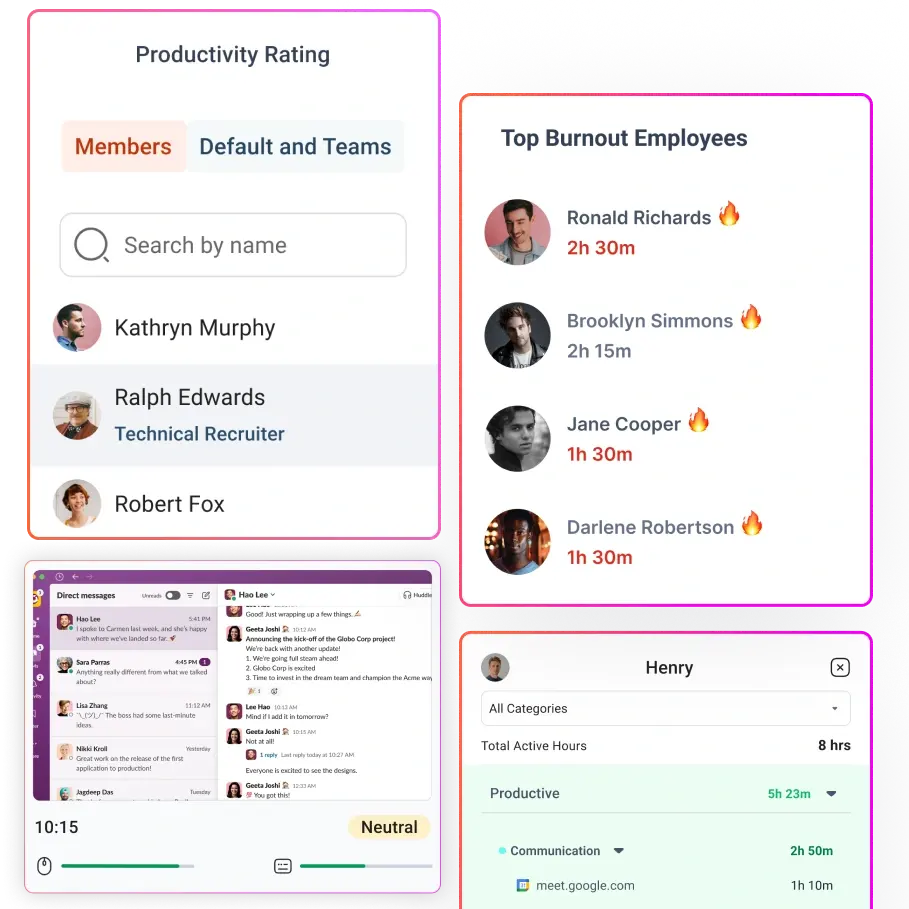
Even when monitoring is legal, how it’s implemented makes all the difference. Employers can protect privacy, build trust, and stay compliant by focusing on three key areas: data minimization, privacy-preserving technology, and transparency.
Data Minimization Strategies
The less data you collect, the lower your risks. Smart monitoring focuses only on what’s necessary:
- Monitor only business-related activities: Keep tracking tied strictly to work, no peeking into personal browsing or private chats.
- Restrict monitoring to work hours: Surveillance should end when the workday does; off-duty tracking is rarely justifiable.
- Avoid monitoring personal devices: If employees use their own phones or laptops, separate work from personal life with clear boundaries.
- Role-based access to monitoring data: Not everyone in management needs to see raw monitoring data; limit access to only those who truly need it.
Privacy-Preserving Technologies
Technology can help balance oversight with respect for privacy:
- Anonymization and pseudonymization: Remove or mask identifiers so data can’t be traced back to specific individuals unless absolutely required.
- Aggregated vs. individual reports: Use group-level insights (team productivity trends) instead of tracking each person minute-by-minute.
- Strong encryption (in transit and at rest): Secure monitoring of data at every stage to prevent leaks or unauthorized access.
- Automatic deletion schedules: Don’t hold onto data longer than necessary; set systems to purge records once their purpose is served.
Transparency and Accountability
Employees are far more likely to accept monitoring when it’s done openly and fairly:
- Clear and accessible privacy notices: Spell out what’s being monitored, why, and how the data will be used, in plain language.
- Regular policy updates and acknowledgment: Refresh policies as tools or employee monitoring laws change, and have employees confirm they understand them.
- Training employees on their rights: Awareness reduces fear, teach staff about their rights under GDPR, CCPA, or local laws.
- Establishing complaint and redress mechanisms: Provide a clear way for employees to raise concerns and ensure issues are addressed quickly.
Managing Employee Consent and Rights
Consent vs. Legitimate Interest
- Why legitimate interest is usually preferred: In workplace monitoring, consent isn’t truly “free” because of the employer–employee power imbalance. Regulators, therefore, view legitimate interest as the stronger and safer legal basis.
- When employee consent may still apply: Consent can work for very specific, optional monitoring (e.g., voluntary wellness programs, BYOD scenarios).
- Procedures for valid consent collection: Must be clear, informed, specific, and documented—no pre-ticked boxes or vague clauses.
- Handling consent withdrawal: Employees must be able to withdraw consent at any time, and monitoring must stop immediately without penalty.
Employee Rights Management Procedures
- Responding to access requests efficiently: Set up internal workflows to quickly provide employees with copies of their monitoring data.
- Implementing rectification and deletion requests: Correct errors promptly and delete data that’s excessive, outdated, or no longer needed.
- Supporting data portability: Where applicable, provide structured, machine-readable data if employees request portability.
- Handling objections and grievances: Create clear channels for employees to challenge monitoring practices and ensure responses are timely and fair.
- Ongoing rights awareness training: Educate managers and staff regularly so both sides understand rights and obligations under privacy law.
Sector-Specific Data Protection Requirements
Healthcare
HIPAA compliance in employee monitoring
In the U.S., HIPAA sets strict rules around access to Protected Health Information (PHI). Monitoring tools must never expose patient data unnecessarily, and audit trails are essential to prove that only authorized staff accessed medical records.
Protecting medical records during monitoring
For healthcare employers, even small missteps, like storing keystroke logs that capture login credentials, can create massive liabilities. Monitoring must be configured to shield sensitive fields, anonymize data where possible, and tightly control who can view logs.
Telehealth and remote work privacy concerns
With telehealth booming, monitoring extends beyond hospitals into employees’ homes. Employers must ensure remote monitoring tools don’t accidentally capture personal surroundings, family interactions, or private communications beyond the clinical context. Encryption, device management, and strict purpose limitation become critical safeguards.
Financial Services
SOX compliance and audit documentation
The Sarbanes-Oxley Act (SOX) requires firms to maintain accurate records for auditing. Monitoring tools can help capture activity logs and user actions, but these records must be secure, tamper-proof, and retained only for lawful periods.
PCI-DSS considerations for payment data
Any employee handling cardholder data falls under PCI-DSS. Monitoring here must prevent accidental logging of credit card details in screenshots, recordings, or logs. Tools should be configured to mask sensitive payment fields automatically.
Insider trading prevention and risk management
Trading firms often monitor communications to detect suspicious patterns and prevent insider trading. This monitoring is legal but highly sensitive, it must be proportionate, well-documented, and often integrated with advanced surveillance systems that flag risks without over-collecting employee personal data.
Government & Defense Contractors
Federal data security and clearance rules
Agencies and contractors handling classified or sensitive information face some of the strictest monitoring obligations. Access must be logged, actions traceable, and data monitored for potential leaks or breaches. Non-compliance isn’t just a fine, it can mean loss of clearance or contracts.
Restrictions on cross-border data transfers
Sensitive defense or government data often cannot legally leave national borders. Monitoring solutions must therefore ensure data storage and processing stay local, with clear geo-fencing and cloud restrictions in place.
Monitoring requirements under government contracts
Many contracts explicitly mandate monitoring of employee activity, system access, and data flows as part of security certification. However, monitoring still must respect employee rights under local labor laws, meaning agencies need to strike a fine balance between security demands and privacy principles.
Data Breach Prevention and Incident Response
When it comes to employee monitoring, the collected data itself becomes a sensitive asset. If that data is leaked, mishandled, or stolen, the consequences are severe: loss of employee trust, regulatory fines, lawsuits, and reputational damage. That’s why preventing breaches and preparing for incidents is just as important as monitoring in the first place.
Preventive Security Measures
Strong authentication and access controls
Monitoring data should never be accessible to just anyone. Multi-factor authentication (MFA), strict role-based access, and periodic access reviews help ensure that only the right people, like HR or compliance officers, can view logs and reports.
Vendor and third-party risk management
Many monitoring solutions are SaaS platforms, which means employee data flows through third-party vendors. Employers must vet vendors carefully, review their security certifications (ISO 27001, SOC 2, etc.), and include contractual safeguards for data handling.
Regular security testing and audits
Just as IT systems get penetration-tested, monitoring platforms should undergo routine audits. This includes checking for unpatched vulnerabilities, misconfigurations, and weak encryption protocols that could expose data.
Secure data handling training for admins
Even the best technology can fail if people mishandle data. Administrators should be trained on secure export procedures, how to share reports safely, and how to spot phishing attempts that could compromise monitoring systems.
Breach Response Procedures
Even with strong defenses, no system is invulnerable. A well-prepared incident response plan ensures that if a breach happens, damage is minimized, and compliance obligations are met.
Rapid detection and containment steps
Every extra hour a breach goes unnoticed increases its impact. Companies need monitoring alerts, intrusion detection systems, and clear protocols to isolate compromised accounts or systems immediately.
Assessing impact and affected data scope
Once a breach is contained, the next step is understanding what was accessed, whether it was login credentials, monitoring logs, or screenshots. This helps gauge both the regulatory exposure and employee impact.
Notification requirements (GDPR 72-hour rule)
Under GDPR, organizations must notify regulators within 72 hours of becoming aware of a breach. If the breach affects employees directly, timely communication with them is also mandatory. Other jurisdictions (like U.S. state laws) may impose their own deadlines.
Communicating with affected employees
Transparency is critical. Employees should be told what happened, what data was compromised, and what steps they should take (such as changing passwords or enabling MFA). A vague or delayed message risks losing all trust.
Post-incident reviews and lessons learned
Once the dust settles, organizations must conduct a root-cause analysis: How did the breach happen? Could monitoring tools have been configured differently? What policies failed? These lessons should feed into updated security controls, employee training, and vendor contracts.
Best Practices Checklist for 2025
- Conduct a Data Protection Impact Assessment (DPIA) before implementing monitoring.
- Limit monitoring to what’s necessary, both in scope and data collected.
- Clearly document your legal basis and decision-making process.
- Keep employee policies and privacy notices up to date.
- Provide compliance training for managers and employees.
- Review employee monitoring practices regularly to confirm ongoing necessity.
- In complex or cross-border cases, consult legal counsel for guidance.
- Use privacy-preserving technologies like anonymization, pseudonymization, and encryption.
- Maintain an incident response plan for data breaches or unauthorized access.
- Conduct vendor due diligence for any third-party monitoring tools.
- Regularly test monitoring systems for security vulnerabilities
- Avoid monitoring personal devices or off-work activities unless strictly necessary
Frequently Asked Questions (FAQs)
Is employee monitoring data protection required by law?
Yes, under GDPR Article 5 and equivalent global laws.
What legal basis should employers use for monitoring?
Most use legitimate interests, but balancing tests are required.
Do employees have the right to refuse monitoring?
They can object, but employers may proceed if the legitimate interest outweighs.
What happens if monitoring violates laws?
Fines up to €20M or 4% of global turnover, plus reputational harm
Conclusion
In 2025, compliance with employee monitoring laws is a business survival skill. The stakes are high: fines, lawsuits, and reputational damage on one side; employee trust, productivity, and resilience on the other. Companies that approach monitoring transparently and responsibly don’t just avoid risk, they gain a competitive edge by proving they value privacy as much as performance.
The next steps are clear: conduct DPIAs, train your people, document your decisions, and seek expert guidance when in doubt. Done right, monitoring becomes a tool for protection and growth, not conflict.
Sign up for Flowace’s 7-day free trial today!